
2022 will see the consolidation of “the world’s biggest work-from-home experiment”.
But the speed of experimentation often comes along with risks that are difficult to evaluate. At least, until we gather enough experience.
How many managers thought it was just fine to hold the company meeting every morning over Zoom until they found out about unexpected visitors bombing the service? How many felt too scared that their employees would not be productive working from home? And how many of us are just tired of not having the right resources to handle collaboration, now that schedules have become much more flexible and asynchronous?
While thousands of corporations have implemented work from home policies, many don’t have neither the policies nor the infrastructure in place to maintain acceptable levels of enterprise security without sacrificing remote employee efficiency.
So here’s a quick guide on how to get up to speed with the secure collaboration capabilities of technological behemoths like Atlassian, Google, or Cisco, not to mention smaller remote-native companies like Automattic (makers of WordPress), GitLab, or Zapier, to name just a few.
Understanding Security with Atlassian Products
Every Atlassian tool contains sensitive information: Confluence is a repository of internal knowledge, often including strategic plans and business KPIs; Jira manages new products and features waiting to be released; while Bitbucket holds the source code.
Corporations want to keep information protected from intruders, but also make it highly available for collaboration internally and with any strategic partners.
The following recommendations will help you strike that balance.
#1 Centralize user identities
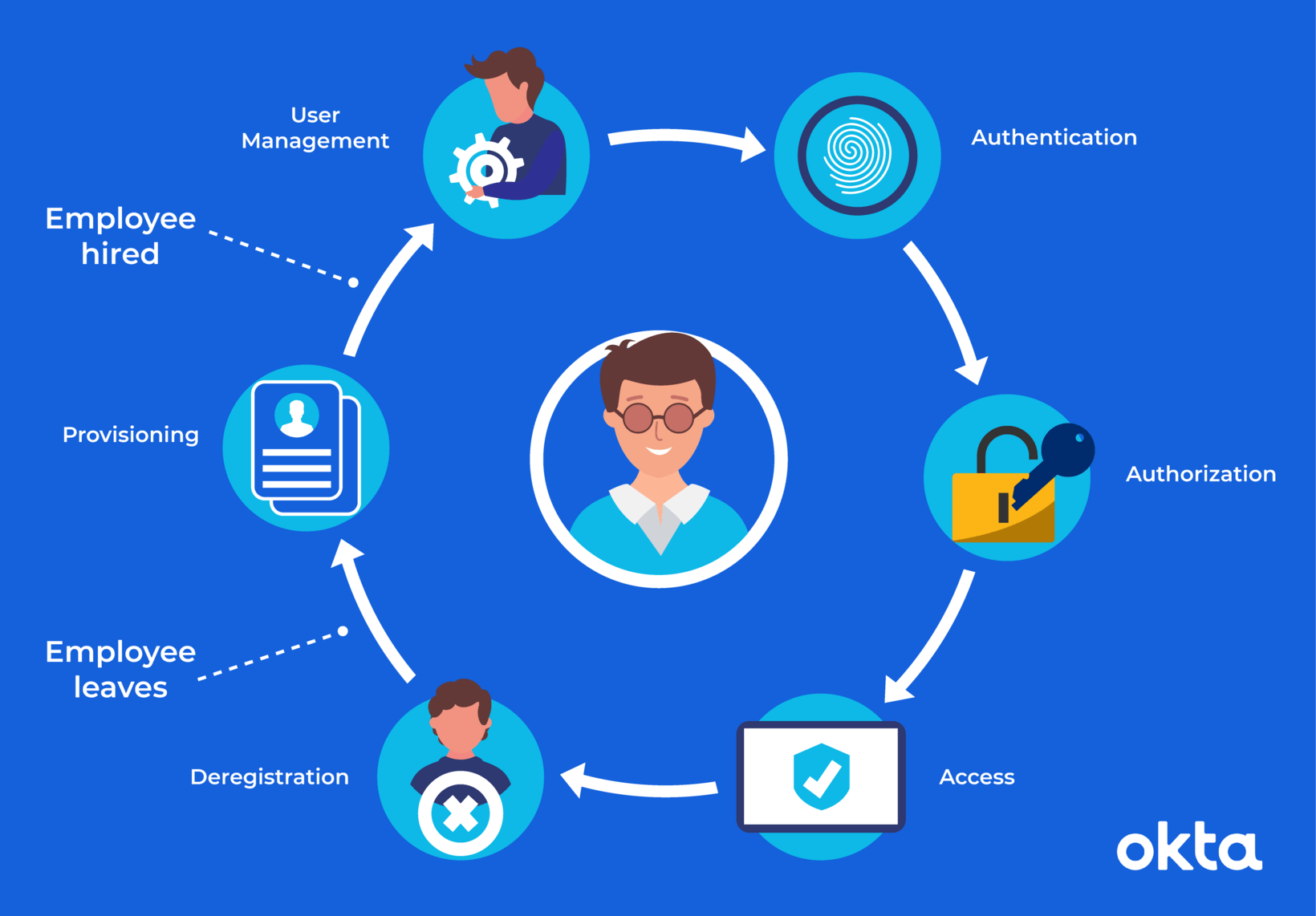
Employees nowadays manage accounts on dozens of cloud applications. Maintaining user profiles that are consistent and accurate is busy work nobody wants to do.
Reminders to have information updated manually by each user are not very productive. When you ask to upload a profile picture here and there, a telephone number in the HR application, a t-shirt size in Confluence… you will always have missing information and chase down both busy workers and lazy folks.
On the contrary, maintaining a central repository of information only will make life easier for administrators and employees at the same time. You won’t have to check for consistency. Comprehensive data will be simply a given.
#2 Integrate user data to enable automations
So now you have centralized user identities on your Identity Provider. Great!
The next thing you want to do is synchronize those user accounts with your corporate applications. You will never have a wrong telephone number in Salesforce again.
What happens when user data is integrated from a single source of truth? Endless automations become possible, and exceptions due to outdated or missing data disappear.
#3 Unleash spontaneous collaboration
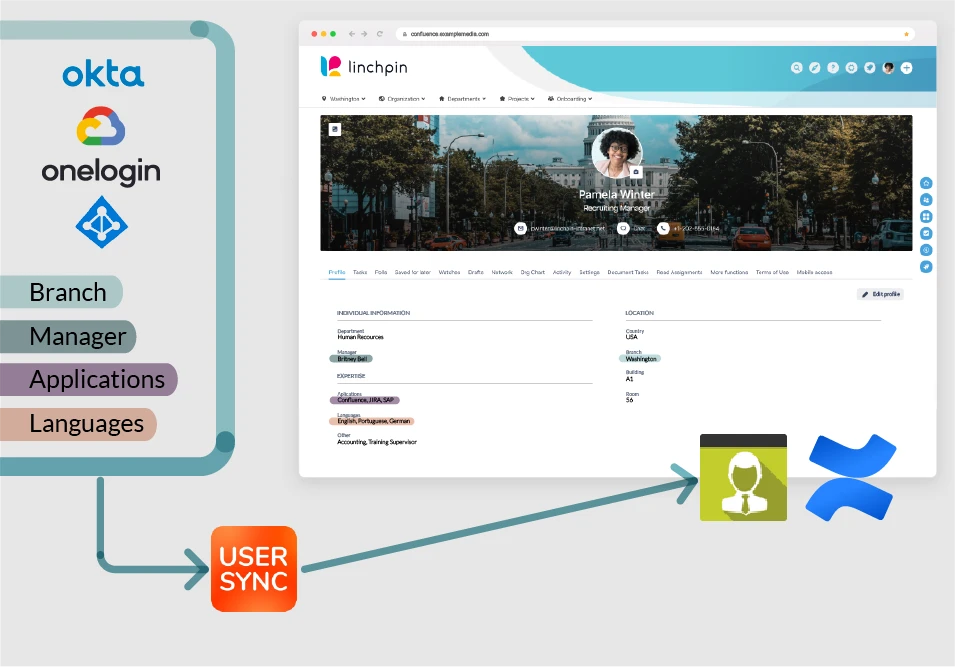
Integrating Azure AD with Confluence Data Center and Linchpin will give everyone the superpower to identify who’s in charge of which initiative, and who has the right skills for a new assignment.
Keep reading about the new User Sync integration with Linchpin
In big corporations in the old face to face times, it could take days to find the right person to talk to about a particular initiative. Or even weeks to negotiate adding a new project member and to find someone with the right skillset.
Remote collaboration can be much more efficient and spontaneous when you’ve centralized user identities and integrated user data across applications.
For example, imagine you’ve integrated your cloud user directory in Azure AD with Confluence Data Center. And on top of that, you’re using Linchpin, the social intranet, which includes rich User Profiles with the ability to add any number of fields.
Want to find out who’s in charge of a project? Just look it up in the dynamic organizational chart.
Want to find an expert? Simply go to the user browser and filter for the skill requirements, right within Confluence. Who knew you would find two guys with .NET and advanced Russian for your last project?
#4 Create (and Document) a Culture of Remote Security
While cybersecurity might bore most employees, it’s important to communicate effectively that every enterprise is only as secure as its weakest link. Intruders only need one bad password (or non-secure transmission of a great password) to get inside. And once they’re in, it’s almost impossible to stop them.
A library of authorized and secure resources is one good way to start building awareness and security best practices. Make sure to include easy to read tips, guidelines, and basic do’s and don’ts and to refer to the library on different messages and channels — we all know that the secret of a successful Confluence page is in the usage as much as it is in the content itself.
This tactic doesn’t have much overhead, and it helps fight shadow IT by sending a clear message that many workday decisions, like the choice of using a cloud application, could have serious security implications and are not to be taken lightly.
#5 Minimize The Number of Passwords
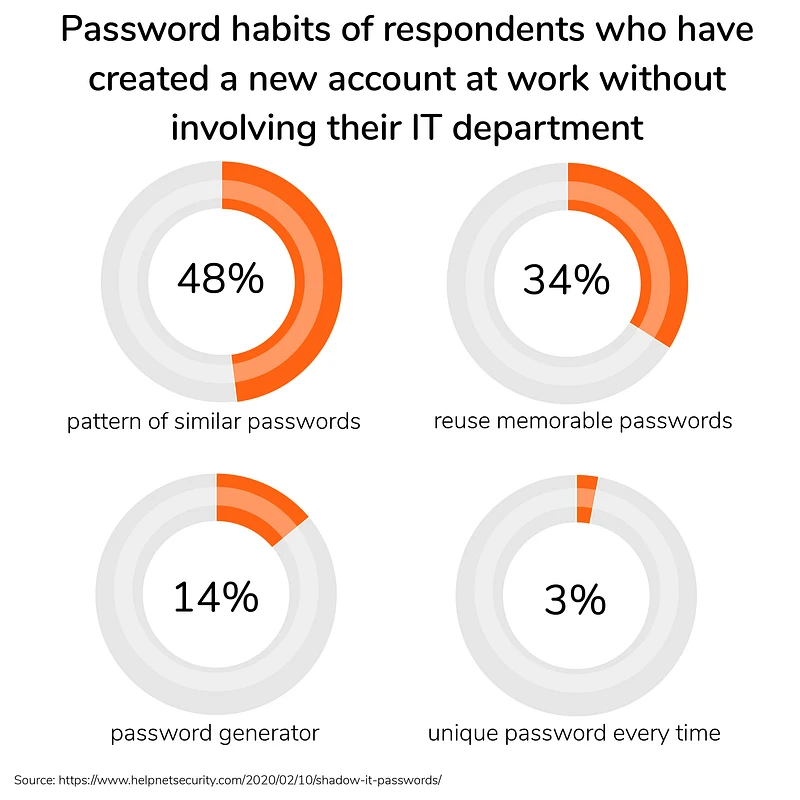
In addition to the tools typically used onsite, remote employees need to access more and more cloud products like Zoom, Slack, Microsoft Teams or Miro to replicate the type of collaboration and responsiveness that exists in office environments. The risks are proportional: the more decentralized accounts, the less secure enterprise assets will be – particularly since a high percentage of employees use one memorable, arguably weaker password to log in everywhere.
The good news is, bad password habits can be eradicated for every app that can be authenticated via single sign-on
The idea behind single sign-on is ironically simple: get rid of passwords; instead, use the same authentication for every tool and govern it from a central location. This authentication happens via an identity provider like G Suite or Microsoft Azure, enabling you to use a limitless amount of compatible apps without having to authenticate each individually. Sometimes the only login to which employees are prompted is in the OS start session of their corporate devices.
But what’s usually seen as a synonym of user experience has tremendous advantages in terms of security:
it’s easier to maintain or even remember one great password than to keep separate, secure passwords for potentially hundreds of applications.
Our Single Sign-On apps are available across the Atlassian product suite.
#6 Synchronize Logout
Would you like to have a master key that opens all your doors but can’t be used to lock them when you’re out? That’s a bit of the problem you have when you implement SSO solutions that don’t feature Single Log Out. When preventing account hijackers or actively fighting against them, Single Log Out (SLO) is not a nice to have; it’s the single most important resource for users who want to cover their track and for systems administrators that spots unusual activity and have serious reasons to believe that the information held by the enterprise identity provider may have been compromised.
See how simple it is to implement SLO in our SAML Single Sign-On apps.
Conclusion
Securing enterprise information these days can’t be an afterthought: it requires careful planning, proper resources, and extensive training. There’s no magic trick to protect your company.
But once you have the right security foundation, there are no excuses for hypergrowth in the speed of digital collaboration. Tools and applications are ubiquitous. You just need to replace physical presence in the same place with the ability to discover who’s the best partner in crime for each new business project.
The recommendations in this article should serve as a solid blueprint for exploiting the great advantages of remote collaboration with Atlassian tools.
