When you implement a self service password reset for Active directory, you’re not just adding a new feature. You’re fundamentally changing how your organization handles one of the most common IT headaches, giving users the power to solve their own login issues instantly. This move away from manual resets drastically cuts down on IT helpdesk tickets and gives a real boost to company-wide productivity.
For any modern IT team trying to build a more efficient and secure environment, this is a foundational step.
Why SSPR Is a Must-Have for Modern IT Departments
Let’s be honest: manual password resets are a huge time sink for any IT department. They create a never-ending stream of low-value, repetitive tickets that constantly interrupt the strategic projects that actually move the business forward. It’s frustrating for your IT staff, and it’s frustrating for the employees waiting for help.
Every single forgotten password becomes another helpdesk ticket, another phone call, and more lost time for everyone. This is exactly why rolling out a self service password reset (SSPR) for Active Directory has become less of a “nice-to-have” and more of a core business necessity.

The benefits go far beyond just convenience, too. Implementing SSPR creates a ripple effect of positive changes across the entire organization.
Reclaiming Productivity and Slashing Costs
Think about it. When employees can reset their own passwords in just a couple of minutes, they get back to their work almost immediately. That downtime spent waiting for IT to intervene? Gone. This directly translates into reclaimed productivity across the board.
For the IT team, the impact is just as significant. The huge reduction in password-related tickets frees them up to focus on what really matters—critical initiatives like infrastructure upgrades, security enhancements, and long-term planning.
The numbers back this up. A 2023 analysis of over 700 organizations using an SSPR solution found they saved an average of $64,610 per year. That breaks down to about $136 per user. When you factor in both the cost of IT support time and the lost productivity from employees, the return on investment is a no-brainer.
“Moving to SSPR is one of the highest-impact, lowest-effort changes an IT department can make. You’re not just closing tickets faster; you’re giving valuable time back to every single person in the company.”
Strengthening Your Security Posture
A properly implemented SSPR system is a big win for security. By forcing users to verify their identity through multiple factors—like a code from a mobile app, a biometric scan, or a physical security key—you’re creating a much tougher barrier against unauthorized access. It’s far more secure than a simple helpdesk call where an employee’s identity might be confirmed with easily discoverable information.
This whole process shifts password management into a secure, auditable framework that’s easier to monitor and control. It also fits perfectly into a larger identity management strategy. In fact, if you’re looking to tighten up your defenses, you should check out our deep dive into how Single Sign-On acts as the first line of defense for passwords.
The table below gives a quick snapshot of the key advantages you can expect.
Key Benefits of Implementing SSPR for Active Directory
Here’s a quick summary of the primary advantages your organization gains by enabling self-service password reset.
| Benefit Area | Impact on Your Organization |
|---|---|
| Cost Reduction | Significantly lowers operational costs by reducing helpdesk call volume and IT staff workload. |
| Increased Productivity | Minimizes employee downtime, allowing them to resolve access issues instantly and resume work. |
| Enhanced Security | Enforces multi-factor authentication for password changes, reducing social engineering risks. |
| Improved User Experience | Empowers employees with 24/7 access to reset their own passwords, boosting satisfaction. |
Ultimately, adopting SSPR isn’t just about fixing a process; it’s about making your organization more agile, secure, and productive from the ground up.
Choosing Between Native and Third-Party SSPR Tools
When it’s time to implement a self-service password reset for Active Directory, you’ll hit a fork in the road pretty quickly. Do you stick with the native tools Microsoft provides, or is it smarter to bring in a specialized third-party solution? The honest answer is: it depends entirely on your company’s specific needs, security posture, and the tech you already have in place.

Microsoft’s native SSPR, which you’ll primarily find through Azure AD, offers a convenient and deeply integrated starting point. For organizations all-in on the Microsoft 365 ecosystem, this often feels like the most direct route. It covers the basics without adding another vendor to your list.
But convenience can come with strings attached. Native tools might not give you the granular control or advanced features that larger or more regulated businesses absolutely need.
Evaluating Native Microsoft SSPR
The biggest selling point for Microsoft’s built-in SSPR is its seamless fit with Azure AD and Microsoft 365. If your environment is mostly in the cloud, flipping it on is pretty straightforward.
But you have to weigh the potential trade-offs:
- Limited MFA Options: It works great with the Microsoft Authenticator app and standard SMS/email codes. However, if you need to support more advanced or non-Microsoft MFA methods—like specific hardware tokens or different biometric authenticators—you might find your options are limited.
- On-Premise Complexity: This is a big one for hybrid environments. Getting SSPR to play nice with a legacy on-premise Active Directory means shelling out for Azure AD Premium licenses to enable the password writeback feature. This can introduce unexpected costs and headaches.
- Customization Constraints: The user interface and the entire password reset workflow don’t offer much in the way of branding or customization. This might seem minor, but a clunky or unfamiliar process can seriously hurt user adoption.
In short, native tools offer a solid foundation. But if your security policy demands specific, non-Microsoft authenticators or you need deep integration with other on-premise legacy systems, you may quickly find yourself hitting a wall.
The Case for Third-Party Solutions
This is exactly where dedicated third-party SSPR tools come into play. These solutions are purpose-built to solve the password reset problem, and they do so with a much broader and deeper feature set that fills the gaps often left by native options.
Specialized tools typically shine in a few key areas:
- Broader MFA Support: They often integrate with a huge array of authentication methods, from biometrics and various hardware tokens (like YubiKey) to a wide range of third-party authenticator apps. This gives you the flexibility to meet even the most stringent security requirements.
- Enhanced User Experience: Third-party solutions frequently offer highly customizable user portals. You can brand them to match your company’s look and feel, which makes the whole process more intuitive and drives up user adoption rates.
- Robust Auditing and Reporting: These tools provide detailed logs and analytics, making it much easier to track SSPR usage, spot potential security issues, and prove compliance to auditors.
- Superior On-Premise Integration: Many are designed from the ground up to work flawlessly in complex hybrid environments. They offer better support for legacy applications and on-premise Active Directory, often without the licensing hurdles of the native approach.
Comparison of SSPR Solutions for Active Directory
Deciding between a familiar, integrated tool and a powerful, specialized one can be tough. I’ve put together this table to quickly compare the key differences between Microsoft’s native offering and what you can typically expect from a dedicated third-party SSPR solution.
| Feature | Native Microsoft SSPR | Third-Party SSPR Solutions |
|---|---|---|
| Integration | Deeply integrated with Azure AD and Microsoft 365. Best for cloud-first environments. | Designed for flexibility, with broad support for on-premise AD, hybrid, and cloud. |
| MFA Options | Primarily supports Microsoft-centric methods (Authenticator app, SMS, email). | Extensive support for a wide range of third-party MFA, including hardware tokens. |
| Customization | Limited branding and workflow customization options. | Highly customizable user portals and workflows for a seamless user experience. |
| On-Premise Functionality | Requires Azure AD Premium licenses for password writeback to on-premise AD. | Often includes robust on-premise support out-of-the-box without extra license fees. |
| Reporting & Auditing | Provides basic logging within the Azure portal. | Offers advanced, detailed reporting and analytics for security and compliance. |
| Cost | Included with certain Azure AD tiers but can have hidden costs (e.g., Premium P1/P2). | Typically involves a separate license fee but can offer a better total cost of ownership. |
Ultimately, the native tools are a great starting point for smaller, cloud-focused organizations. But as your security and integration needs grow more complex, the investment in a dedicated third-party tool often pays for itself through enhanced security, better user adoption, and reduced IT workload.
The complexity of Active Directory often puts a real strain on IT teams, and these bottlenecks can weaken organizational resilience and frustrate employees. That’s why many organizations opt for more powerful solutions. Choosing the right tool isn’t just about resetting passwords; it’s about building a secure, efficient, and user-friendly identity management foundation. Further exploring broader topics like identity management and provisioning can help place SSPR within your overall IT strategy.
A Practical Guide to SSPR Implementation
Alright, let’s move from theory to action. This is where we roll up our sleeves and get your self-service password reset for Active Directory solution off the ground. A successful implementation isn’t just about flipping a switch; it’s about thoughtful preparation and a phased approach that makes the transition smooth for everyone involved—both your IT team and your end-users.
We’ll start with the foundational work. These are the essential checks and configurations you need to nail down before even thinking about going live. Getting this initial phase right is absolutely critical for avoiding the common pitfalls that can derail an otherwise solid rollout.
Laying the Groundwork for Success
Before you even dream of enabling SSPR for a single user, you have to make sure your Active Directory environment is ready. A crucial first step is to confirm your AD functional level is compatible with whatever SSPR tool you’ve chosen, whether that’s the native Azure AD SSPR or a third-party solution.
Another piece of the puzzle, especially in hybrid environments, is licensing. This one trips people up all the time. If you’re using Microsoft’s native tools, features like password writeback—which is what syncs password changes from the cloud back to your on-premises AD—require Azure AD Premium P1 or P2 licenses. Overlooking this can bring your entire project to a screeching halt.
Pro Tip: Don’t skip the prep work. Seriously. A few hours spent verifying prerequisites and licensing upfront can save you days of troubleshooting nasty synchronization or permission issues down the line.
With the backend sorted, the next step is configuring the authentication methods users will rely on to prove who they are. This is always a balancing act between security and convenience.
- High Security: Methods like the Microsoft Authenticator app (especially with number matching) or FIDO2 security keys offer the strongest possible protection against phishing and account takeovers.
- Convenience: Things like SMS or email codes are familiar to users, which helps with adoption. But they’re considered less secure due to risks like SIM swapping.
- Avoid: Security questions are widely seen as the weakest link in the chain. If you absolutely must use them, make sure they’re combined with other, much stronger factors.
This visual shows the basic flow for a user once SSPR is active, from the initial verification step all the way to the final directory update.
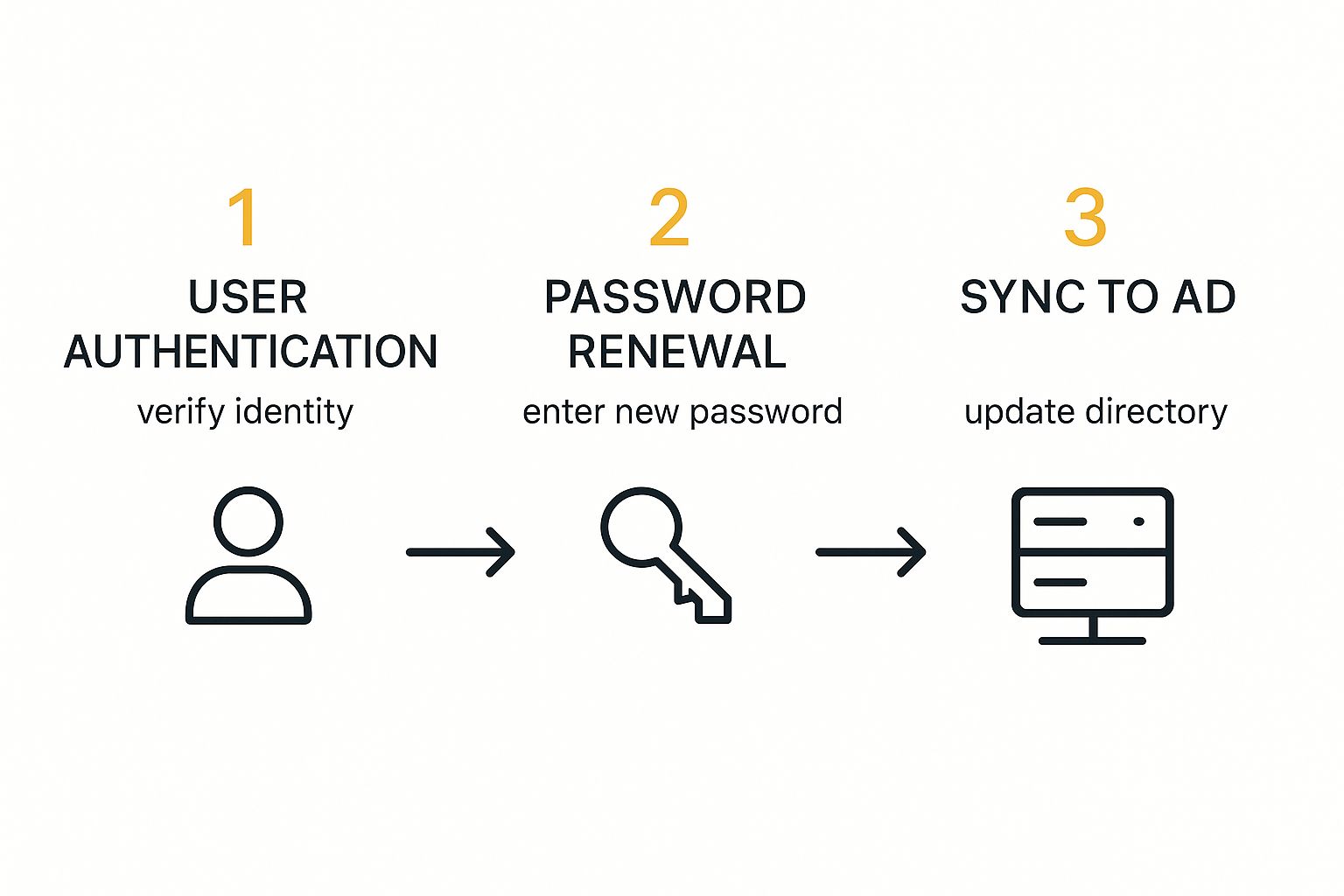
Think of it as a secure, three-stage handshake. The system has to confirm a user’s identity beyond a doubt before handing over the keys to change their password.
Staging Your Rollout with a Pilot Group
A “big bang” rollout for SSPR is almost never a good idea. The much smarter approach is to start small with a pilot group. This group should be a good mix of people—some tech-savvy folks from the IT department, a few from other business units, and maybe an executive or two to get their buy-in early.
By targeting a specific user group first, you can achieve a few key things:
- Gather Real-World Feedback: This is your chance to discover what works and what doesn’t in a controlled environment. Is the enrollment portal intuitive? Are the instructions clear enough for non-technical users?
- Identify Technical Glitches: You can uncover any unforeseen issues with specific user configurations, group policies, or application integrations before they impact the entire organization.
- Refine Your Communication Plan: Use the pilot group’s experience to fine-tune your announcement emails, training materials, and support documentation for the full-scale rollout.
Once you’ve successfully wrapped up the pilot, you can start expanding the SSPR deployment to the rest of the organization in phases. This methodical approach leads to a much smoother and more successful implementation. It also aligns perfectly with best practices for managing the entire user lifecycle, from onboarding to offboarding.
For a broader perspective on automated user management, check out our guide on the essentials of user provisioning and deprovisioning. This controlled strategy minimizes disruption and maximizes adoption.
Securing Your SSPR Implementation from Day One
Rolling out a self service password reset for active directory solution is a big step forward. It’s also a significant security event. Get it right, and you’ve empowered your users and strengthened your defenses. Get it wrong, and you’ve just created a shiny new attack vector for bad actors.
Securing your SSPR implementation from the very beginning isn’t just a good idea; it’s non-negotiable. The biggest mistake I see is teams treating SSPR as a simple convenience feature. It’s a direct gateway to user accounts, and you have to fortify it. That starts with moving past outdated, easily compromised verification methods.
Ditching Guessable Security Questions
The era of using “What was your first pet’s name?” as a valid security measure is long over. Honestly, it was never a great idea. This kind of information is often plastered all over social media or can be figured out with basic social engineering. Relying on these knowledge-based answers (KBAs) is an open invitation for an account takeover.
Your security strategy needs to be built on a foundation of strong, phishing-resistant multi-factor authentication (MFA).
These methods prove identity through something the user has, not just something they know:
- Authenticator Apps: Push notifications from apps like Microsoft Authenticator require the user to physically have their registered device in hand.
- FIDO2 Security Keys: These physical hardware keys offer the highest level of security. They make it nearly impossible for a remote attacker to compromise an account.
- Biometrics: Using fingerprints or facial recognition adds another robust layer of identity verification that’s unique to the user.
By enforcing strong MFA, you dramatically slash the risk of an attacker successfully exploiting the SSPR process. This isn’t just a best practice; it’s your primary line of defense against modern threats like SIM-swapping, where attackers hijack a user’s phone number to intercept SMS codes.
A poorly configured SSPR system can be worse than no SSPR at all. The goal is to make it easy for legitimate users and nearly impossible for attackers. That balance is struck with strong, modern authentication.
Continuous Monitoring and User Education
Your job isn’t done once SSPR is live. You have to actively monitor for suspicious activity. Think about it: a sudden spike in password reset attempts for a single user or a cluster of resets from an unusual location could be a red flag for a brute-force attack. Set up alerts for these anomalies so your security team can jump on them immediately.
The human element is just as critical. Many organizations are hesitant to fully deploy SSPR because they’re worried about security. In fact, a 2023 study revealed that a staggering 39% of Microsoft tenants had SSPR disabled for over 75% of their users. Why? Often because attackers have successfully exploited weak setups in the past. You can read more about these breach findings from Obsidian Security.
This is exactly why user education is paramount. Train your employees to:
- Recognize phishing attempts related to SSPR enrollment.
- Never, ever approve MFA pushes they did not initiate.
- Report any suspicious password reset notifications right away.
This proactive approach works hand-in-hand with your technical controls, creating a much more resilient security posture. Managing user access securely is an ongoing process, and concepts like just-in-time provisioning can further tighten security by granting permissions only when needed, minimizing the potential attack surface. By combining robust technical safeguards with an aware user base, you ensure your SSPR implementation is a security asset, not a liability.
How to Drive Adoption and Measure SSPR Success
Even the most technically sound self service password reset for active directory tool is basically useless if your employees don’t actually use it. I’ve seen this happen before. The real win isn’t in the technical setup; it’s in how you handle the people and the process. Shifting your focus from the backend configuration to a user-centric deployment is where you’ll unlock the tool’s genuine value.

This all starts with a solid communication plan. Please don’t just flip the switch and hope everyone figures it out. You need to build awareness and gently guide users through the change, making the whole thing feel like a helpful upgrade, not another corporate chore.
Crafting Your Communication and Rollout Plan
My advice? Always start with a phased rollout. As we talked about earlier, a pilot group is fantastic for working out the technical kinks, but it’s also your first real test for user communications. Use their feedback to polish your messaging before you push it out to the entire company.
When you do communicate, keep it simple, clear, and focused on the benefits for the employee.
- Initial Announcement: Send out an email about a week or two before launch. Briefly explain what SSPR is, why the company is implementing it (think less waiting on IT, better security), and what they can expect.
- Launch Day Email: On the big day, send an email with a direct link to the enrollment portal. Your instructions need to be dead simple. Use screenshots or even a short GIF showing how quick the registration process is.
- Follow-Up Reminders: After about a week, give a gentle nudge to users who haven’t registered yet. Remind them of the convenience of being able to reset their own password anytime, day or night.
The goal here is to eliminate any resistance by making enrollment feel both effortless and essential. Frame it as a tool that gives employees more control and saves them time—because, frankly, it does.
Measuring What Matters: Proving Your ROI
So, how do you prove the project was worth it? By tracking the right numbers. Your leadership team is going to want to see a clear return on investment (ROI), and the great thing about SSPR is that the data is surprisingly easy to gather. You want to focus on tangible outcomes that scream business value.
Here are the key metrics I always monitor:
| Metric | How to Track It | Why It Matters |
|---|---|---|
| Helpdesk Ticket Reduction | Compare the volume of password-related tickets before and after you launch SSPR. | This is your single biggest cost-saving indicator. It’s a direct measure of the reduced workload on your IT team. |
| User Adoption Rate | Keep an eye on the percentage of users who have successfully enrolled in the new system. | A high adoption rate is proof that the tool is actually being used and its benefits are being realized company-wide. |
| Time to Resolution | Measure the average time it takes a user to reset their own password versus how long they used to wait for IT. | This metric is gold. It perfectly highlights the massive productivity gains for employees across the board. |
When you present this data, you’re not just showing that a new system works; you’re proving its financial and operational impact. Success in this project relies on having a clear view of your user base, a principle that applies to many other administrative tasks. For example, similar efficiency gains can be found when you https://www.resolution.de/post/automating-user-management-in-jira/ to streamline other processes.
Got Questions About SSPR? We’ve Got Answers
Even the best-laid plans run into questions, especially when you’re rolling out something as critical as SSPR. We get a lot of the same queries from folks in the trenches, so we’ve put together some quick, straightforward answers to the most common ones.
Think of this as your go-to cheat sheet for sorting out those last-minute details before you go live.
What Licenses Do I Actually Need?
This is probably the number one question we hear, especially for hybrid environments. It’s easy to get tangled up in Microsoft’s licensing.
For a purely cloud-based setup, the basic SSPR features are baked into most Microsoft 365 subscriptions. But if you’re running a hybrid environment—and most of us are—the game changes. The absolute must-have feature is password writeback, which is what syncs a user’s new password from the cloud back to your on-premise Active Directory.
To get password writeback, you need Azure AD Premium P1 or P2 licenses for your users. There’s no getting around this; it’s a hard requirement for any hybrid SSPR implementation.
And how do you get people to actually sign up? You can force their hand (in a good way). Just head into the Azure portal’s password reset settings and flip the “Require users to register when signing in?” switch to “Yes.” It’s a simple technical fix, but make sure you back it up with a solid communication plan so nobody is caught off guard.
Which Authentication Methods Are Genuinely Secure?
The next big conversation is always around security. What’s the best way for a user to prove they are who they say they are without calling the help desk?
Your strongest bets are always rooted in multi-factor authentication (MFA). We strongly recommend pushing users toward these two:
- Microsoft Authenticator App: This is our top pick. It uses push notifications and one-time passcodes tied directly to a user’s device, making it both convenient and secure.
- FIDO2 Security Keys: For the highest level of protection, nothing beats a physical hardware key. They’re practically bulletproof against phishing and other remote attacks.
A quick word of caution: While things like SMS and email codes are easy, they are far more susceptible to modern attacks like phishing and SIM-swapping. And security questions? They’re a relic of the past. Avoid them completely if you can.
Setting up SSPR is also the perfect time to review your broader password policies. It’s worth looking into the current best practices for password change frequency to make sure your entire security posture is up to snuff.
Are you looking to optimize your Atlassian user management and cut down on license costs? resolution Reichert Network Solutions offers User Deactivator, an app that automatically identifies and disables inactive users in Jira, Confluence, and Bitbucket. Learn how you can save costs and streamline administration by visiting https://www.resolution.de/user-deactivator-overview.