An access control policy template isn’t just a document; it’s a ready-made framework that helps you quickly decide who gets access to what data and systems. Using a template saves a ton of time and, more importantly, slashes security risks right from the get-go. Think of it as the essential blueprint for building a secure and compliant operation.
Why An Access Control Policy Is Your First Line Of Defense
Let’s be honest—drafting security policies can feel like a tedious chore, just another box to check for compliance. But a well-defined access control policy is so much more than paperwork. It’s the active, living blueprint that governs access across your entire organization. Without one, you’re basically leaving your most critical doors unlocked and unwatched.

Imagine a former employee’s credentials are still active. It’s a shockingly common oversight, but it’s a risk that’s easily neutralized with a clear policy that requires immediate de-provisioning upon termination. This is where a policy shines: it turns abstract security goals into concrete, enforceable actions.
From Jargon To Practical Risk Reduction
Security terms like “least privilege” can sound like empty jargon, but they represent powerful, practical strategies for shrinking your attack surface. The principle is simple: users should only have the bare-minimum access needed to do their jobs. It’s common sense, really. A marketing intern, for example, has absolutely no business poking around in financial databases or sensitive HR records.
A solid access control policy template bakes these principles right into its structure. It guides you toward making security-conscious decisions from the start, removing the guesswork and paving a clear path to protecting your business from both internal mishaps and external threats.
Before you build anything, you need a strong foundation. Here’s a quick look at the essential elements every access control policy needs, connecting each part to its real-world security goal.
Core Components Of A Robust Access Control Policy
| Policy Component | Primary Goal | Example Application |
|---|---|---|
| Policy Scope | Clearly define what systems, data, and users the policy covers. | “This policy applies to all employees, contractors, and third-party vendors accessing corporate network resources.” |
| Roles & Responsibilities | Assign ownership for policy enforcement and management. | “The IT Department is responsible for implementation; department heads are responsible for approving access requests.” |
| Access Control Principles | Establish guiding rules like Least Privilege and Separation of Duties. | “Users will be granted the minimum permissions required for their job functions.” |
| Access Request & Approval | Formalize the process for granting, modifying, or revoking access. | “All access requests must be submitted via the IT service portal and approved by the user’s direct manager.” |
| User Access Reviews | Mandate periodic checks to ensure access levels remain appropriate. | “HR and IT will conduct quarterly reviews of all user access rights to sensitive financial systems.” |
| Policy Enforcement | Detail the consequences of non-compliance. | “Violations of this policy may result in disciplinary action, up to and including termination of employment.” |
These components work together to create a comprehensive framework that not only secures your assets but also stands up to audits and regulatory scrutiny.
Establishing An Enforceable Foundation
An access control policy is the bedrock upon which all your technical security controls are built. It’s the “why” behind your technical “how.” For instance, without a policy guiding your decisions, managing user permissions in complex systems can quickly spiral into chaos. Our guide on Jira access management shows just how vital a clear strategy is for keeping sophisticated tools under control.
An effective policy isn’t just about locking things down; it’s about enabling the right access. The goal is to ensure productivity isn’t choked by overly strict measures while still maintaining a rock-solid security posture.
For any organization, putting a robust access control policy in place is a critical step in developing effective commercial access control strategies. It sets the definitive standard for how both physical and digital assets are protected, helping you prevent operational mayhem and the nightmare of a costly data breach. Starting with a proven template is simply the smartest, most efficient way to build a framework that actually works.
The Anatomy of an Effective Policy Document
So, what actually goes into a policy that works in the real world? A truly effective access control policy isn’t just a generic outline; it’s a living document built from several interconnected parts. Each piece has a specific job, and they all work together to create something clear, enforceable, and genuinely protective of your organization’s most important assets.

The goal here isn’t to get bogged down in dense legal or overly technical jargon. It’s about building a practical guide that turns a blank page into your company’s first line of defense. Let’s break down the core elements you absolutely need to include.
Core Policy Statement and Scope
Every solid policy kicks off with a clear policy statement. Think of this as the “why” behind the document. It’s a concise declaration of the policy’s purpose. For instance, it might state that the goal is to protect company information from unauthorized access and to ensure the confidentiality, integrity, and availability of data. Simple.
Next, you define the scope. This section is absolutely critical for stamping out ambiguity. It clearly states who and what the policy covers, leaving no room for guesswork.
- Who it applies to: Does it cover all full-time employees, part-time staff, contractors, third-party vendors, or temporary interns? Spell it out.
- What it applies to: List the systems, networks, applications (both on-premise and in the cloud), and data classifications governed by the policy. For example: “This policy applies to all corporate-owned devices, network infrastructure, SaaS applications, and databases containing customer or financial data.”
To really understand the scope of what you’re protecting, it helps to know the systems inside and out. This fantastic guide to wireless access control systems provides a great foundation for understanding the very technologies your new policy will govern.
Defining Roles and Responsibilities
A policy without clear ownership is just a piece of paper that will collect dust. This section is where you assign accountability, making sure specific people or teams are on the hook for implementing, managing, and enforcing the rules. This eliminates confusion and creates a clear chain of command for anything access-related.
Here are some of the common roles you’ll need to define:
- Data/System Owner: This is typically a department head or manager. They are ultimately responsible for the data and get the final say on who should have access.
- System Administrator: The hands-on technical team responsible for the day-to-day work of granting or revoking access based on approved requests.
- User: The individual employee or contractor who is granted access. Their responsibility is to use that access appropriately and guard their credentials.
- Security Officer/Team: This team is in charge of auditing the policy’s effectiveness, running periodic reviews, and investigating any security incidents.
A common mistake I see is making the IT department solely responsible for everything. True security is a shared responsibility, and your policy must reflect that. Business leaders own the data; IT executes the controls.
Access Management and Review Procedures
This is the operational heart of your access control policy. It details the “how-to” for the entire user access lifecycle, from the day someone starts to the day they leave. Vague procedures are unenforceable, so this section needs to be incredibly precise.
You should outline the exact process for these key actions:
- Requesting Access: How does someone ask for new or different access? This should point to a standard form or ticketing system that captures the user’s name, their role, the specific resource they need, and—most importantly—a business justification from their manager.
- Approving Access: Who has the final say? Your policy should state that approval must come from the data or system owner, not just the user’s direct manager. This is especially true for highly sensitive systems.
- Periodic Access Reviews: A staggering 63% of businesses have former employees who can still access company data. To fight this, your policy must mandate regular access reviews, usually quarterly or semi-annually. This process involves system owners reviewing a list of everyone with access to their systems to confirm it’s all still necessary and appropriate.
- Revoking Access: Detail the process for immediate access termination when an employee leaves or changes roles. This procedure has to be automatically triggered by HR processes to close this all-too-common and dangerous security gap.
By clearly documenting these procedures, you create a repeatable and auditable trail for every single access decision. This not only tightens your security but also becomes invaluable when the compliance auditors come knocking.
Making Role-Based Access Control (RBAC) Work for You
Role-Based Access Control, or RBAC, sounds technical, but it’s really just a smart way to boost security and make life easier. Instead of giving people permissions one by one—a nightmare to manage—RBAC groups permissions by job function. Think of it as creating a “keychain” for each type of job.
The idea is simple: you create a role, give that role the right set of “keys” (permissions), and then you just hand out the appropriate keychain to anyone doing that job. It’s a clean, straightforward way to bring order to the chaos of access management.
Identifying Business Functions and Defining Roles
First things first, you need to look at your organization in terms of what people do, not who they are. What are the core jobs happening every day? Start with broad categories and then drill down.
For a typical software company, you might have functions like:
- Marketing: They handle campaigns, social media, and create content.
- Sales: They’re in the CRM, managing leads and customer relationships.
- Engineering: They build, test, and deploy the product.
- Customer Support: They field user questions and troubleshoot problems.
- Finance: They manage billing, payroll, and all things money.
From these functions, roles start to emerge. The ‘Marketing’ function probably has a ‘Marketing Manager’ and a ‘Content Creator.’ They don’t need the same access. The manager needs to see budget reports, while the creator just needs access to the blog. This is the heart of building a solid access control policy template.
The whole process really boils down to three key stages.
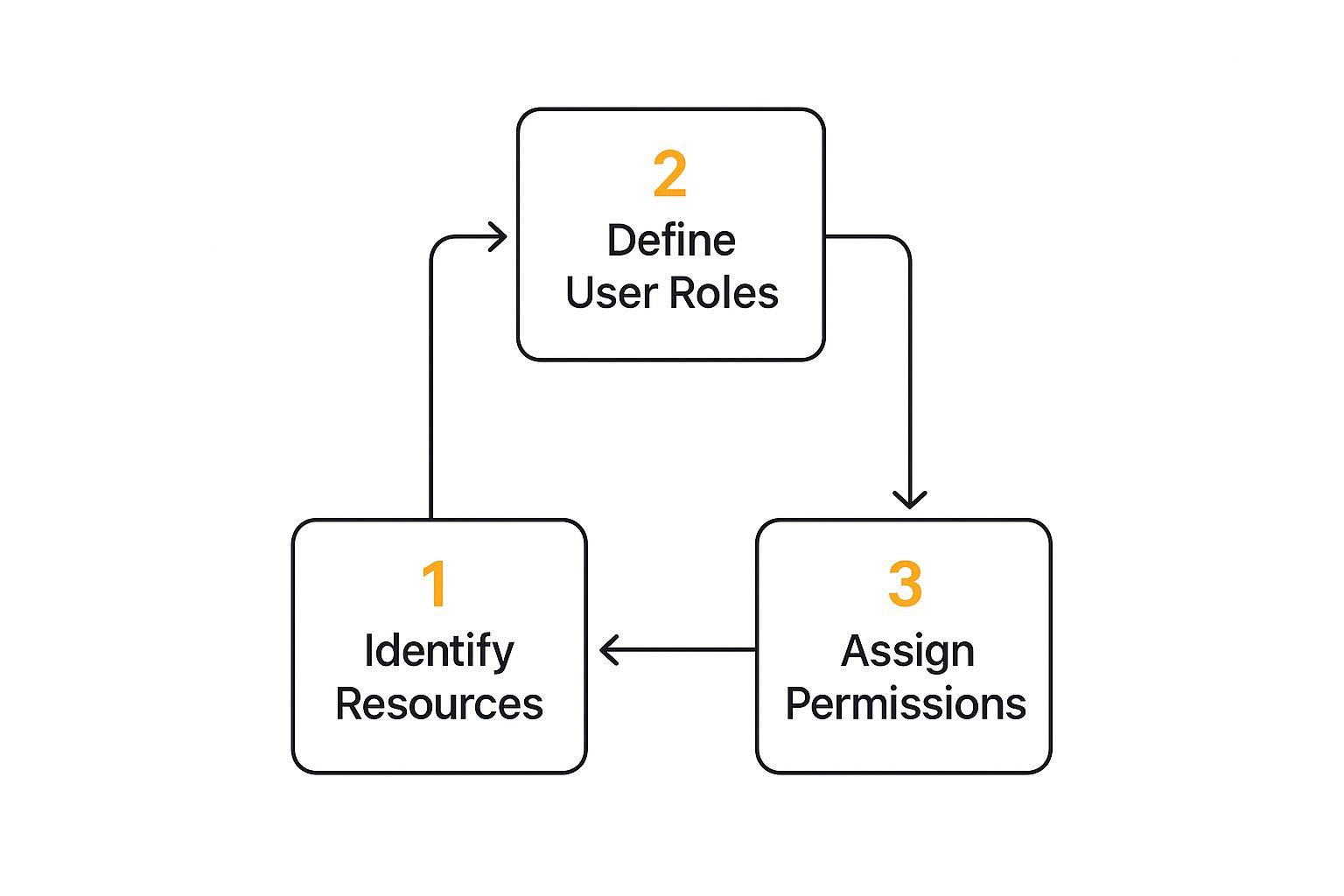
As you can see, you can’t decide who gets access until you know what you’re protecting in the first place.
Mapping Permissions and Handling Exceptions
With your roles defined, the next step is to map permissions. This is where you get granular and apply the principle of least privilege. Give people only the access they absolutely need to do their job, and nothing more.
A ‘Support Agent’ role, for instance, should have read-only access to a customer’s subscription details, but they definitely shouldn’t be able to see or change payment information. The ‘Finance’ role gets full access to the billing system but has no reason to be in the software development repositories.
This strict separation is a huge security win. It minimizes accidental data exposure and contains the damage if an account is ever compromised. If a support agent’s account gets hacked, the attacker is walled off from your financial data.
But we all know the real world is messy. What about one-off projects? Easy. You can create temporary, project-specific roles. A ‘Project Phoenix Team Member’ role might grant short-term access to a specific set of tools and documents. When the project wraps up, you just revoke that role, and all associated permissions vanish instantly. No lingering security holes.
The real beauty of RBAC is how it scales. When you hire a new support agent, you just assign them the ‘Support Agent’ role. Boom. They have everything they need to get started—and not a single permission more. You’re not manually cloning access from another user and crossing your fingers you did it right.
Getting this right is becoming more critical every day. The access control market is projected to grow from around USD 9.55 billion in 2025 to an estimated USD 13.54 billion by 2030, largely because of tightening regulations in fields like banking and healthcare.
Automating User Provisioning and Deprovisioning
The final, crucial piece is connecting RBAC to your HR system. When someone joins the company, gets promoted, or leaves, their access needs to change automatically and immediately. This is where user provisioning and deprovisioning become your best friends.
When HR marks an employee as terminated, an automated workflow should kick in and instantly disable all of their accounts. No delays, no human error.
This automation transforms your policy from a document sitting in a folder to a living, breathing security system that actually works. For a closer look at this essential process, check out our guide on user provisioning and deprovisioning. Integrating these systems closes one of the most common—and most dangerous—security gaps an organization can have.
Your Customizable Access Control Policy Template
You came here for a tool, and here it is: a comprehensive, ready-to-use access control policy template. We’ve built this from the ground up to be a practical starting point, not some rigid document you have to fight with. It’s all laid out in a clean, copy-and-paste-friendly format with all the essential components we’ve covered.

Inside, you’ll find everything you need—sections for policy scope, detailed roles, access management procedures, and core principles like least privilege. More importantly, it’s packed with clear [placeholders] and direct instructions to help you tailor it to your organization’s unique setup. This isn’t just a download; it’s a functional resource designed to save you hours of guesswork and help you build a professional security policy that actually works.
How To Use This Template
We built this document for flexibility. The best way to get started is to simply copy the text below and paste it into your favorite document editor. From there, a good first step is to find and replace the [Company Name] placeholder throughout.
Next, you’ll want to walk through each section. Pay close attention to anything marked with [Instruction:]. These are your cues to plug in company-specific details, like the names of your systems, department titles, or the specific security tools you have in place. The goal is to swap every placeholder with information that reflects your real-world operational environment.
Remember, this template gives you the structure and professional language. The specific details you add are what will make it truly yours—and most importantly, enforceable.
Pro Tip: Don’t get bogged down trying to perfect every single detail on the first pass. A much better approach is to work through the template with your team, pulling in department heads and your IT staff. Their input is gold for making sure the policy is both practical and comprehensive.
The Access Control Policy Template
1.0 Policy Statement and Purpose
This Access Control Policy outlines the requirements for managing access to [Company Name]‘s information systems, data, and physical facilities. The purpose of this policy is to establish a framework of controls to protect the confidentiality, integrity, and availability of our assets from unauthorized access, modification, or destruction.
2.0 Scope
This policy applies to all [Company Name] employees, contractors, temporary staff, and third-party vendors (collectively, “Users”) who require access to any of [Company Name]‘s information systems, including but not limited to:
- Corporate network infrastructure
- Cloud-based applications and platforms (e.g., AWS, Microsoft 365, Salesforce)
- Internal servers and databases
- Proprietary software applications
- Physical office locations and data centers
3.0 Roles and Responsibilities
- System/Data Owner: Usually a department head who is responsible for classifying their data and approving access requests for systems under their control.
- System Administrator: The IT team member in charge of implementing, managing, and revoking user access based on approved requests.
- Users: Every individual granted access is responsible for protecting their credentials and following this policy to the letter.
- Security Officer: Responsible for auditing policy compliance, running periodic access reviews, and managing security incident response.
4.0 Core Access Control Principles
[Company Name] is built on the following core security principles for managing access:
- Principle of Least Privilege (PoLP): Users are only granted the absolute minimum level of access required to do their jobs. Nothing more.
- Separation of Duties: We divide critical tasks among multiple users to prevent any single person from having too much control.
- Need-to-Know Basis: Access to sensitive information is strictly limited to individuals who have a legitimate business need to see it.
5.0 User Access Management Lifecycle
This section breaks down the procedures for the entire user access journey, from start to finish.
Access Provisioning
All requests for new user accounts or changes to existing access levels must be submitted through [Specify Ticketing System, e.g., Jira Service Desk]. Any request has to be approved by the user’s direct manager and the relevant System/Data Owner before the IT Department will act on it.
User Access Reviews
On a quarterly basis, System/Data Owners will work with the Security Officer to review all user access rights for systems they manage. The whole point of these reviews is to double-check that existing access is still necessary and appropriate.
Access Deprovisioning
When an employment or contract ends, all access to [Company Name] systems will be revoked within 24 hours. This process is kicked off automatically by Human Resources. It’s also vital to keep a clean user directory over time. For more on this, our guide on deactivating inactive users gives you practical steps for optimizing license usage and security.
6.0 Authentication Requirements
All users must follow these authentication standards:
| System Sensitivity | Authentication Requirement |
|---|---|
| High (e.g., Financial Systems, HR Portals) | Multi-Factor Authentication (MFA) is mandatory. |
| Medium (e.g., CRM, Project Management Tools) | Strong password (as defined in the Password Policy). |
| Low (e.g., Intranet, General File Shares) | Standard password. |
7.0 Policy Enforcement
Failure to comply with this Access Control Policy may result in disciplinary action, up to and including termination of employment or contract, as well as potential legal action in accordance with local laws and regulations.
An access control policy isn’t a “set it and forget it” document. Let’s be honest, a static policy is a dangerous one. Technology just moves too fast for that. The moment your team spins up a new cloud server, adopts another SaaS tool, or connects an IoT device, your policy is already on its way to becoming obsolete.
Just think about your team’s daily workflow. They’re jumping between a whole cocktail of third-party tools for everything from project management to customer comms. Each one of those is a new entry point to your data that needs to be governed by your policy. A proactive approach is really the only way to keep your policy a relevant, powerful tool for securing your assets.
This isn’t just a hunch; it’s backed by major market trends. The global access control market is projected to more than double, jumping from about USD 12.01 billion in 2025 to USD 25.15 billion by 2034. This explosive growth is largely fueled by the very things we’re talking about—IoT and cloud tech, which demand much smarter security. You can dig into more insights on this access control market expansion and the role AI is playing over on Precedence Research.
Adapting Your Policy for Cloud Platforms
Cloud platforms like Amazon Web Services (AWS) or Google Cloud throw a real wrench in traditional access management. Unlike on-premise servers, cloud resources can be spun up and torn down in minutes. Trying to manage that manually is a recipe for disaster.
Your policy has to evolve to handle this dynamic environment. For instance, a crucial update is to mandate the use of the cloud platform’s own native access control tools. A fantastic example is AWS’s Resource Control Policies (RCPs), which let you set a data perimeter at the organizational level. This is a huge win. It means that even if a developer misconfigures a single resource, your overarching rules can still block unauthorized external access.
You could add a clause to your policy that looks something like this:
All cloud resources provisioned under
[Company Name]‘s accounts must adhere to centrally managed access policies. For AWS environments, this includes the application of Resource Control Policies (RCPs) to restrict data access to principals within the organization’s defined perimeter, unless an explicit exception is granted by the Security Officer.
This simple addition fundamentally shifts your security posture from chasing individual settings to enforcing a broad, centralized strategy. It’s a non-negotiable update for any business operating in the cloud.
Securing SaaS Applications and Third-Party Tools
SaaS tools are everywhere, and for good reason. Your team relies on everything from Slack to Salesforce. The problem? Each one brings its own user management system, creating a messy, fragmented, and often insecure web of access points. Your policy needs to bring some order to this chaos.
A key strategy here is to mandate Single Sign-On (SSO) wherever you possibly can. SSO centralizes authentication through your main identity provider, giving you one control panel to manage user access across dozens of different applications.
Here are a couple of specific clauses you should consider adding:
- SSO Mandate: “All SaaS applications handling sensitive company or customer data must be integrated with the corporate Single Sign-On (SSO) solution. Applications that do not support SSO require a documented risk assessment and approval from the Security Officer.”
- Automated Provisioning: “User access to integrated SaaS applications shall be managed via automated provisioning and de-provisioning, triggered by changes in the user’s role or employment status within the central identity provider.”
That second point—automation—is a total game-changer. It means that when someone’s role changes or they leave the company, their access is updated everywhere, instantly. No manual cleanup, no forgotten accounts. Diving into concepts like Just-in-Time provisioning can give you an even more advanced way to grant temporary, context-aware access to these tools, tightening your security even further.
Addressing IoT and Connected Devices
The Internet of Things (IoT) has opened the floodgates to a whole new fleet of devices on your network. We’re talking about everything from smart security cameras to environmental sensors in the server room. The scary part is that many of these devices ship with laughably weak default credentials and are rarely, if ever, updated. They’re low-hanging fruit for attackers.
Your access control policy has to extend to these non-traditional endpoints. The two most critical additions you can make are sections on device hardening and network segmentation.
For example, your policy should clearly state:
- “All IoT devices must have their default credentials changed before being connected to the corporate network.”
- “IoT devices must be placed on a segregated network segment, isolated from critical business systems, to limit potential damage in case of a compromise.”
By treating these devices as inherently untrusted and walling them off, you can get all the benefits of their functionality without exposing your core infrastructure to a ton of unnecessary risk. This is how you turn your policy from a static document into a living, breathing guide that truly reflects your modern tech stack.
Frequently Asked Questions About Access Control Policies
Even with the best access control policy template in hand, practical questions always pop up during implementation. It’s just the nature of the beast. Having clear, experience-backed answers ready is what turns your policy from a static document into a living, breathing part of your security strategy.
Let’s dive into some of the most common questions I hear from teams on the ground.
How Often Should We Review and Update Our Access Control Policy?
Think of your access control policy as a living document, not a “set it and forget it” task. You absolutely need a formal, comprehensive review at least annually. This keeps it in lockstep with your security goals and any new compliance headaches that have emerged.
But an annual review is just the baseline. The real triggers for a review are major organizational shifts. Did you just adopt a new CRM? Launch a new cloud service? Overhaul a core business operation? Or, most critically, did you just navigate a security incident? Any of these events mean it’s time to pull out the policy and make sure it still reflects your current tech stack and threat landscape.
What Is the Difference Between Authorization and Authentication?
This is a classic point of confusion, but getting it right is fundamental. I always explain it like getting into a secure office building.
- Authentication is proving you are who you claim to be. It’s your keycard, your password, or your fingerprint. It’s the security guard checking your ID at the front door and nodding you through.
- Authorization is what you’re allowed to do once you’re inside. That same keycard that got you through the main door (authentication) won’t get you into the CEO’s office or the server room (authorization).
A solid policy has to define the rules for both. It should mandate strong Multi-Factor Authentication (MFA) to even get on the network, but it also has to be crystal clear that only the finance team is authorized to touch the payroll systems.
Can a Small Business Really Use This Template?
Absolutely. In fact, we designed this access control policy template specifically to be scalable. If you’re a small business or a startup, you might simplify some areas. For instance, your “Roles and Responsibilities” section will be much shorter if one person wears multiple hats.
The core principles, however, are just as critical for a five-person company as they are for a 5,000-person enterprise. Principles like least privilege, formal access request procedures, and mandatory access reviews protect your business regardless of its size.
Start with this template as your foundation and tailor the complexity to what fits your team right now. The beauty is that as your business grows, the policy can easily grow with you. You won’t have to rip it up and start from scratch.
How Do We Manage Access for Complex Tools Like Jira?
Ah, Jira. Managing permissions in powerful, sprawling platforms like this is the perfect real-world test for your policy. Without a guiding policy, permissions in tools like Jira can devolve into an insecure, tangled mess faster than you can say “admin privileges.”
Your policy provides the “why” that governs the “how” of the tool’s specific settings.
For example, your policy would state that all access must be role-based (RBAC). In Jira, this means you stop assigning permissions to individuals. Instead, you create specific user groups like “Developers,” “QA Testers,” and “Project Managers,” and then assign project roles and permission schemes to those groups. It’s a far more manageable—and secure—way to operate. For a deeper dive, our article on automating user management in Jira shows exactly how to apply these policy-driven principles in the real world.
Ready to stop overpaying for Atlassian licenses and automate your user lifecycle management? resolution Reichert Network Solutions has you covered. Our User Deactivator for Jira automatically identifies and disables inactive users, saving you up to 20% on license costs while tightening security.
Discover how User Deactivator can optimize your Atlassian environment
