Think of a data breach response plan as the formal playbook your organization will follow, play-by-play, during and after a security incident. It’s a detailed guide designed to minimize the damage—from financial bleeding to a tarnished reputation—by making sure your reaction is swift, coordinated, and effective.
Frankly, going without one isn't just being unprepared; it's inviting chaos when the inevitable happens.
Why A Response Plan Is Non-Negotiable

In the current threat landscape, a security incident is a matter of 'when,' not 'if.' This simple truth elevates a data breach response plan from just another IT document to a core strategy for business survival. Believing you're too small to be a target or too secure to be breached is a dangerous and costly assumption.
The fallout from being unprepared goes far beyond the initial technical glitch. It creates a ripple effect that can seriously destabilize your entire organization.
The True Cost of Inaction
Without a plan, the financial gut punch is immediate and severe. Costs start piling up from every direction: emergency IT contractors, urgent legal consultations, regulatory fines, and PR teams trying to manage the crisis. The longer it takes you to get a handle on the breach, the higher those costs climb. We're talking millions, on average—a figure that can easily cripple a business.
Reputational damage is often even harder to fix. A poorly handled incident shatters customer trust, and winning that back is a long, uphill battle. This can trigger customer churn, make it harder to attract new talent, and devalue your brand for years to come.
Then there's the operational meltdown. Critical systems might be offline for days or weeks, pulling your team away from growth and innovation and into full-time damage control. It throws everyone into a reactive, high-stress state, forcing them to make critical decisions under immense pressure.
A well-documented plan transforms panic into process. It provides clarity when everything feels chaotic, ensuring your team can act decisively to protect the business, its customers, and its future.
To give you a better sense of what this plan should cover, here’s a quick breakdown of its essential pillars.
Core Components of a Data Breach Response Plan
| Component | Objective |
|---|---|
| Preparation | Identify key roles, responsibilities, and resources before an incident occurs. |
| Detection & Analysis | Define how to identify a breach, determine its scope, and assess the immediate impact. |
| Containment | Outline immediate steps to isolate affected systems and prevent further data loss. |
| Eradication & Recovery | Detail the process for removing the threat and securely restoring systems. |
| Post-Incident Activity | Establish workflows for forensic analysis, communication, and process improvement. |
Each of these components works together to create a comprehensive and resilient defense.
The Global Scale of Data Exposure
The sheer volume of incidents happening worldwide really underscores why this is so critical. The statistics are staggering. Since 2004, there have been over 23 billion breached accounts globally, affecting about 7.7 billion unique email addresses. Think about that—on average, every single email address has been compromised roughly three times. This isn't a minor issue; it's a massive, widespread privacy crisis. You can dig deeper into these numbers by exploring the latest data breach trends.
This guide is designed to move you beyond fear and into action. We’ll walk through the essential components every effective data breach response plan needs, offering practical, step-by-step advice to build a framework that truly protects your organization. This isn't just about ticking a compliance box; it's about survival.
Assembling Your Incident Response Team

Let's be clear: a great data breach response plan isn't a document you pull off a shelf. It’s a team of real people who know exactly what to do when things go south. While the tech and processes matter, it's the people who execute the strategy under fire. Building this team isn't just an IT job; it demands a cross-functional group that can handle the technical, legal, and reputational fallout of an incident.
When a breach hits, ambiguity is your biggest enemy. Without clearly defined roles, your team will scramble. You'll see duplicated efforts, and worse, critical tasks will be missed entirely. The goal here is to create a structure that functions like a well-oiled machine under extreme pressure, turning potential chaos into a coordinated, efficient response. This is the foundation of a solid incident management process.
Defining Core Roles and Responsibilities
Your incident response team (IRT) has to extend far beyond the server room. Yes, you need your technical wizards to contain the threat, but a breach has business-level consequences that require a much wider skillset.
Here are the essential roles your team should have:
- Incident Manager: Think of this person as the quarterback. They coordinate the entire response, make sure tasks are assigned, and serve as the single point of contact for leadership. This isn’t necessarily your top tech person; it’s someone with killer organizational and communication skills.
- Technical Lead: This is your top security and IT expert. They lead the hands-on investigation, guide containment and eradication efforts, and are responsible for the forensic analysis to find the root cause.
- Communications Lead: Usually from your marketing or PR department, this person manages all internal and external messaging. They work hand-in-glove with legal to draft statements for customers, employees, and the media, balancing transparency with protecting the company.
- Legal Counsel: Having in-house or external lawyers on call is non-negotiable. They advise on regulatory deadlines (like GDPR's 72-hour rule), help preserve evidence under attorney-client privilege, and review every public-facing communication to minimize legal risk.
- HR Representative: If employee data is involved, HR is absolutely critical. They handle internal communications, address staff concerns, and manage any investigations related to insider threats.
- Executive Leadership Sponsor: You need a C-level executive to provide top-down support, approve emergency resources and spending, and keep the board of directors in the loop.
This structure ensures you've got every angle of the crisis covered—from patching the vulnerability to managing customer trust. To see how these roles fit into a larger framework, you can learn more about building a robust incident management process that complements your team structure.
A common failure point is not having a clearly designated backup for each role. If your lead investigator is on vacation when an incident occurs, who steps in? Document primary and secondary contacts for every position.
Establishing a Clear Chain of Command
In a crisis, you need to make decisions fast. A flat or confusing hierarchy leads to analysis paralysis when every second counts. Your response plan must explicitly map out the chain of command. It should detail who reports to whom and who has the authority to make critical calls, like taking a system offline or hiring a third-party forensics firm.
This isn't about adding bureaucracy; it's about building speed. A security analyst shouldn't have to wait for three levels of approval to isolate a compromised server. The plan should empower them to act based on pre-approved protocols, eliminating bottlenecks and saving precious time.
Training and Readiness
Just having a team on paper isn't enough. Regular training is what turns a group of individuals into an effective response unit. You wouldn't send a firefighter into a blaze without practice, and the same goes for your IRT.
Tabletop Exercises: Run these at least once a year. Give the team a realistic breach scenario—a ransomware attack, a stolen employee laptop—and make them walk through the response plan step-by-step. I guarantee these exercises will uncover gaps in your plan, communication breakdowns, or resource shortages that you can fix before a real crisis hits.
Contact List Maintenance: This sounds painfully simple, but it's so often overlooked. Keep a secure, up-to-date contact list for every single IRT member, including their after-hours phone numbers. This list should also include key external contacts: your cybersecurity insurance provider, legal counsel, and law enforcement. And make sure it's accessible even if your primary systems are down.
The Four Phases of Incident Response
A solid data breach response plan isn't about having a single, giant panic button. It’s about breaking down the chaos of a security incident into a clear, manageable lifecycle. When the pressure is on, you don't want to be inventing a process on the fly.
Instead, think of your response as a logical progression through four distinct phases. This framework, which is widely adopted from industry standards like those from NIST, gives your team a roadmap to follow, ensuring nothing critical gets missed. Each phase has its own goal, moving you from being prepared, to reacting and containing the threat, and finally, to learning and getting better.
Phase 1: Preparation
Honestly, the most important work you'll do on your incident response happens before anything goes wrong. This is the proactive part, where you lay all the groundwork so your team can act decisively instead of scrambling for answers. It's where you build the muscle memory for a crisis.
So, what does good preparation look like?
- Finalize Your Team: Get your Incident Response Team (IRT) locked in. Everyone needs to know their exact role, their responsibilities, and—just as important—who their backup is if they're unavailable.
- Get Your Tools and Access Ready: Make sure the team has access to everything they'll need. This means security tools like endpoint detection and response (EDR) systems and forensic software, but it also means having logins and contact lists for third-party vendors—think your cloud provider or a cybersecurity law firm—ready to go.
- Run Drills: You have to practice. Regular tabletop exercises are invaluable. Simulating a breach is the best way to find the weak spots in your plan, uncover communication gaps, and give your team the confidence to actually perform their roles under real stress.
Think of it as setting the stage. If you skip this, every other phase becomes exponentially harder, more expensive, and far more chaotic.
Phase 2: Detection and Analysis
This is it—the moment your plan gets triggered. This phase kicks off the second a potential security incident is spotted, whether that's from an automated alert, a worried user, or even a tip from an outside party. The two goals here are simple: be fast and be accurate.
This is tougher than it sounds. Recent data from 2023 and early 2024 showed that a staggering 40% of data breaches were first identified by external sources, not the company's own security team. With the average time to just identify a breach sitting at 194 days, it’s clear that a lot of organizations are flying blind.
Once an alert is flagged, your technical lead needs to jump on it. The first step is to quickly figure out if you're dealing with a genuine threat or just a false positive. This involves piecing together data from different places—network logs, endpoint alerts, user activity—to get a handle on the intrusion's nature and scope. Is this a single piece of malware on one laptop, or is it a full-blown ransomware attack spreading across the network? The answer dictates everything that happens next.
Phase 3: Containment, Eradication, and Recovery
Welcome to the most hands-on, high-stakes part of the job. This is where your team is actively in the trenches, working to stop the bleeding, kick the threat out, and get things back to normal. This phase is really three distinct actions rolled into one.
This simple flow shows how to tackle this part of your data breach response plan.
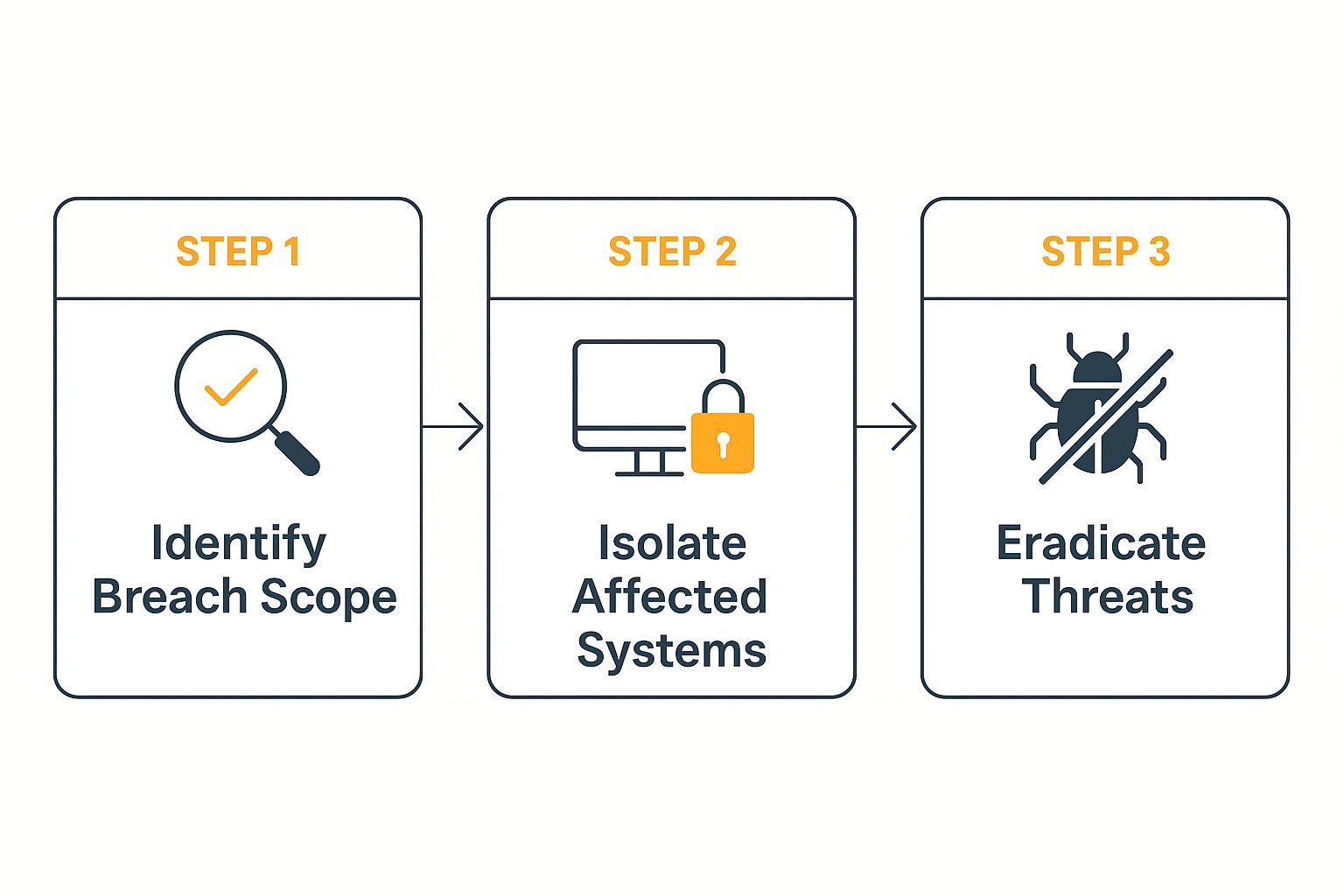
Following this process ensures you stop the attack from spreading before you try to clean up, which is critical for preventing reinfection.
- Containment: Your immediate priority is to isolate the affected systems. You have to stop the attacker from moving laterally across your network. This could be as simple as disconnecting a server from the internet, or it might involve disabling compromised user accounts and segmenting parts of your network. The goal is to stop the damage from getting any worse.
- Eradication: Once the threat is contained, the team can focus on getting it out of your environment for good. This means deleting malware, patching the vulnerability the attacker used to get in, and triple-checking that they didn't leave any backdoors behind.
- Recovery: With the threat gone, you can start the process of securely restoring the affected systems and data from clean backups. This has to be done carefully, often in a segmented environment, to make absolutely sure you aren't accidentally reintroducing the problem.
A critical note for this phase: preserve evidence. Document every single action you take. These logs are not only vital for your own post-incident investigation but are often essential for legal and compliance reasons.
Phase 4: Post-Incident Recovery
The immediate fire is out, but your work isn't done. This final phase is all about learning from what just happened so you can build a stronger defense for the future. You could argue this is the most important phase for your long-term security posture.
The main event here is a thorough post-mortem or lessons-learned meeting. Get the entire IRT and key stakeholders in a room to talk through what happened, what went well, and what could have been done better. It’s crucial that this is a blameless analysis focused on improving the process, not pointing fingers.
You need to answer some tough questions:
- What was the actual root cause of the breach?
- How could we have spotted this sooner?
- Did our communication plan work the way it was supposed to?
- Do we have gaps in our tools or our team's training?
The answers should feed directly back into your data breach response plan. This creates a powerful feedback loop of continuous improvement, making your organization more resilient with every incident. For more on building these kinds of essential processes, you can explore our guide on incident management best practices.
Putting Your Plan into Action with Atlassian
A documented data breach response plan is a great start, but let's be honest: a PDF gathering dust on a shared drive won't help you when things go sideways. To be truly effective, your plan needs to be a living, breathing workflow your team can execute flawlessly under extreme pressure. This is where the Atlassian suite absolutely shines, turning theory into coordinated action.
By wiring up tools like Jira, Confluence, and Opsgenie, you can build a genuine command center for incident response. This integrated ecosystem automates the tedious stuff, tracks progress where everyone can see it, and keeps your documentation right where you need it. You'll move from chaotic, ad-hoc reactions to a disciplined, process-driven response.
Centralizing Incidents with Jira Service Management
Your first step is to carve out a dedicated space to manage security incidents. I’ve found that Jira Service Management is perfect for this, acting as the single source of truth for any event. Set up a specific project just for your incident response team (IRT), complete with a custom workflow that perfectly mirrors the phases of your response plan.
This project becomes the nerve center for all incident-related activity. Every incident gets its own ticket, meticulously capturing every detail from the moment of detection to the final sign-off. This isn't just about task tracking; it's about creating a bulletproof, auditable record of every single action taken—something that's invaluable for post-mortems and satisfying compliance auditors.
Imagine this scenario, which I've seen play out many times:
- A monitoring tool flags suspicious login activity and automatically fires an alert.
- That alert instantly creates a high-priority incident ticket in your IRT's Jira project.
- The ticket is already populated with key details like the affected system and the detection timestamp.
- Based on your pre-set rules, the right team members are automatically assigned and notified.
This level of automation immediately shaves critical minutes off your response time. The frantic, manual scramble to log the issue and hunt down the right people is just… gone. Instead, everyone has instant clarity, often visualized in a clean incident management dashboard.
A centralized view like the one above is non-negotiable. It gives everyone the situational awareness needed to make smart decisions when the pressure is on.
Automating Alerts with Opsgenie
In the first few moments of a breach, speed is everything. You simply can't afford to waste time with manual phone trees or sending emails into a potential black hole. This is where Opsgenie becomes a true game-changer for your data breach response plan. It plugs directly into your monitoring tools and your Jira project to take charge of alerting and on-call management.
When that incident ticket pops up in Jira, Opsgenie can kick off a sophisticated, automated alert sequence. It checks your on-call schedule and pings the designated engineer using their preferred contact method—whether that's a push notification, an SMS, or a direct phone call. If the primary person doesn't acknowledge the alert within a configured timeframe, Opsgenie automatically escalates it to the next person in line.
This simple workflow guarantees that a human is actively engaged with the incident in minutes, not hours. It completely removes the single point of failure that comes with manual notifications and builds accountability from the very start.
Creating a Dynamic Playbook with Confluence
If Jira is tracking the "what" and "who," then Confluence is where you keep the "how." Your Confluence space should be the home for your dynamic incident response playbooks. And I mean dynamic—this isn't just a place to paste a static copy of your plan. It's an interactive, living resource.
For every type of incident you might face, you can build a corresponding runbook template in Confluence. The moment a major incident is declared in Jira, an automation rule can spin up a new Confluence page from the right template.
This new page becomes the collaborative workspace for that specific incident, neatly linked back to the master Jira ticket. This is where the team can:
- Run through step-by-step containment checklists.
- Document their findings and observations in real time.
- Collaboratively draft and approve communications for internal and external audiences.
- Conduct the post-incident review and capture every lesson learned.
What you end up with is a self-contained, comprehensive record for every event. Six months down the line, you have the Jira ticket showing the precise timeline and the Confluence page containing the full narrative, all cross-linked and easy to find.
Many teams also pull in customer data from their CRM to get a full picture. For those looking to connect disparate systems, a HubSpot Jira integration can be a powerful way to streamline communications, especially when customer data is at risk. This ensures that your support, security, and comms teams are all working from the same up-to-date information.
Managing Post-Breach Communication and Recovery

You’ve contained the immediate fire of a security breach, but the real work is just beginning. Once the threat is neutralized, your data breach response plan pivots to two equally critical, parallel tracks: transparent communication and meticulous technical recovery.
Frankly, how you handle this phase defines the long-term damage. It will either salvage customer trust and your brand's reputation or shatter them completely. This is no time for radio silence.
At the same time, your technical teams are in a race to not only restore systems but also to bolt the door the attacker walked through.
Navigating Stakeholder Communication
The first order of business is crafting clear, honest, and timely messages for every group affected by the breach. This is not a one-size-fits-all email blast. Each audience has different needs, and your communication has to hit the right note for each one.
You’ll be speaking to a few key groups:
- Affected Customers: They need to know what happened, what data was exposed, and what you're doing to protect them. Be direct. Offer support like credit monitoring if it's relevant, and give them a clear way to get answers.
- Regulatory Bodies: Regulations like GDPR have tight, non-negotiable notification deadlines. Your legal and compliance teams need to lead this charge, making sure every box is ticked to avoid painful fines.
- Internal Stakeholders: Your own people need the story straight from you. Keeping employees in the loop stops rumors and empowers them to handle customer questions with consistent, accurate information.
Having pre-approved templates is a lifesaver here. It saves precious time and prevents a bad situation from getting worse because of a poorly worded, off-the-cuff statement. For a deeper dive, check out our guide on building a solid communication plan template.
Secure System Recovery and Hardening
While the comms team is managing the public-facing side, your technical crew has its own mountain to climb. This isn't just about flipping a switch to get systems back online. It’s a deliberate, security-first recovery.
The process starts with restoring data and applications from clean, verified backups. It is absolutely essential to do this in an isolated sandbox environment first. You need to test everything for any lingering malware or backdoors before even thinking about going live. The last thing you want is to accidentally re-infect your own network.
While that's happening, the team must focus on total eradication. This means patching the vulnerability the attacker used, hunting down and removing any backdoors they left, and hardening security controls across the board to prevent a repeat performance.
The goal of recovery isn't just to get back to "business as usual." It's to emerge from the incident stronger and more resilient than you were before.
The Financial Imperative for a Solid Plan
The staggering costs of data breaches really drive home why this phase is so vital. Breaches are getting more common and more expensive, especially in critical industries.
For example, the healthcare sector saw the average cost of a breach hit $9.77 million in 2024, a whopping 53% increase since the pandemic began. Over in financial services, API and web app attacks jumped by 65%, pushing their average breach cost to $5.9 million. These aren't just numbers; they’re a clear signal that effective post-breach management is a financial necessity, not just a technical one. You can dig into more of these rising cybersecurity costs and explore additional industry statistics to see the full picture.
The Blameless Post-Mortem
When the dust finally settles, the most important step for your long-term health is the post-mortem. Get the entire incident response team and key stakeholders in a room to dissect what happened, from the initial alert to the final recovery.
This has to be a blameless forum. The goal isn't to point fingers; it's to find gaps in your process, technology, or training.
Document everything. What went well? What didn't? Update your playbooks with these lessons. Use the findings to build a business case for the resources you need, whether that's a new security tool or more training for the team. This is how you turn a painful crisis into a powerful learning opportunity.
Frequently Asked Questions
Even with the best guide in hand, some questions always seem to pop up when you're piecing together something as vital as a data breach response plan. Let's walk through some of the most common ones I hear from teams to clear up any lingering doubts and help you build a strategy you can count on.
How Often Should We Test Our Response Plan?
The quick and easy answer is at least annually. You have to think of it like a fire drill—you don't want to wait for an actual fire to discover the alarm is broken. A yearly tabletop exercise is the bare minimum to keep your plan from gathering dust on a shelf.
That said, if you're in a high-stakes industry like finance or healthcare, or if your IT environment has changed significantly, quarterly testing is a much safer bet. The real goal here isn't just to tick a compliance box. It's about building muscle memory, so when a real incident strikes, your team responds with process and instinct, not panic.
The most valuable part of testing is finding the flaws before an attacker does. Every gap you identify in a controlled drill is a crisis you avert in the real world. A successful test isn't one where everything goes perfectly; it's one where you learn what to fix.
What Is the Single Biggest Mistake in a Response?
It's not a technical failure; it's a human one. The most frequent and damaging mistake I see is a complete breakdown in clear, decisive communication. This happens on two fronts: internally among the response team and externally with customers and regulators.
When your messaging is slow, confusing, or contradictory, you're just pouring gasoline on the fire. It demolishes customer trust faster than the breach itself, sows chaos within your own teams, and can amplify the reputational harm tenfold. Having a pre-approved communications strategy, with templates locked and loaded, is your best shield against this kind of self-inflicted wound.
Does Our Small Business Really Need a Formal Plan?
Yes. Without a doubt. It’s a dangerous myth that attackers only target massive corporations. The truth is, small and medium-sized businesses (SMBs) are often seen as juicier targets precisely because they’re assumed to have weaker security and no formal plan to fight back.
For an SMB, a data breach can be an extinction-level event. The kind of financial hit and reputational damage a large enterprise can absorb could easily be enough to force you to close your doors for good. The scale of your plan might be smaller, but the core elements are the same:
- Preparation: Know who does what before the crisis hits.
- Containment: Stop the bleeding as fast as humanly possible.
- Recovery: Learn from the incident and rebuild a stronger defense.
Your data breach response plan is a fundamental survival tool, not some "nice-to-have" luxury for the big players.
Should We Involve Legal Counsel When Building the Plan?
Absolutely, and you should bring them in at the very beginning—not just after a breach happens. Getting legal counsel involved proactively is one of the smartest things you can do. They bring crucial expertise on a few key fronts.
First off, they live and breathe the tangled web of regulatory notification laws. Whether you're dealing with GDPR, CCPA, or other industry-specific rules, they know exactly who you need to notify and how fast you have to do it. Missing those deadlines can bring on some seriously painful fines.
Second, their early involvement can help wrap your internal investigation communications under attorney-client privilege. This is a huge deal. It can protect your internal analysis and candid discussions from being exposed in potential lawsuits down the road.
Finally, they’ll put every planned external statement under a microscope to minimize your legal liability. Their input ensures your response is not only technically solid but also legally sound. For example, if a breach involves compromised employee accounts, you'll need a process to lock access immediately. To handle this properly, you can learn how to deactivate Jira users as a structured part of your response.
Are you looking for a smarter way to manage your Atlassian user lifecycle and optimize license costs? The resolution Reichert Network Solutions User Deactivator app automates the tedious work of finding and deactivating inactive users in Jira, Confluence, and Bitbucket. Keep your user directory clean, secure, and cost-effective without the manual effort. Discover how you can save on licensing fees by checking out our User Deactivator overview.