Building a Secure Software Fortress: Mastering DevSecOps
This listicle delivers eight key DevSecOps best practices to fortify your software development. Learn how to integrate security seamlessly into your development lifecycle, transforming it from a bottleneck to a continuous enhancement. These practices are crucial for building user trust and ensuring operational resilience. Mastering these DevSecOps best practices will help you create robust application security in 2025 and beyond. From automated security scanning to security chaos engineering, we’ll cover essential techniques to strengthen your security posture.
1. Implement Automated Security Scanning in CI/CD Pipeline
One of the most crucial DevSecOps best practices is integrating automated security scanning directly into your Continuous Integration/Continuous Delivery (CI/CD) pipeline. This “shift-left” approach embeds security checks early in the development lifecycle, transforming security from a reactive afterthought to a proactive, integral component of the development process. By catching vulnerabilities and compliance violations before they reach production, organizations can significantly reduce risks and remediation costs.
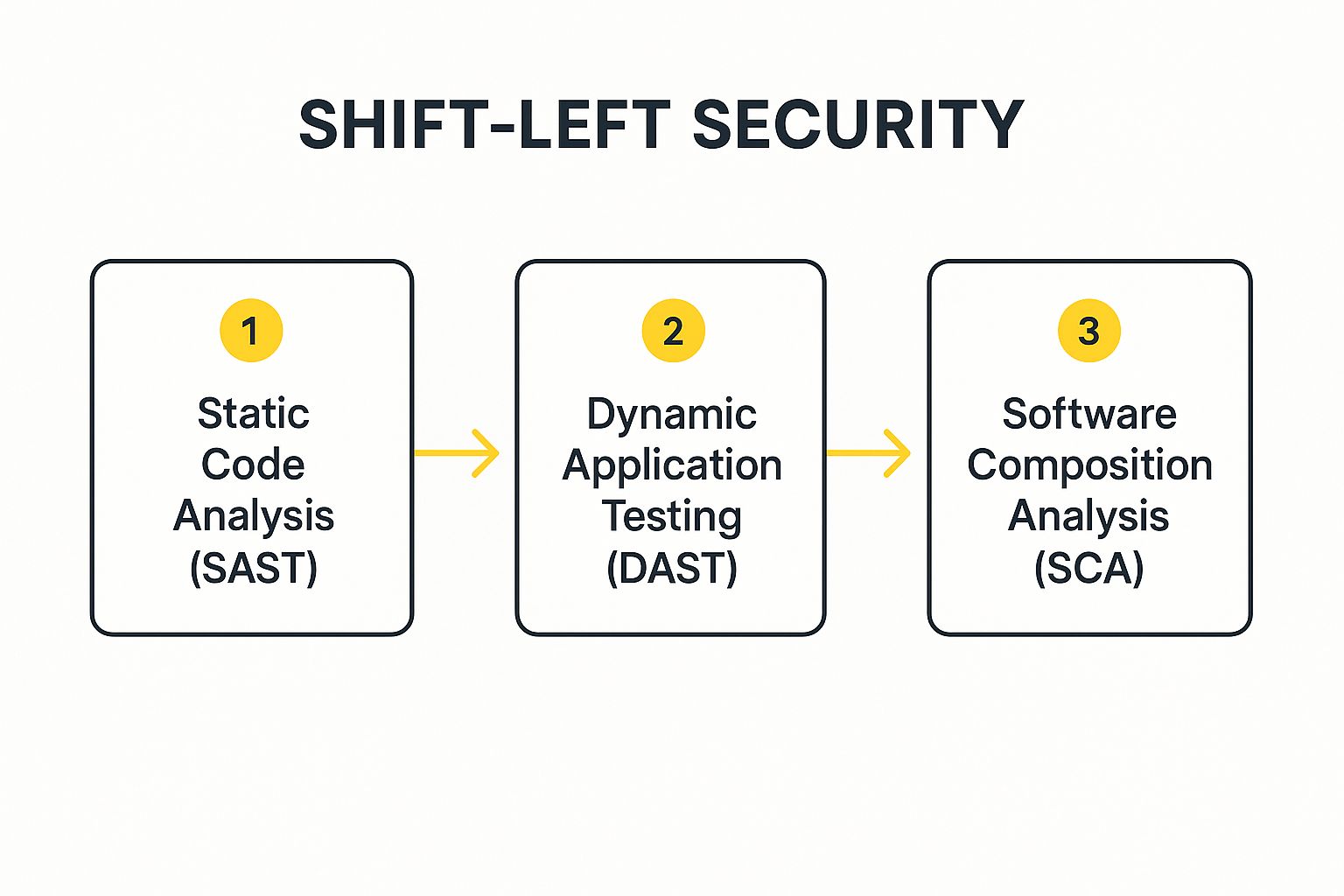
The infographic above illustrates a typical workflow for automated security scanning within a CI/CD pipeline. The process begins with the developer committing code changes. Then, various automated security scanning tools are triggered as part of the build process, including SAST for analyzing source code, DAST for testing running applications, SCA for checking dependencies, and container and IaC scanning. If a vulnerability is detected, the build fails, and the developer is notified. This immediate feedback loop ensures that security issues are addressed quickly and efficiently. The final step represents a successful build and deployment after security checks have passed. The sequential nature of this workflow highlights the importance of integrating security at each stage, preventing vulnerable code from progressing through the pipeline.
This automated approach utilizes various security scanning tools to cover different aspects of your application and infrastructure:
- SAST (Static Application Security Testing): Analyzes source code for vulnerabilities without executing the application.
- DAST (Dynamic Application Security Testing): Examines running applications for security issues, simulating real-world attacks.
- SCA (Software Composition Analysis): Scans third-party libraries and dependencies for known vulnerabilities.
- Container Scanning: Checks container images for vulnerabilities and misconfigurations.
- Infrastructure as Code (IaC) Scanning: Validates infrastructure templates for security best practices.
Why implement automated security scanning in your CI/CD pipeline?
This practice is essential for several reasons. It ensures consistent and repeatable security checks with each build, reducing human error and increasing efficiency. Early detection of security issues translates to significant cost savings in remediation efforts. Furthermore, integrating security into the development workflow fosters a security-conscious culture among developers.
Pros:
- Early detection of security issues, saving time and reducing remediation costs.
- Consistent and repeatable security checks.
- Reduced human error in security testing.
- Creates security awareness among developers.
- Prevents vulnerable code from reaching production.
Cons:
- Can generate false positives requiring manual review.
- Initial setup can be time-consuming.
- Requires regular maintenance and updates of security tools.
- May slow down the pipeline if not optimized properly.
Examples of Successful Implementation:
Organizations like GitHub, Netflix, and Capital One have embraced automated security scanning in their DevOps practices, demonstrating its effectiveness in enhancing security posture. For instance, GitHub utilizes GitHub Advanced Security for all its repositories. Learn more about Implement Automated Security Scanning in CI/CD Pipeline
Actionable Tips:
- Start with critical security checks and gradually expand coverage.
- Define appropriate security gates and thresholds for blocking builds.
- Use policy-as-code tools like OPA (Open Policy Agent) to define security policies.
- Integrate results into developer tools and dashboards for visibility.
- Implement parallel security scanning to minimize pipeline delays.
This video provides further insights into implementing automated security scanning.
This DevSecOps best practice, popularized by organizations like OWASP and Google’s DORA team, is crucial for building secure and reliable software in today’s fast-paced development environment. By automating security, organizations can proactively address vulnerabilities, reduce risks, and ultimately deliver higher-quality software.
2. Threat Modeling as Code
Threat Modeling as Code is a crucial DevSecOps best practice that shifts the traditional, manual, and documentation-heavy threat modeling process to an automated, code-driven approach. This evolution allows teams to define potential security threats and their corresponding mitigations in a machine-readable format. This structured approach ensures security is systematically addressed throughout the application lifecycle, making it a key component of robust DevSecOps pipelines. By integrating threat modeling directly into the development workflow, organizations can proactively identify and mitigate security risks, fostering a security-first culture.
Instead of relying on static documents, Threat Modeling as Code utilizes structured formats like YAML or JSON to represent threat models. This allows for version control integration, enabling teams to track changes, collaborate effectively, and maintain a clear history of security considerations. Moreover, this codified approach enables automated validation of security controls against identified threats, providing continuous feedback and ensuring alignment with security requirements.
How it Works:
Threat Modeling as Code works by defining threat models using a structured language that describes the application architecture, potential threats, and their mitigations. This machine-readable format enables integration with various DevSecOps tools and processes. Here’s a general workflow:
- Define the Application Architecture: Represent the application components and their interactions in a structured format.
- Identify Potential Threats: Use established methodologies like STRIDE or DREAD to systematically identify potential threats to the application.
- Specify Mitigations: Define the security controls and mitigations in place to address the identified threats.
- Automate Validation: Integrate the threat model into the CI/CD pipeline to automatically validate the security controls and identify potential vulnerabilities.
- Generate Documentation: Use the code-based threat model to generate reports, visualizations, and other documentation.
Features and Benefits:
- Machine-readable threat models: Enables automation and integration with other tools.
- Version control integration: Tracks changes and provides a history of security decisions.
- Automated validation of security controls: Ensures consistency and compliance.
- Integration with CI/CD pipelines: Facilitates continuous threat assessment.
- Automated documentation generation: Simplifies reporting and communication.
Examples of Successful Implementation:
- Microsoft’s Threat Modeling Tool: Provides a foundation for automating aspects of threat modeling.
- IriusRisk: Offers a threat modeling platform that integrates with CI/CD pipelines.
- Netflix’s automated threat modeling: A prominent example of applying this approach to a microservices architecture.
Pros:
- Repeatable and scalable: Makes threat modeling consistent across multiple projects.
- Living documentation: The threat model evolves with the application.
- Automated validation: Enhances security posture and reduces manual effort.
- Improved collaboration: Bridges the gap between security and development teams.
- Testable threat models: Allows for validation and verification like any other code.
Cons:
- Learning curve: Requires familiarity with threat modeling concepts and tools.
- Tooling and integration: May necessitate custom integrations or specialized tooling.
- Risk of tool focus: It’s crucial to prioritize analysis over simply using the tools.
- Limitations of codification: Not all threats are easily represented in code.
Actionable Tips:
- Start with STRIDE or DREAD: These methodologies provide a structured approach to threat identification.
- Utilize threat modeling DSLs: Languages like pytm or threagile can simplify the process.
- Integrate with issue tracking: Ensure identified threats are addressed and tracked.
- Prioritize high-risk areas: Focus on critical components and vulnerabilities first.
- Regular validation: Continuously validate the threat model against the evolving architecture.
When and Why to Use This Approach:
Threat Modeling as Code is particularly valuable in Agile and DevOps environments where rapid development cycles and continuous integration/continuous delivery (CI/CD) pipelines are prevalent. It enables security to be integrated seamlessly into the development process, ensuring that security considerations are addressed proactively and consistently. This approach is ideal for organizations looking to scale their threat modeling efforts, improve collaboration between security and development teams, and automate security validation. By embedding security into the development lifecycle, organizations can build more secure and resilient applications.
3. Infrastructure as Code Security
Infrastructure as Code (IaC) Security is a crucial DevSecOps best practice that focuses on securing the very foundation of your applications: the infrastructure. Instead of manually configuring servers, networks, and databases, IaC defines and provisions infrastructure through code, allowing you to manage and provision your infrastructure in a safe, repeatable, and predictable manner. This approach treats infrastructure configuration as software, enabling you to scan, test, and validate for security issues before deployment, preventing insecure configurations from ever reaching production environments. This proactive approach significantly strengthens your overall security posture and is a key component of implementing DevSecOps best practices.

IaC security leverages various tools and techniques to achieve its objectives. These include pre-deployment scanning of infrastructure templates (like Terraform, CloudFormation, or Azure Resource Manager templates) for security misconfigurations, enforcing security policies for infrastructure using policy-as-code tools, and implementing drift detection to identify any unauthorized infrastructure changes that deviate from the defined code. Secure secret management for infrastructure credentials is also paramount, as is adopting immutable infrastructure patterns that minimize the attack surface by deploying fresh instances rather than patching existing ones.
This approach offers significant advantages for scrum masters, agile coaches, software development teams, and IT operations departments alike. By preventing insecure infrastructure configurations before deployment, IaC security ensures consistent security controls across all environments (development, testing, staging, and production). It enables auditability of infrastructure changes through version control, reducing manual configuration errors that could lead to security vulnerabilities. Furthermore, it facilitates compliance through codified security policies, a crucial aspect for organizations operating in regulated industries. For example, Hashicorp uses Sentinel policy-as-code to enforce security policies in Terraform configurations, while AWS’s CloudFormation Guard provides policy-based validation for CloudFormation templates. Tools like Chef InSpec further empower teams to codify infrastructure security and compliance requirements. You can learn more about Infrastructure as Code Security to see how security concerns are addressed even in specific API contexts.
While IaC security offers numerous benefits, it also presents some challenges. It requires additional tooling and expertise, and integrating legacy infrastructure can be difficult. Security policies must be continuously updated to address new threats, and it’s important to note that IaC security may not catch all runtime security issues, necessitating complementary security measures.
To successfully implement IaC security, consider these tips: implement infrastructure linting early in the development process; use pre-commit hooks to catch security issues before they enter version control; define infrastructure security baselines as code; implement least privilege principles in all infrastructure roles and permissions; and regularly audit and rotate infrastructure credentials. These practices, championed by organizations and individuals like Hashicorp (creators of Terraform), the AWS Cloud Development Kit (CDK) team, Bridgecrew (creators of Checkov, an IaC security scanner), and Kief Morris (author of ‘Infrastructure as Code’), are essential for building a robust and secure infrastructure.
By embracing IaC security as a core DevSecOps best practice, organizations can proactively address infrastructure security risks, improve compliance, and build a more secure and resilient foundation for their applications.
4. Immutable Security with Container Orchestration
Immutable Security with Container Orchestration is a crucial DevSecOps best practice that enhances the security posture of containerized applications. It combines the principles of immutable infrastructure with container security, leveraging orchestration platforms like Kubernetes to enforce strict security controls. This approach treats containers as immutable artifacts—deployed entities that are never modified after creation. Instead of patching or updating a running container, a new, updated container image is built, deployed, and replaces the old one. This eliminates the risks associated with mutable infrastructure, ensuring consistent security policies and reducing the potential attack surface.

This method fundamentally shifts how security is managed in containerized environments. By deploying only pre-approved and scanned images, organizations can minimize the risk of vulnerabilities and ensure that all running containers adhere to established security standards. Automated processes within the container orchestration platform facilitate this workflow, making security a core part of the deployment pipeline. This is a key component of DevSecOps, integrating security practices seamlessly into the development and operations lifecycle.
Features that enable Immutable Security with Container Orchestration include:
- Read-only container file systems: Preventing runtime modifications helps to maintain the integrity of the container image and reduces the risk of malware persistence.
- Automated container image scanning: Scanning images in registries and at runtime identifies vulnerabilities before they can be exploited.
- Network policies: Restricting container communications through network policies enforces a zero-trust security model, limiting the blast radius of potential breaches.
- Pod security policies/admission controllers: These enforce security standards and prevent the deployment of non-compliant containers.
- Runtime security monitoring: This detects anomalous container behavior, providing early warning of potential security incidents.
- Service mesh integration: Secure service-to-service communication within the orchestrated environment enhances overall application security.
Pros:
- Reduced attack surface: Prevents live patching and unauthorized modifications, minimizing vulnerabilities.
- Consistent security controls: Ensures standardized security across development, testing, and production environments.
- Automated remediation: Facilitates rapid and automated remediation through container replacement.
- Supports zero-trust security: Enables granular control over container interactions, aligning with modern security best practices.
Cons:
- Learning curve: Teams new to containers and orchestration may require training and upskilling.
- CI/CD pipeline complexity: Requires robust CI/CD pipelines for efficient container rebuilds and deployments.
- Resource utilization: Frequent container replacements can potentially increase resource consumption.
- Legacy application challenges: Some legacy applications may be difficult to containerize securely.
Examples:
- Google Kubernetes Engine (GKE) leverages Binary Authorization to enforce container image security policies before deployment.
- Monzo Bank uses Kubernetes with stringent security policies to manage its complex microservices architecture.
- Red Hat OpenShift provides enterprise-grade security features for container orchestration, including enhanced access controls and security auditing.
Tips for Implementing Immutable Security:
- Use minimal base images: Opt for distroless or Alpine Linux to minimize the attack surface.
- Implement zero-trust networking: Employ default-deny network policies to restrict container communication.
- Principle of least privilege: Never run containers as root; utilize user namespaces and non-root users.
- Runtime security monitoring: Implement container runtime security tools like Falco or Aqua Security.
- Automated vulnerability response: Establish automated workflows for addressing critical security vulnerabilities.
Immutable Security with Container Orchestration is a vital DevSecOps practice for modern software development, offering a proactive and robust approach to securing containerized applications. Popularized by industry leaders like Kelsey Hightower and Liz Rice, as well as organizations like the CNCF, Docker, Inc., and the Kubernetes community, this approach provides a scalable and efficient way to manage security throughout the container lifecycle, making it an essential best practice for any organization adopting containerization.
5. Continuous Compliance as Code
Continuous Compliance as Code (CCaC) is a crucial DevSecOps best practice that shifts compliance from a periodic, manual process to an automated, continuous one. It bakes security and compliance validations directly into the development lifecycle, treating compliance requirements just like any other piece of code. This allows organizations to ensure their systems adhere to industry and regulatory standards like GDPR, HIPAA, PCI-DSS, and SOX, not just at audit time, but at all times. This proactive approach is essential for maintaining a strong security posture and avoiding costly penalties.
Instead of relying on time-consuming and potentially error-prone manual audits, CCaC codifies compliance requirements. These codified requirements are then automatically checked throughout the development and deployment pipeline, providing continuous visibility into compliance status. This allows teams to catch and remediate compliance drifts early, preventing non-compliant changes from reaching production.
How Continuous Compliance as Code Works
CCaC leverages several key features to automate and streamline compliance:
- Codified Compliance Requirements: Compliance rules are translated into machine-readable code, allowing for version control and automated execution.
- Automated Compliance Scanning: Automated scans are integrated into the CI/CD pipeline, checking for compliance violations at every stage.
- Real-time Compliance Dashboards and Reporting: Dashboards provide real-time insights into the compliance status of systems and applications.
- Compliance Drift Detection and Automated Remediation: CCaC can automatically detect deviations from compliance baselines and even trigger automated remediation actions.
- Evidence Collection Automation: The process automatically gathers evidence of compliance, simplifying audit preparation.
- Policy-as-Code: Compliance policies are defined and managed as code, enabling consistent enforcement and automated updates.
Examples of Continuous Compliance as Code in Action
Several organizations have successfully implemented CCaC to improve their security posture and streamline compliance efforts:
- Capital One uses compliance-as-code to maintain continuous PCI-DSS compliance for its financial systems.
- Intuit has implemented automated compliance checks for SOX and other regulations.
- Microsoft utilizes Azure Policy for continuous compliance across its cloud resources.
These examples demonstrate how CCaC can be applied across various industries and regulatory frameworks.
Actionable Tips for Implementing Continuous Compliance as Code
- Map Compliance Controls to Specific Code Checks and Tests: Clearly define how each compliance control translates into a specific code check or test.
- Implement Compliance Gates in Deployment Pipelines: Prevent deployments if compliance checks fail.
- Use Tools like InSpec, OPA, or AWS Config for Compliance Automation: Leverage existing tools to automate compliance checks and enforcement.
- Create Developer-Friendly Documentation: Provide developers with clear and concise documentation explaining the compliance requirements and how they are implemented in code.
- Automatically Generate Compliance Reports for Auditors: Streamline the audit process by automatically generating the necessary reports.
When and Why to Use Continuous Compliance as Code
CCaC is particularly beneficial for organizations that:
- Operate in highly regulated industries (e.g., finance, healthcare).
- Manage complex and evolving compliance requirements.
- Seek to improve their security posture and reduce risk.
- Aim to streamline and automate their compliance processes.
For Scrum Masters, Agile Coaches, Software Development teams, and Project Managers, CCaC provides the ability to integrate compliance directly into the development workflow, fostering a “shift-left” approach to security. For Enterprise IT and Operations departments, CCaC offers continuous visibility and control over compliance, reducing manual overhead and improving efficiency. Learn more about Continuous Compliance as Code.
Pros and Cons of Continuous Compliance as Code
Pros:
- Reduced manual compliance verification effort
- Continuous visibility into compliance status
- Prevention of non-compliant changes from reaching production
- Simplified audit processes with automated evidence collection
- Empowers developers to understand compliance requirements in context
Cons:
- Initial effort to translate compliance requirements into code
- May require specialized expertise in both compliance and coding
- Some compliance requirements may be difficult to fully automate
- Requires regular updates as regulations change
By integrating compliance directly into the development process, Continuous Compliance as Code strengthens your DevSecOps posture, allowing you to deliver secure and compliant software consistently and efficiently. Platforms popularized by companies like Chef (with InSpec), HashiCorp (with Sentinel), and organizations like the Center for Internet Security (CIS) and Coalfire offer powerful tooling to achieve this.
6. Security Chaos Engineering
Security Chaos Engineering (SCE) is a crucial DevSecOps best practice that proactively identifies vulnerabilities in your systems by deliberately injecting controlled security failures and simulated attacks. This approach allows teams to observe how their systems respond under pressure, improve detection and response mechanisms, and build more robust recovery processes before real attackers exploit weaknesses in production environments. By embracing the “break things on purpose” philosophy within a controlled environment, organizations can significantly enhance their overall security posture. This makes it a valuable addition to any DevSecOps strategy.
How it Works:
SCE applies the principles of chaos engineering to the realm of security. Instead of random infrastructure failures, SCE focuses on simulated security incidents. These range from injecting malicious code into CI/CD pipelines to simulating denial-of-service attacks or exploiting potential misconfigurations. The goal is to understand the system’s reaction to these events, identify weaknesses, and improve resilience.
Features of Security Chaos Engineering:
- Controlled security fault injection: Introduce specific security failures, such as expiring certificates or injecting malicious code, in a controlled manner.
- Attack simulation in production-like environments: Mimic real-world attacks to assess the effectiveness of your security defenses.
- Game days for security incident response training: Conduct simulated incident response exercises to train teams and refine their response plans.
- Automated security chaos experiments in CI/CD pipelines: Integrate security chaos testing into your automated workflows for continuous security validation.
- Validation of security monitoring and alerting effectiveness: Ensure that security monitoring tools and alerts function as expected during simulated attacks.
Pros:
- Identifies unknown security weaknesses and blind spots: Uncovers vulnerabilities that traditional security testing might miss.
- Improves security incident response through practice: Provides valuable hands-on experience in handling security incidents.
- Validates the effectiveness of security controls in real conditions: Tests security controls under realistic attack scenarios.
- Builds security resilience into systems by design: Encourages a proactive approach to security by identifying and mitigating weaknesses early.
- Develops a proactive security mindset across teams: Promotes a culture of security awareness and shared responsibility.
Cons:
- Requires careful planning to avoid unintended consequences: Thorough planning and risk assessment are essential to prevent disruptions to production systems.
- May require specialized tools and expertise: Implementing SCE effectively may necessitate specialized tools and skilled security professionals.
- Needs strong executive support due to perceived risks: Gaining buy-in from leadership is critical due to the potential for disrupting systems.
- Can be resource-intensive to implement properly: Setting up and running SCE experiments can require significant time and resources.
Examples of Successful Implementation:
- Netflix’s Chaos Monkey: Originally designed for infrastructure resilience, Chaos Monkey has evolved to include security-focused failure testing.
- AWS Security Hub: Provides continuous compliance checks as a form of automated security verification, aligning with the principles of SCE.
- Shopify: Conducts regular security game days to test incident response capabilities and improve preparedness.
- Google’s Project Zero: Proactively tests security boundaries in controlled ways to identify and report vulnerabilities.
Actionable Tips for Implementing Security Chaos Engineering:
- Start small and controlled: Begin with non-production environments before moving to production.
- Define clear blast radius constraints: Limit the scope of experiments to minimize potential impact.
- Create a security hypothesis for each experiment: Define clear objectives and measurable outcomes for each test.
- Automate security chaos tests: Integrate SCE into your CI/CD pipeline for continuous security validation.
- Document findings and improvements: Track the results of experiments and document any identified weaknesses and subsequent improvements.
When and Why to Use Security Chaos Engineering:
SCE is particularly beneficial for organizations that prioritize proactive security and want to move beyond traditional security testing methods. It is ideal for:
- Highly regulated industries: Where robust security posture is critical.
- Organizations with complex systems: Where identifying vulnerabilities can be challenging.
- Teams adopting DevSecOps: SCE complements and enhances DevSecOps practices.
By implementing Security Chaos Engineering as a DevSecOps best practice, organizations can proactively identify and mitigate security vulnerabilities, build more resilient systems, and improve their overall security posture. While it requires careful planning and execution, the benefits of SCE far outweigh the risks for organizations striving for a robust security posture in today’s dynamic threat landscape. This proactive approach is no longer a luxury but a necessity for organizations looking to stay ahead of emerging threats.
7. Automated Security Guardrails
Automated Security Guardrails are a crucial DevSecOps best practice, acting as preventive controls that are programmatically enforced throughout the software development lifecycle (SDLC). Unlike traditional security gates that can halt progress, guardrails guide development teams toward secure coding practices and infrastructure configurations, allowing them to maintain velocity while operating within defined security boundaries. This approach helps strike a balance between robust security requirements and the need for rapid development cycles, a key challenge in today’s fast-paced software world. This makes them a vital component of any successful DevSecOps strategy.
How Automated Security Guardrails Work:
These guardrails function by embedding security checks and enforcement mechanisms directly into the development and deployment pipeline. They work proactively to identify and prevent security misconfigurations and policy violations before they reach production. This is achieved through a combination of features, including:
- Self-service security policies: Developers can apply pre-approved security policies to their projects without needing to involve security teams for every decision.
- Just-in-time permission elevation: When elevated permissions are required, automated workflows can approve requests quickly, minimizing delays while maintaining control.
- Pre-approved secure patterns and templates: Providing developers with readily available secure building blocks ensures consistency and reduces the likelihood of introducing vulnerabilities.
- Automated remediation of common security issues: Guardrails can automatically fix common security problems, such as misconfigured cloud storage or insecure dependencies.
- Developer-friendly security feedback mechanisms: Clear, actionable feedback integrated into the developer workflow helps teams learn from mistakes and improve security practices.
- Preventive controls that stop high-risk actions: For critical security violations, guardrails can block actions that pose an immediate threat, acting as a last line of defense.
Examples of Successful Implementation:
Several organizations and platforms leverage automated security guardrails effectively. For example, AWS implements Service Control Policies to establish guardrails across organizations, preventing actions that could compromise security. Salesforce’s Heroku Shield provides guardrails specifically for application development, while Google Cloud’s Organization Policy Service enforces security policies at scale. Learn more about Automated Security Guardrails to see practical examples of implementation. Even internally, companies like Intuit have developed automated guardrail systems to prevent common AWS misconfigurations, showcasing the adaptability of this approach.
Why Use Automated Security Guardrails?
This DevSecOps best practice is particularly beneficial because it shifts security left, integrating it seamlessly into the development process. This approach is essential for Scrum Masters, Agile Coaches, Software Development and Engineering Teams, Project and Product Managers, Remote and Cross-functional Teams, and Enterprise IT and Operations Departments alike, as it allows them to:
- Reduce friction between security and development teams: By empowering developers to manage security within defined boundaries, guardrails minimize the need for constant back-and-forth with security teams.
- Prevent common security mistakes before they happen: Proactive prevention is always better than reactive remediation. Guardrails stop vulnerabilities from being introduced in the first place.
- Enable faster development within secure boundaries: By guiding rather than blocking, guardrails allow developers to move quickly without sacrificing security.
- Scale security expertise through automation: Automated guardrails extend the reach of security teams, ensuring consistent enforcement even as development teams and projects grow.
- Provide consistent security enforcement across projects: Guardrails ensure that security policies are applied uniformly across all projects, reducing inconsistencies and vulnerabilities.
Pros and Cons:
While automated security guardrails offer significant advantages, it’s important to be aware of the potential drawbacks:
Pros: (as outlined above)
Cons:
- Can be complex to implement across diverse technology stacks: Integrating guardrails into a heterogeneous environment can be challenging.
- Requires ongoing maintenance as security requirements evolve: Guardrails must be updated regularly to stay effective against emerging threats and changing best practices.
- May not catch all classes of security issues: Guardrails are most effective against known and predictable issues; they may not catch novel or sophisticated attacks.
- Initial setup can require significant investment: Implementing automated guardrails requires time, resources, and expertise.
Tips for Implementation:
- Start with high-impact, common security issues to prevent: Focus on the most critical vulnerabilities first to maximize the impact of your guardrails.
- Design guardrails that guide rather than just block: Provide clear explanations and remediation instructions to help developers learn from security violations.
- Provide clear remediation instructions when violations occur: Make it easy for developers to fix issues quickly and efficiently.
- Implement exception processes for legitimate edge cases: Recognize that there will be times when deviations from standard security practices are necessary.
- Measure both prevention effectiveness and developer experience: Track the success of your guardrails in preventing vulnerabilities and the impact on developer workflow.
By incorporating automated security guardrails into your DevSecOps strategy, you can build a more secure and resilient development process while empowering development teams to move quickly and efficiently.
8. Shift-Right Security Monitoring and Feedback Loops
Shift-Right Security Monitoring and Feedback Loops represent a crucial DevSecOps best practice, focusing on continuous security monitoring and improvement after applications and infrastructure are deployed into production. This approach complements the “shift-left” focus on integrating security earlier in the development lifecycle, creating a holistic security strategy. While shift-left aims to prevent vulnerabilities from entering the codebase, shift-right acknowledges that some issues may only surface in a real-world production environment. By observing the system in action, you gain valuable insights into actual attack patterns, system vulnerabilities, and the effectiveness of existing security controls. This creates a continuous learning loop, allowing development teams to proactively strengthen security posture.
How Shift-Right Security Works:
Shift-right involves integrating security tools and practices directly into the production environment. This includes implementing features like:
- Runtime Application Self-Protection (RASP): Provides real-time protection within applications, detecting and blocking attacks as they happen.
- Continuous Security Monitoring: Constantly monitors production environments for suspicious activities, performance anomalies, and known vulnerabilities.
- Automated Security Incident Triage and Response: Automates the initial steps of incident response, speeding up containment and minimizing damage.
- Security Telemetry Collection and Analysis: Gathers detailed security data from various sources and analyzes it to identify trends and patterns.
- Real-time Vulnerability Detection and Exploitation Attempts: Identifies attempts to exploit vulnerabilities in real time.
- Security Observability Dashboards and Alerting: Provides real-time visibility into security posture and alerts relevant teams to critical issues.
Benefits and Drawbacks:
Pros:
- Detects Production-Specific Issues: Unveils vulnerabilities and security flaws that only appear in a live environment.
- Real-World Attack Data: Provides insights into actual attack patterns and techniques used by malicious actors.
- Continuous Improvement Loop: Facilitates continuous learning and improvement of security practices and code security.
- Faster Incident Response: Enables rapid response and containment of security incidents.
- Control Validation: Validates the effectiveness of existing security controls and identifies weaknesses.
Cons:
- Late Detection: May identify vulnerabilities after they’re deployed, potentially after exploitation.
- False Positives: Requires careful management to avoid alert fatigue and wasted resources.
- Performance Overhead: Can impact the performance of production systems if not implemented and managed effectively.
- Integration Challenges: Needs seamless integration with development workflows to maximize effectiveness.
Examples of Successful Shift-Right Implementation:
- Etsy: Their security monitoring directly feeds insights back into the development process, allowing for rapid patching and improvements.
- Netflix: Security telemetry informs future security requirements and helps to anticipate emerging threats.
- Capital One: Implements real-time threat monitoring with direct feedback to development teams for rapid remediation.
- Cloudflare: Employs a continuous security monitoring and improvement cycle, leveraging insights from their vast network.
Actionable Tips for Implementing Shift-Right Security:
- Implement security-focused observability using the RED (Rate, Errors, Duration) method.
- Create automated security playbooks for common findings to streamline incident response.
- Establish clear handoff processes between security operations and development teams.
- Use threat intelligence to tune monitoring for relevant attacks and reduce false positives.
- Implement blameless security postmortems to encourage reporting and foster a culture of learning. Beyond technical security measures, the human element plays a crucial role in your overall security posture. Understanding social engineering tactics and how to respond to them is vital. Resources like this social engineering training can be invaluable for building awareness.
- Learn more about Shift-Right Security Monitoring and Feedback Loops
Why Shift-Right is a DevSecOps Best Practice:
In the fast-paced world of software development, achieving robust security requires a comprehensive approach. Shift-right monitoring and feedback loops are indispensable for organizations striving to incorporate DevSecOps best practices. They bridge the gap between production realities and development processes, ensuring that security is not a one-time event but an ongoing, adaptive process. By embracing shift-right, organizations can build more resilient systems, respond effectively to threats, and foster a culture of continuous security improvement. This approach is particularly beneficial for Scrum Masters, Agile Coaches, software development teams, project managers, and enterprise IT operations departments who need to ensure continuous delivery while maintaining a strong security posture.
This approach was popularized by industry leaders like Dino Dai Zovi, Fastly/Signal Sciences, Google’s SRE practices, and the DORA team. Their work has highlighted the critical role of shift-right in building secure and resilient systems.
Top 8 DevSecOps Best Practices Comparison
| Best Practice | Implementation Complexity 🔄 | Resource Requirements ⚡ | Expected Outcomes ⭐📊 | Ideal Use Cases 💡 | Key Advantages ⭐ |
|---|---|---|---|---|---|
| Implement Automated Security Scanning in CI/CD Pipeline | Medium – initial setup and maintenance needed | Moderate – tools and integration in pipelines | Early vulnerability detection, reduced human error, prevention of vulnerable code | Projects aiming for shift-left security integration in development processes | Early bug discovery, consistent checks, developer security awareness |
| Threat Modeling as Code | Medium to High – requires learning curve and tooling | Moderate – threat modeling tools and integrations | Repeatable, scalable threat models with automated validations | Systems needing ongoing, version-controlled threat modeling across lifecycle | Living documentation, collaboration, automated validation |
| Infrastructure as Code Security | Medium – requires domain expertise and tooling | Moderate – IaC scanners, policy tools | Prevention of insecure infra configs, auditability, compliance enforcement | Environments using declarative infrastructure provisioning | Reduces manual errors, consistent infra security, compliance facilitation |
| Immutable Security with Container Orchestration | High – steep learning curve, robust CI/CD needed | High – container and orchestration resources | Reduced attack surface, consistent secure container environments | Organizations heavily using containers/kubernetes for microservices | Immutable artifacts, automated remediation, zero-trust support |
| Continuous Compliance as Code | Medium to High – translating compliance into code | Moderate to High – compliance tooling and expertise | Continuous compliance verification, audit simplification | Regulated industries requiring continuous adherence to standards | Automated audit evidence, prevention of non-compliance |
| Security Chaos Engineering | High – careful planning and specialized expertise | High – simulation tools and controlled environments | Identification of unknown weaknesses, improved incident response | Teams focused on resilience testing and security readiness | Proactive security validation, resilience building, incident response training |
| Automated Security Guardrails | Medium to High – complex across diverse stacks | Moderate to High – policy frameworks and automation | Automated prevention of security misconfigurations without blocking flow | Organizations balancing security and developer velocity | Friction reduction, scalable security enforcement, faster secure development |
| Shift-Right Security Monitoring and Feedback Loops | Medium – requires integration with production monitoring | Moderate to High – monitoring and analytics tools | Real-time detection of production threats, continuous security improvement | Production environments needing active security observability | Detection of live threats, faster response, security feedback integration |
Elevating Your Security Posture: The Continuous DevSecOps Journey
Implementing DevSecOps best practices is not a destination but a continuous journey of improvement. From integrating automated security scanning in your CI/CD pipeline to leveraging the power of security chaos engineering, the key takeaways from this article highlight the crucial need to weave security into every facet of the software development lifecycle. Mastering these concepts, including threat modeling as code, infrastructure as code security, and immutable security with container orchestration, empowers teams to build more resilient and secure applications from the ground up. Continuous compliance as code and automated security guardrails further solidify this approach, ensuring adherence to security standards and best practices throughout the development process. Shift-right security monitoring and feedback loops provide vital insights, enabling proactive identification and mitigation of vulnerabilities. By adopting these DevSecOps best practices, organizations not only enhance their security posture but also cultivate a culture of security consciousness, which is paramount in today’s increasingly complex threat landscape.
The benefits of incorporating these practices extend far beyond just checking compliance boxes. They translate to tangible outcomes: reduced risk, faster incident response, enhanced customer trust, and ultimately, a more robust and reliable software product. As the sophistication of cyber threats continues to evolve, a well-defined and implemented DevSecOps strategy becomes not just a best practice, but a business imperative.
Start small, focus on iterative improvements, and embrace the ongoing learning process that defines the DevSecOps journey. For streamlined communication and efficient collaboration within your DevSecOps workflows, particularly during incident response, explore tools like resolution’s NASA, integrated within Jira. Streamline your security efforts and foster team collaboration with resolution’s NASA, a powerful tool integrated with Jira, designed to enhance communication and workflow efficiency within your DevSecOps practice. Visit NASA – Not Another Standup App to learn more and empower your team to build secure software efficiently.
