- Apps
- User Management
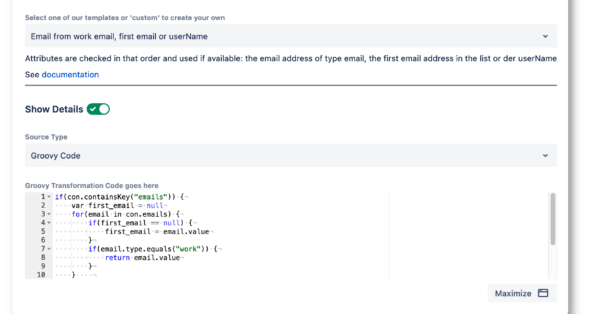
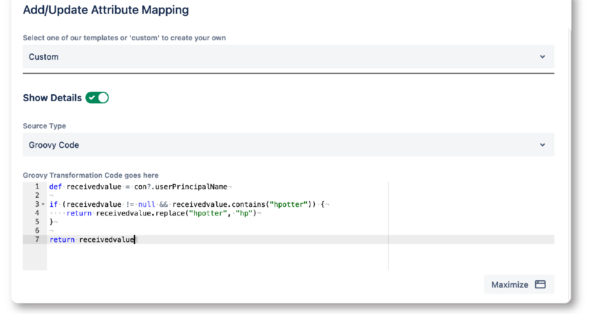
- SAML Single Sign-OnAuthenticate and provision users
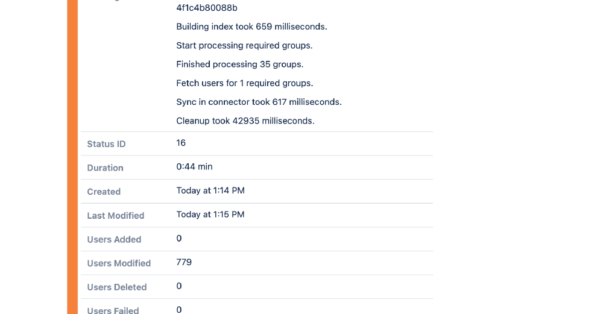
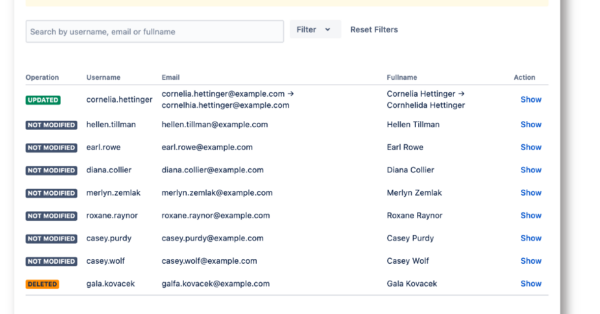
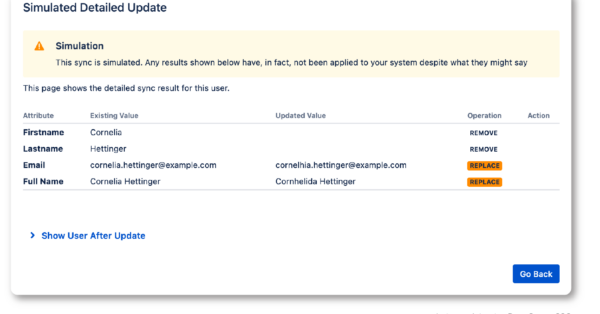
- User & Groups SyncSynchronize users and groups
- User DeactivatorIdentify and disable inactive users
- API Token AuthenticationReplace passwords with tokens
- AWS ALB AuthenticationAuthenticate with AWS
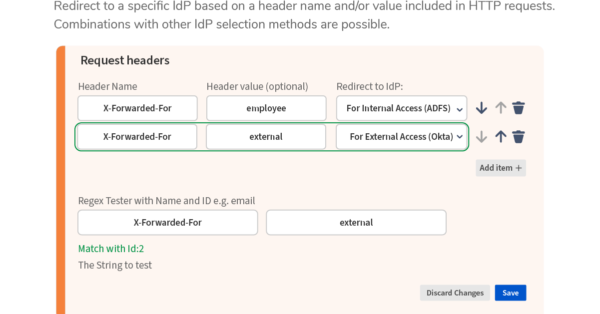
- HTTP Header AuthenticationAuthenticate with request headers
- Productivity
- NASA - Agile Meetings for TeamsNASA – Not Another Standup App
- Out of Office Assistant for Jira CloudWork delegation and vacation responders
- Required Fields for monday.com AppAutomations that will ensure you never miss vital data again!
- Task Egg TimerTime Tasks, count down deadlines
- Issue Translation for JSMMake Jira Service Management multilingual
- Issue Translation for JiraIssue translations: subject, description & comments
- Reporting for Confluence with Google AnalyticsUser insights for Confluence Cloud
- Link Shortener & URL RedirectsUser-friendly branded links for Confluence
- Integration Apps
- monday.com for ConfluenceVisualize and share your boards
- Confluence Plugin for Zoom RecordingsEasily access recorded meetings
- HubSpot for ConfluenceIntegrate & Link HubSpot boards into Confluence
- Smartsheet for ConfluenceEmbed gantt, calendars and more
- Miro Embed for ConfluenceFreely navigate whiteboards together
- PDF Embed for ConfluenceEmbed your PDF documents in Confluence
- Space Holder Link
- monday.com for JiraVisualize and share your boards
- Jira Plugin for Zoom RecordingsAmplify your Zoom recordings in Jira
- HubSpot for JiraConnect Jira issues in HubSpot
- Embed Airtable for ConfluenceDynamic datasets and forms
- PowerBI Embed for ConfluenceBridge the gap between data and decision making
- More Embed Apps
- User Management
- Support
- Documentation
- Partners
- Whitepapers
- Transforming StandupsSay no to bad agile comms and pave the way for change
- re:solution v.s. Atlassian API-TokenSome apps are built differently
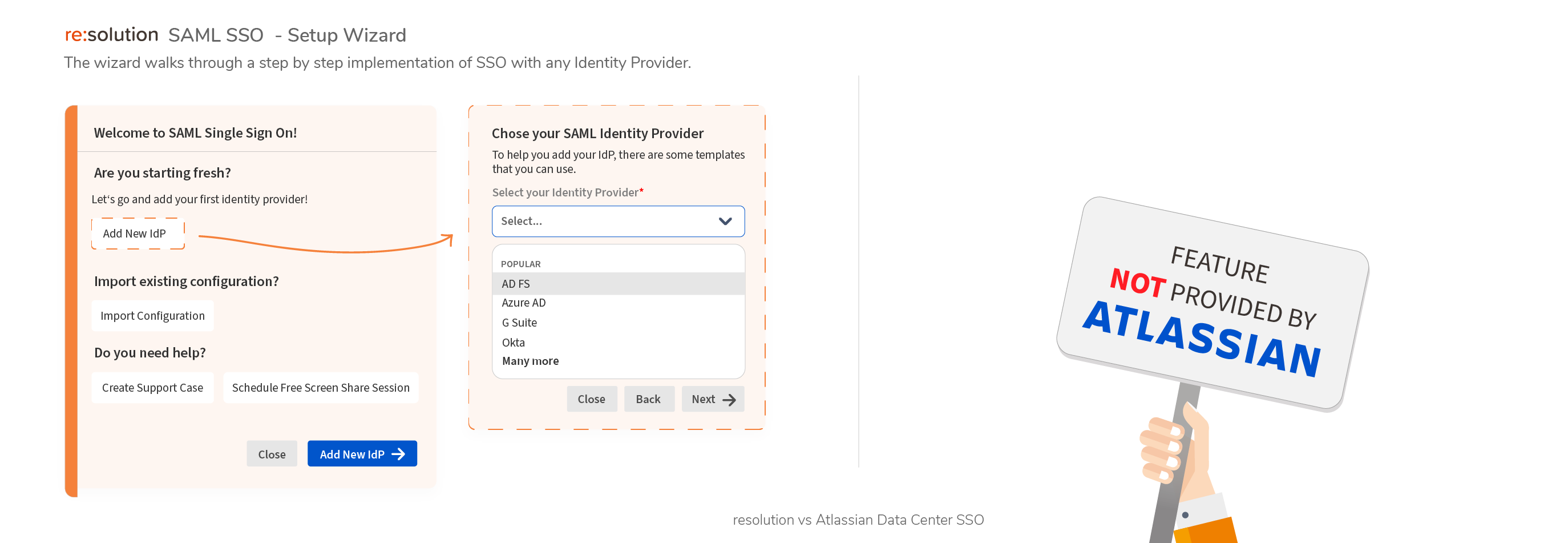
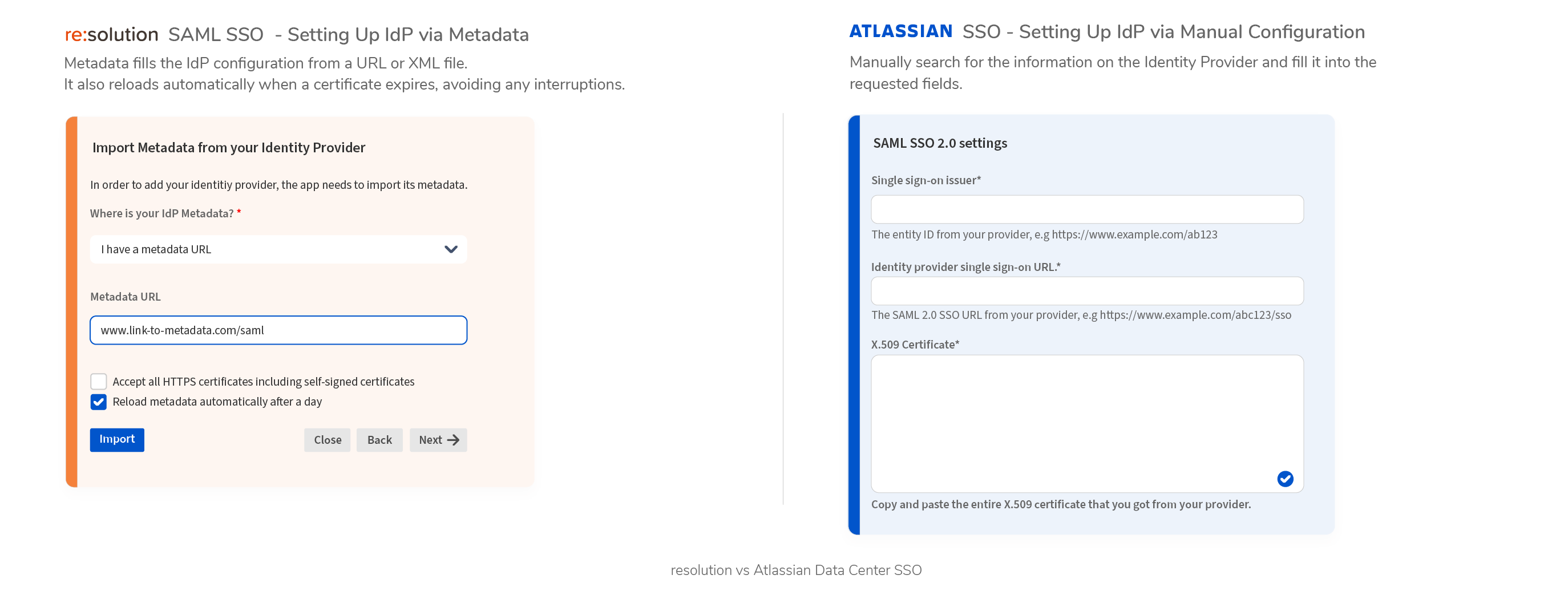
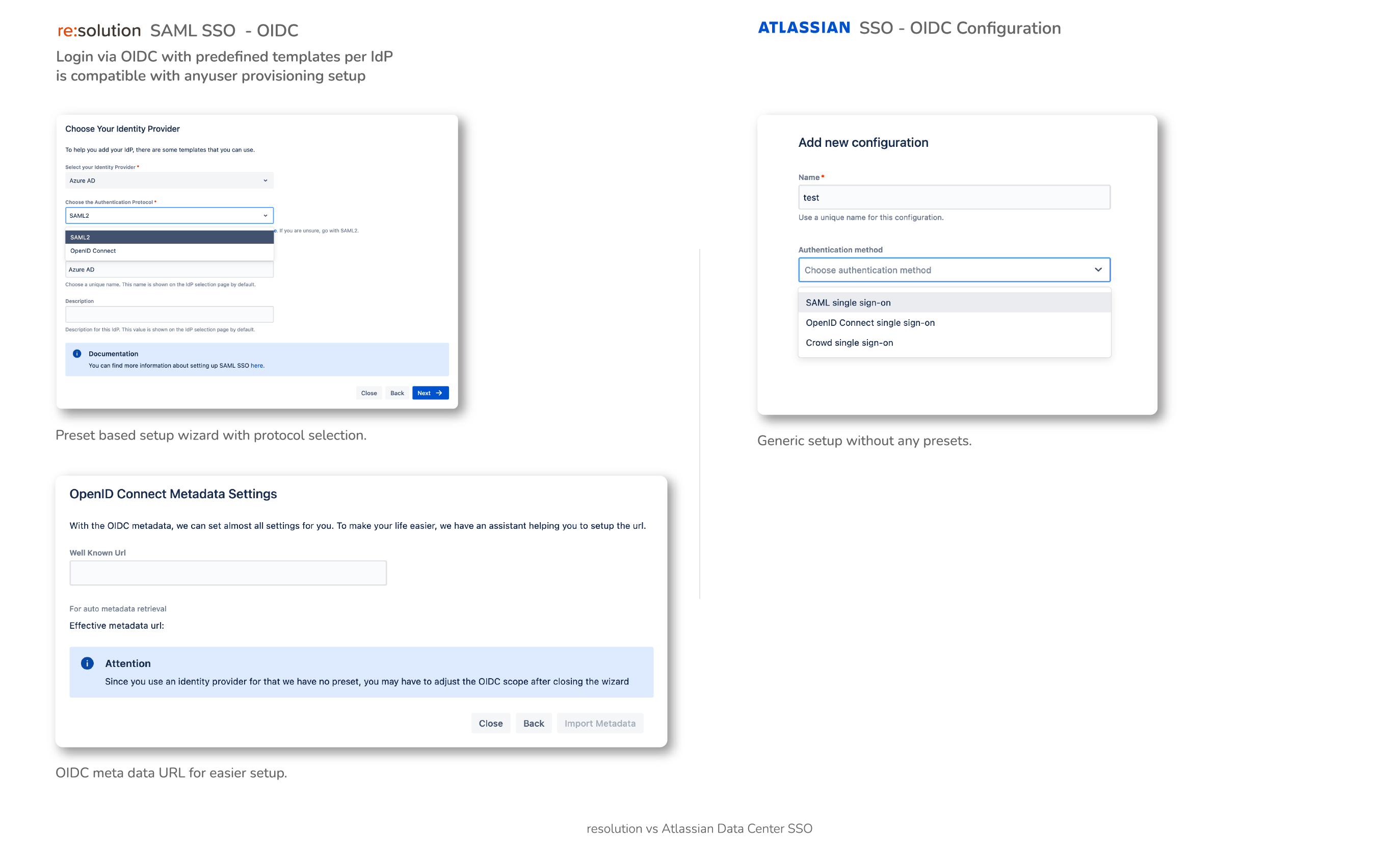
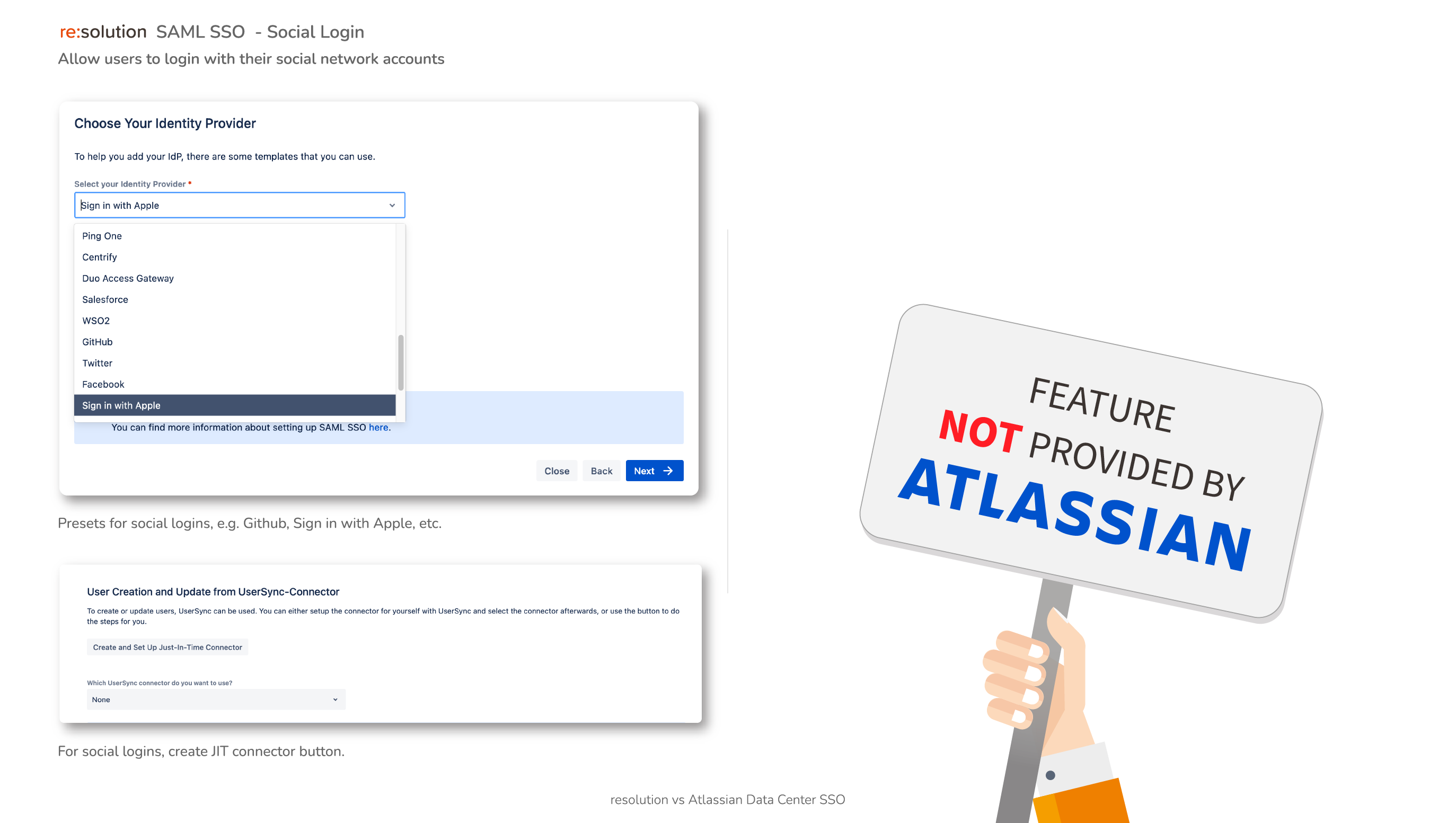
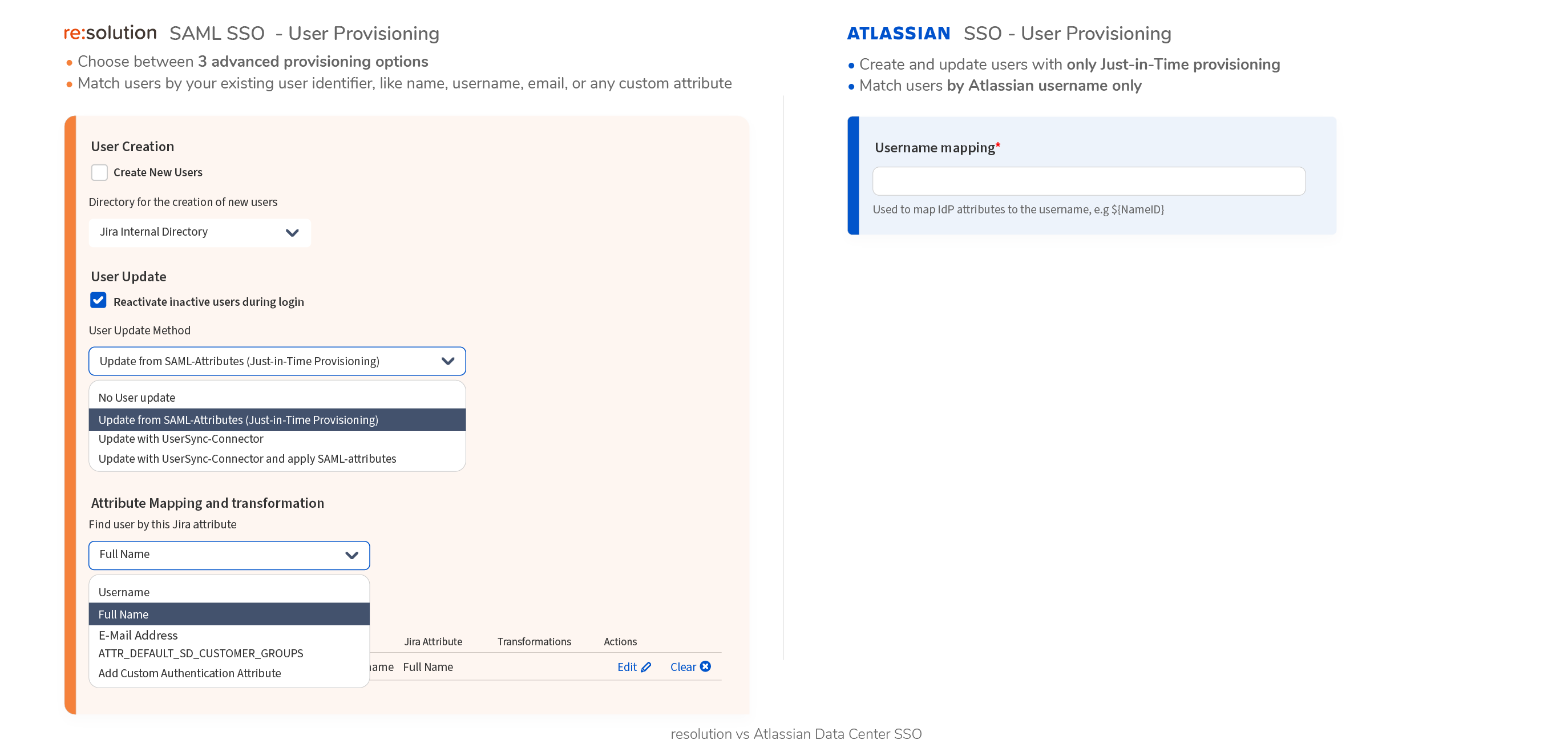
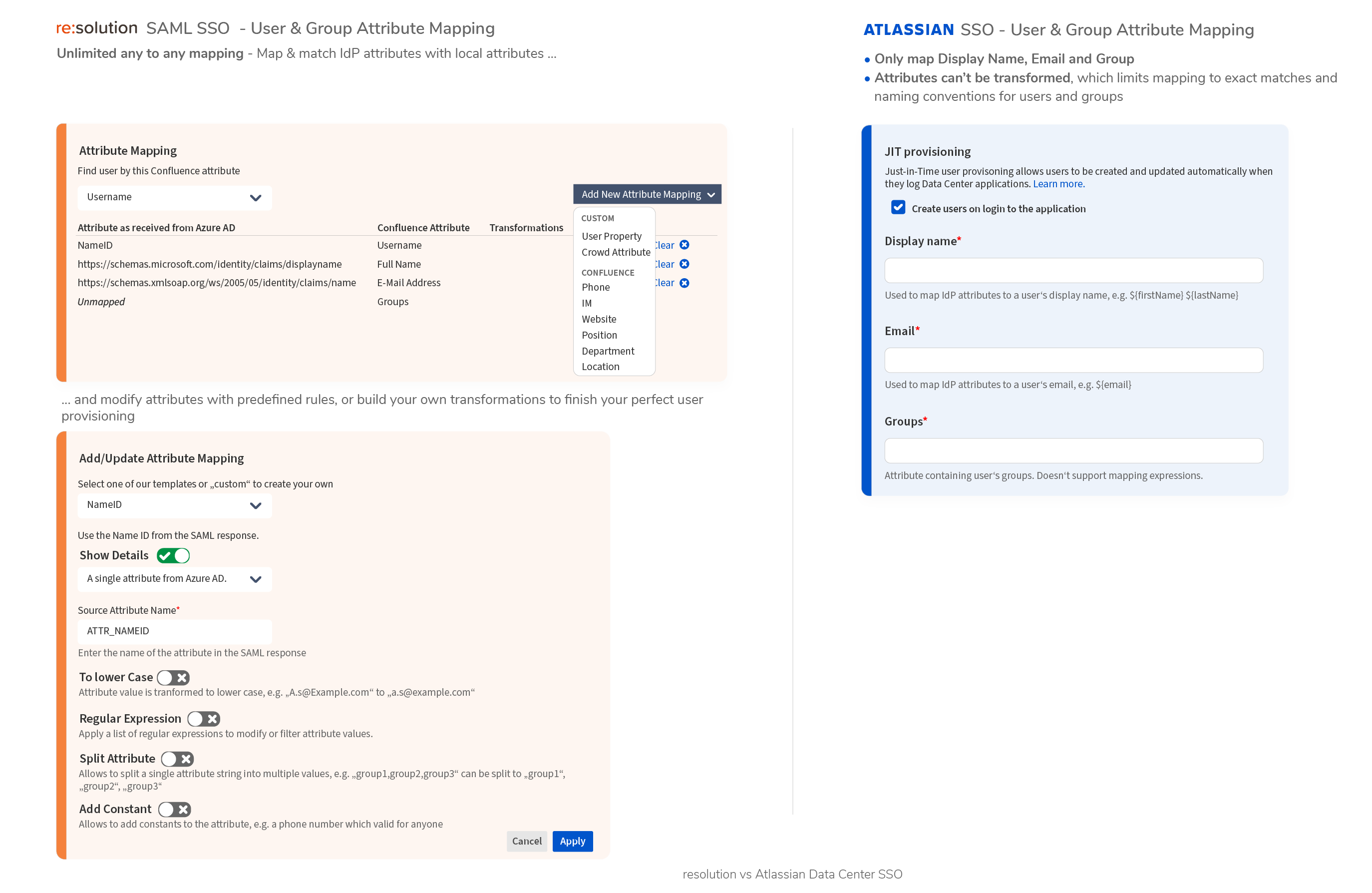
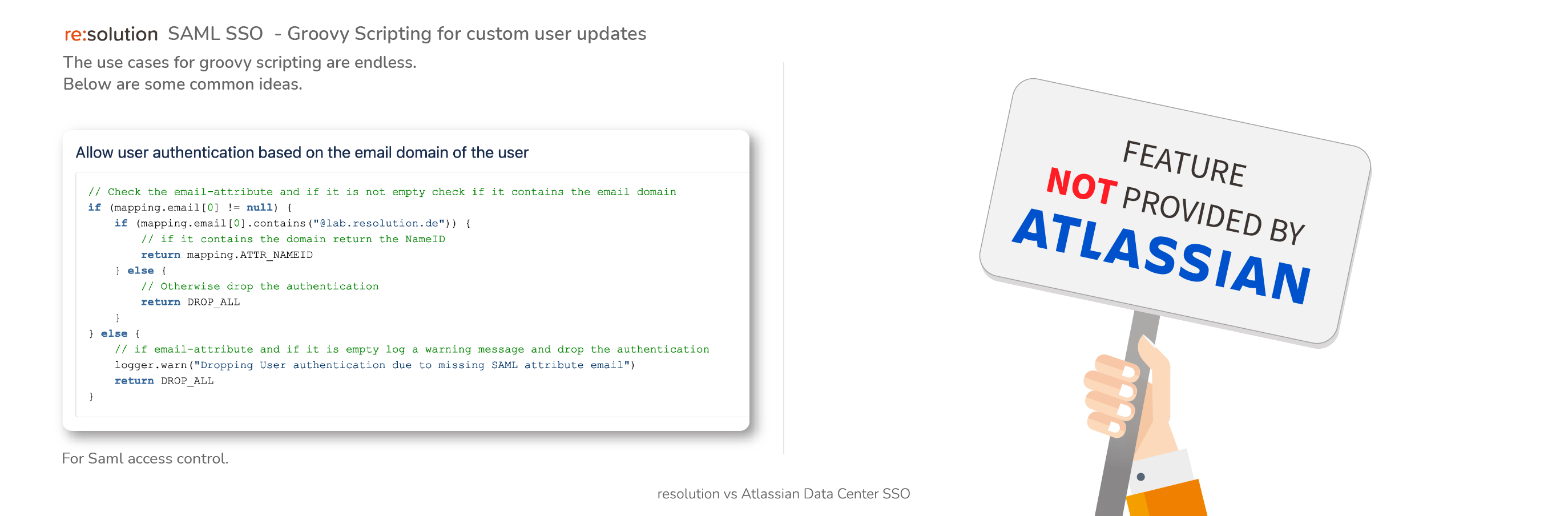
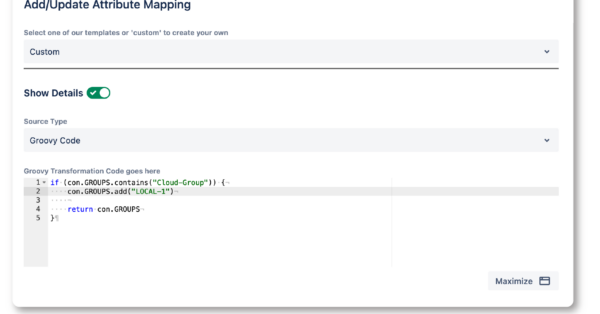
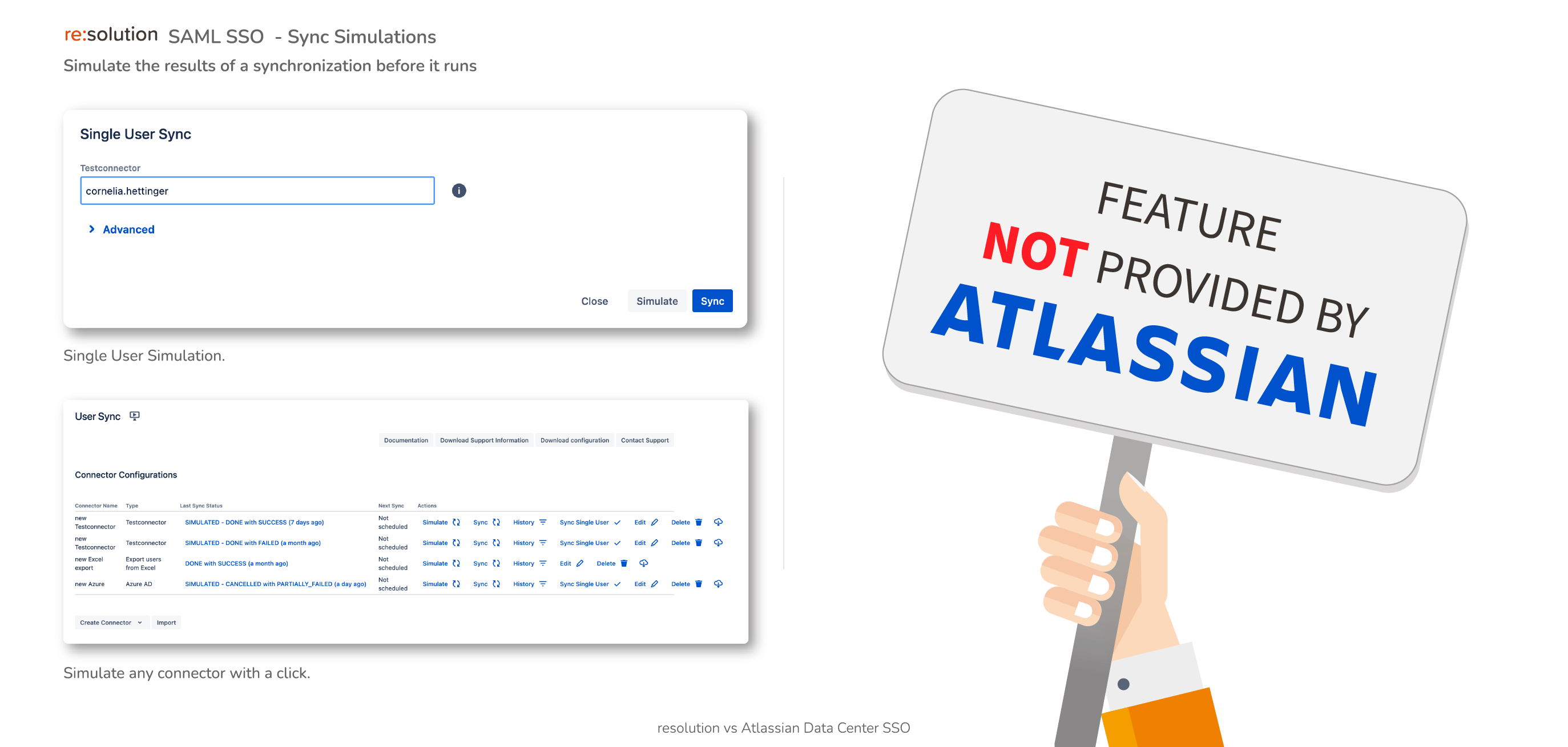
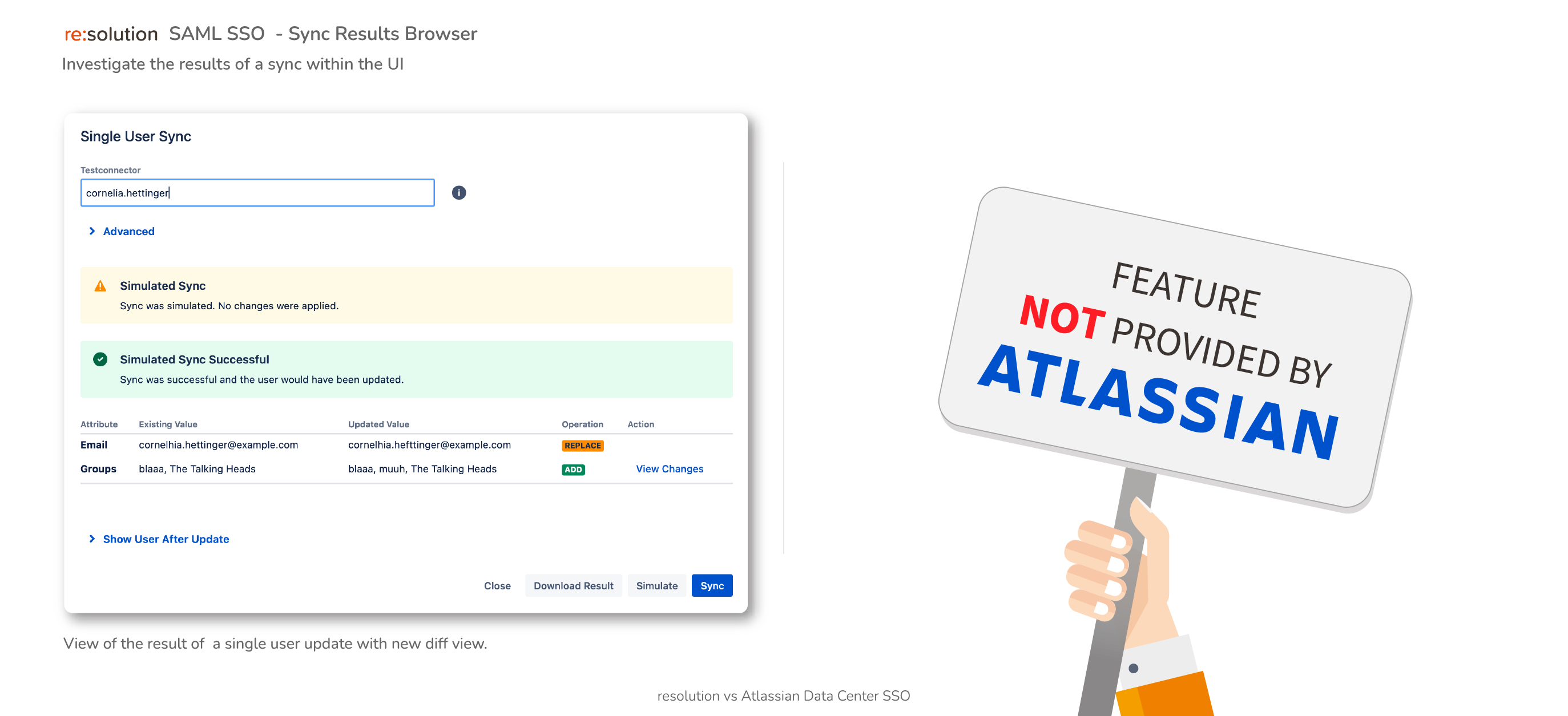
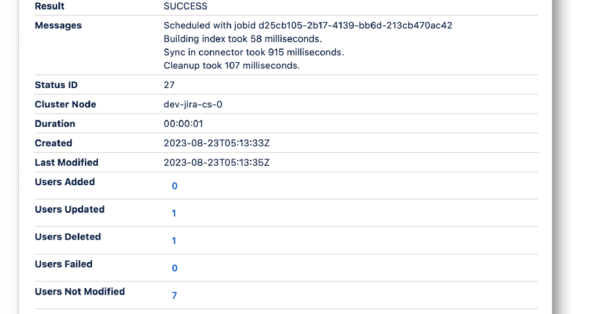
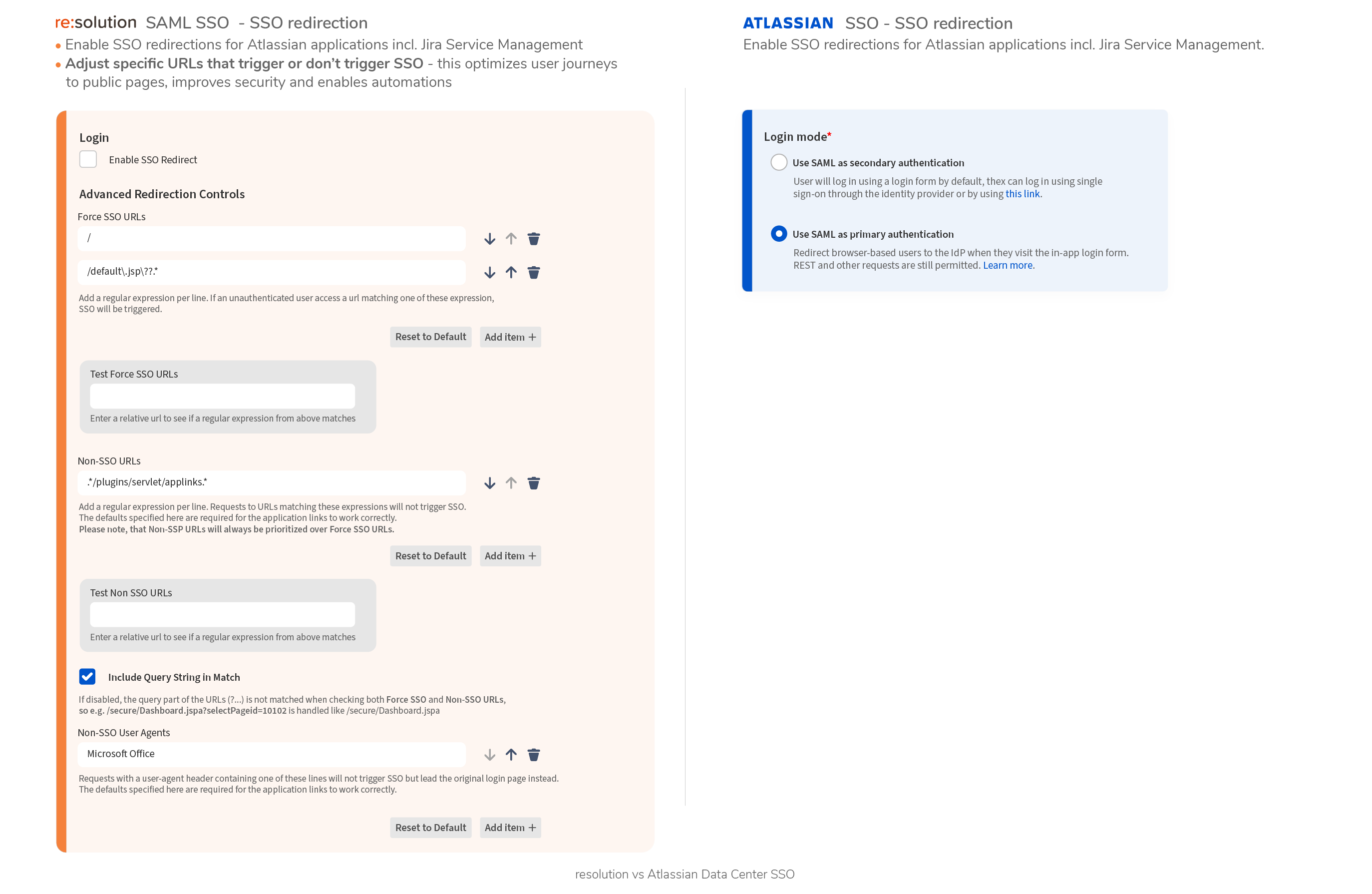
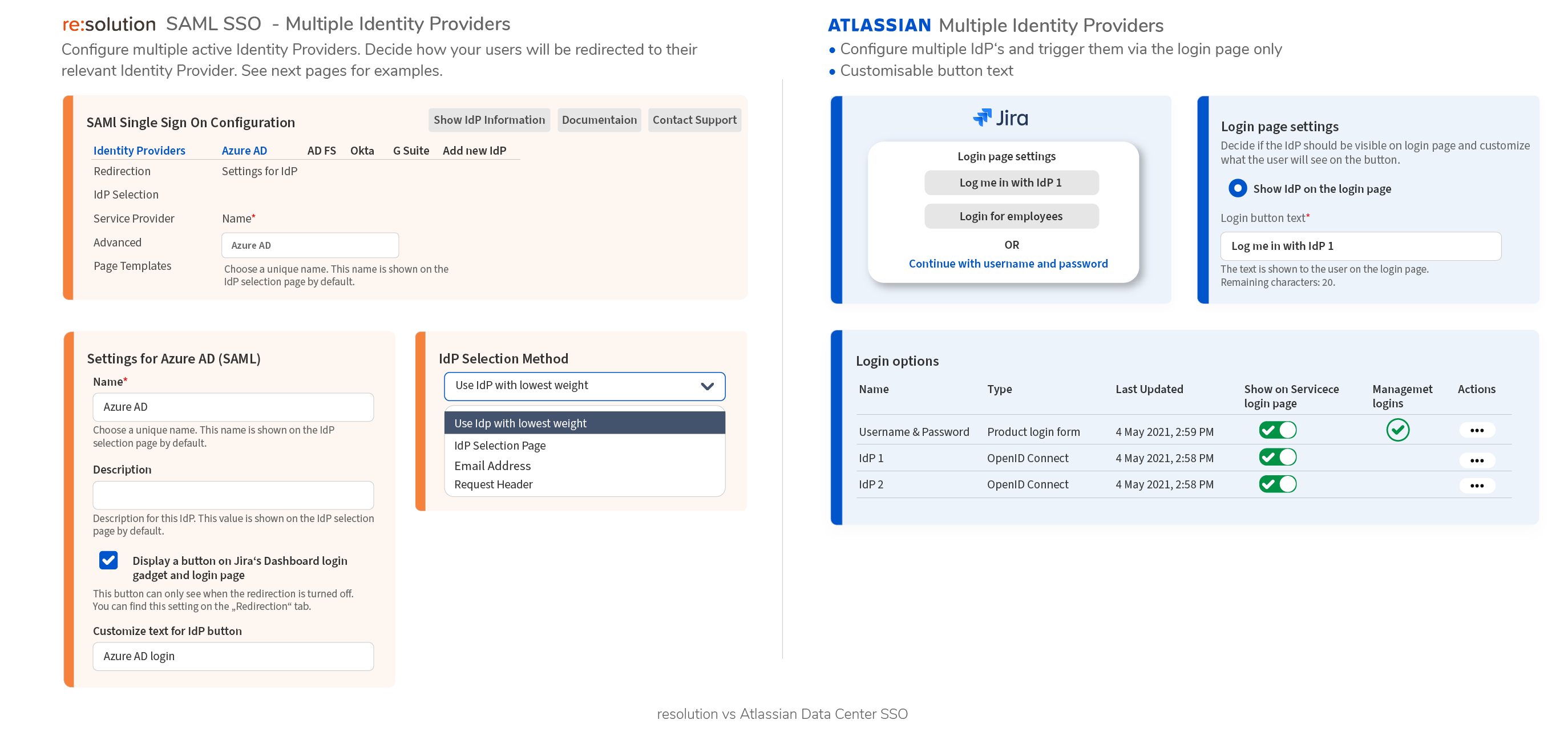
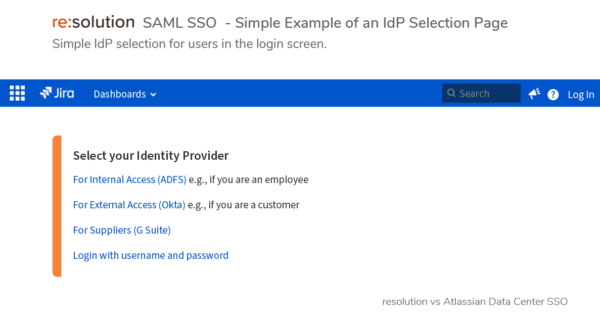
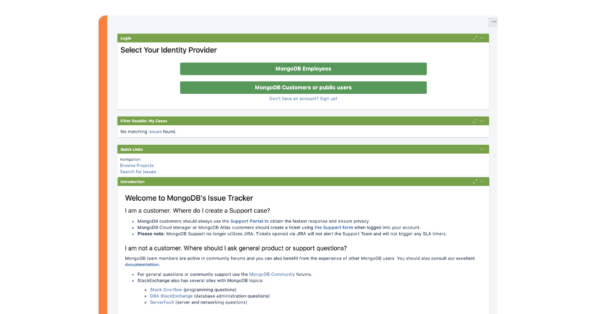
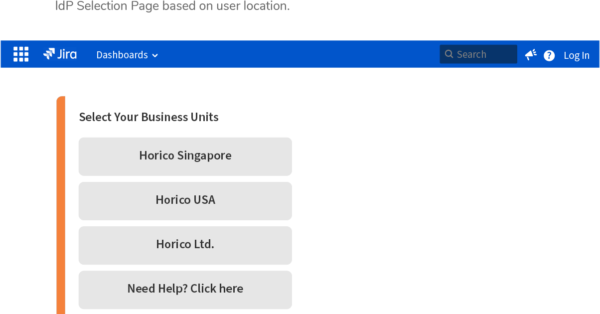
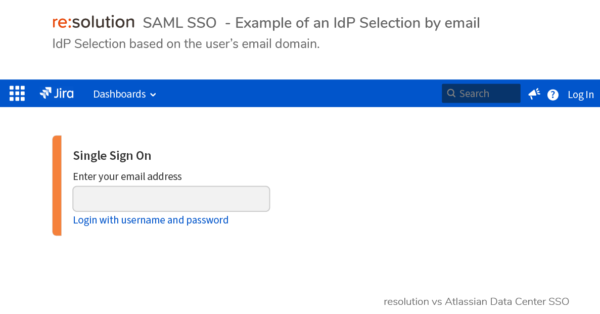
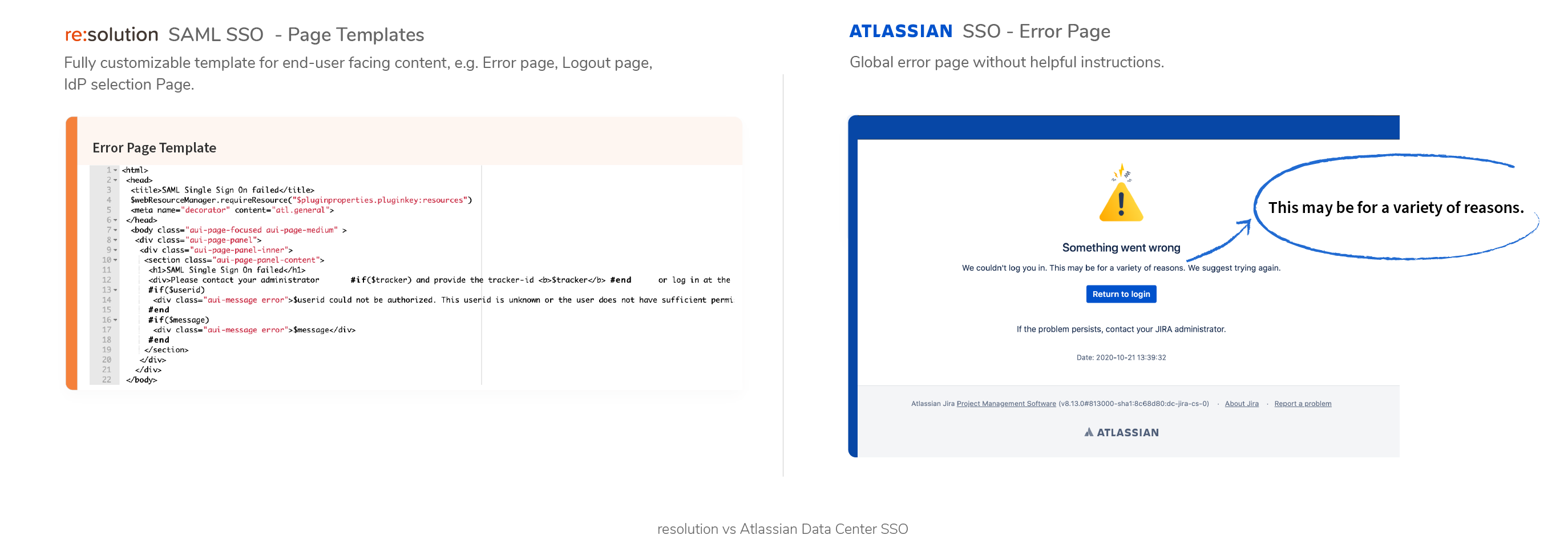
- Data Center SAML SSO resolution vs AtlassianFull feature comparison with the native Single Sign On functionality
- Out of Office – For Jira PMsKeep Teams Aligned, Even When Members Are Away
- Out of Office – ITSM & ESMSmart Delegations. Confident Automation.
- Blog
- About Us