
The Hansgrohe Group is an internationally active manufacturer of premium and designer showers, faucets and accessories for the bathroom and the kitchen. The Black-Forest based company has left their mark on the history of bathroom design, as well as on innovations in and around both the bathroom and the kitchen.
With a history going back 120 years, Hansgrohe’s vision focuses on innovations with water. Atlassian tools important to how that vision unfolds into actual collaboration practices within the company and with external partners.
The vision for Digitization at Hansgrohe
| Founded | 1901 in Schiltach (Germany) by Hans Grohe |
| Total employees | Ca. 4,700 (2020) |
| Atlassian Applications | Jira (2,000 users), Confluence (4,000 users) |
| Teams involved | All office employees |
| External Users | 10% of overall users are external. |
| The challenge | With Data Center’s SAML SSO, login was failing for some cloud users coming from external Azure AD (Entra) configurations where UPN ≠ email address. |
| The killer feature | Flexible attribute mapping |
| Benefits of resolution SAML SSO | – Users can be looked up in Azure AD (Entra) by their email address (instead of the UPN) – All external users can login successfully – Smooth collaboration with critical partners |
Hansgrohe has a very ambitious vision to deliver digital experiences to their customers, and Atlassian tools have a significant role in that delivery.
Confluence at Hansgrohe: A collaborative mission
Digital products like hansgrohe RainTunes have hundreds of components: software, connectivity, sanitation hardware and functionality… The final product would be impossible if teams worked in silos with traditional project management practices and without very tight collaboration. Intense collaboration implies a constant use of the Atlassian stack.
Collaboration at Hansgrohe is tied to two big names: Atlassian, and Microsoft. When management looked for a suite to lead the company’s new digitization strategy, it appointed both companies as strategic collaboration vendors.
The Hansgrohe journey with Atlassian had started similarly to many other companies: quite small. Back in 2015, an IT Operations team started using Jira and Confluence to support its processes. In a short time, more and more teams were using the tool.
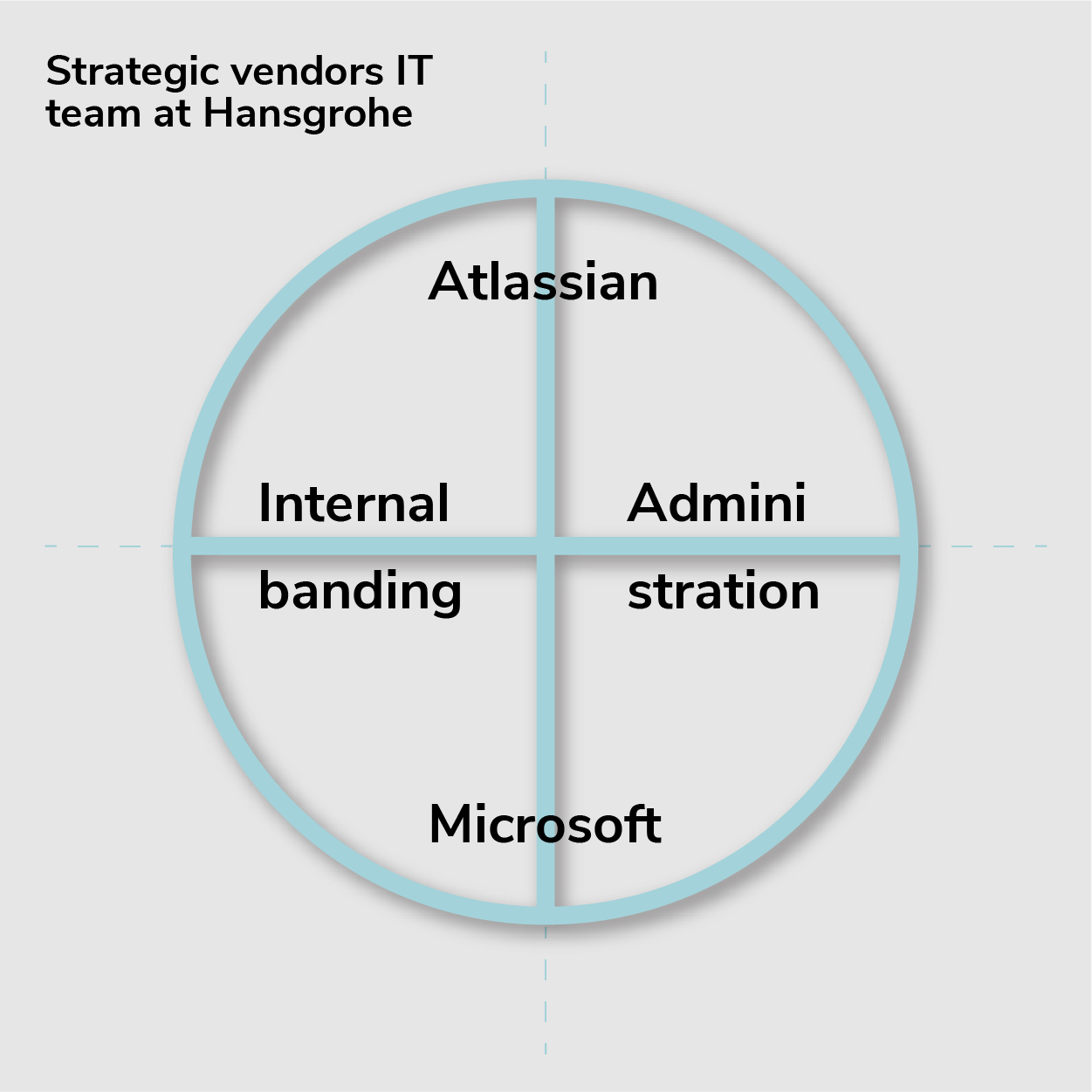
Currently, half of the Atlassian team is devoted to internal branding, that is: evangelizing Atlassian applications and promoting user adoption. The other half is devoted to administration. The entire team has leaned on Trivadis both for specific technical challenges and to find the most fitting setup for the company’s use cases.
Confluence as a knowledge management hub
We’re also in the process of breaking down the traditional department structures, creating the conditions that will allow our digital experts to pass on their knowledge across multiple disciplines with ease.
Hansgrohe, 2020 Annual Report
All office workers at Hansgrohe have access to Confluence, the mandated platform for knowledge sharing, documenting meetings, and project collaboration. With employees actively trained to become digital transformers, the central role of the Atlassian wiki is becoming increasingly critical.
Why external users are vital in Confluence
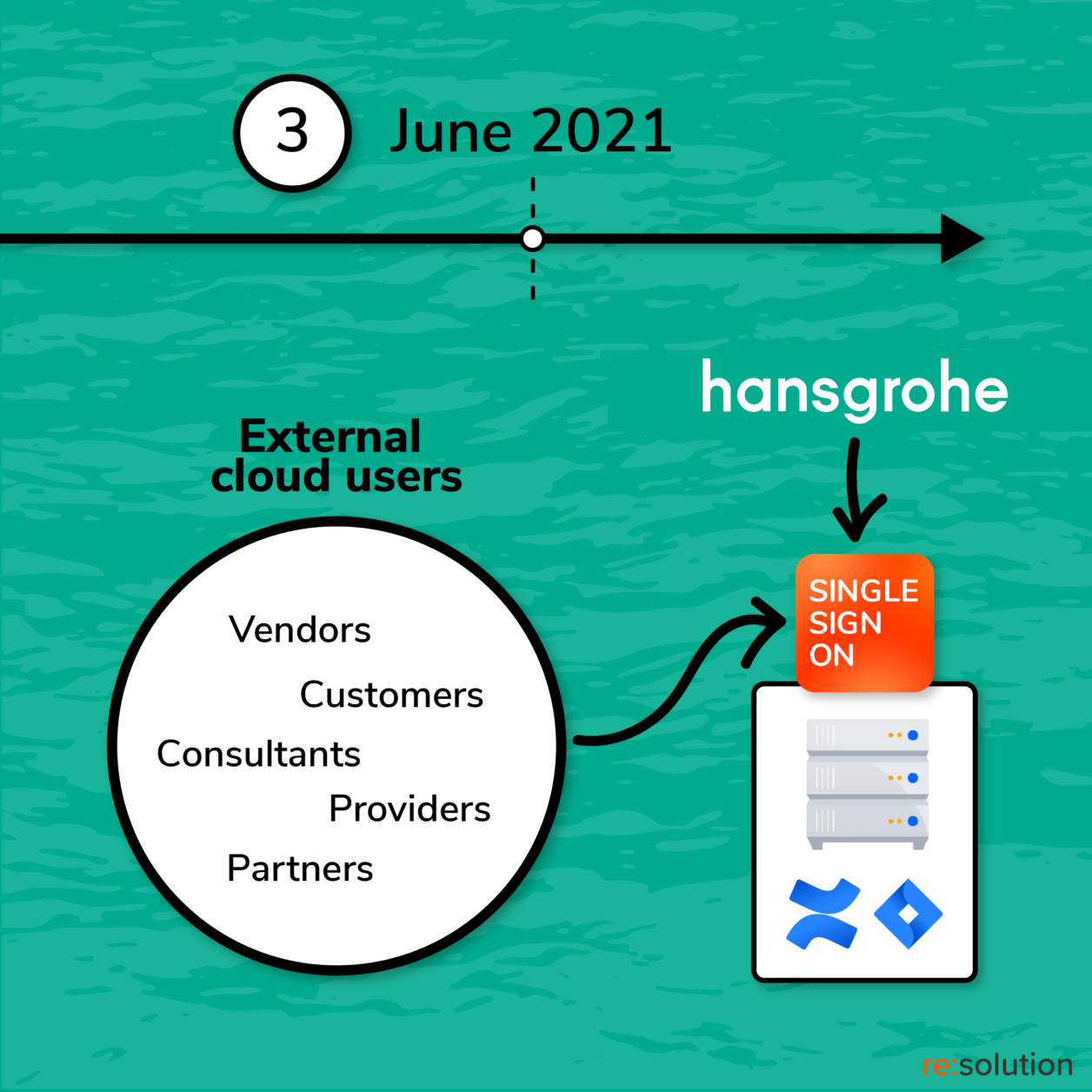
Hundreds of external users also need access to Confluence, including vendors, partners, consultants, and providers. In total, a 10% of the Atlassian accounts correspond to external users of all types, which are called “Collaboration Cloud Users”. Those Cloud Users build the basis for a full collaboration in other systems as well, e.g. Microsoft Teams.
In the hansgrohe RainTunes product, for example, many different accounts were provisioned for the strategic design partner with expertise in Product and Interaction Design that the company just wouldn’t have been able to mobilize in-house.
The first implementation of resolution SAML SSO
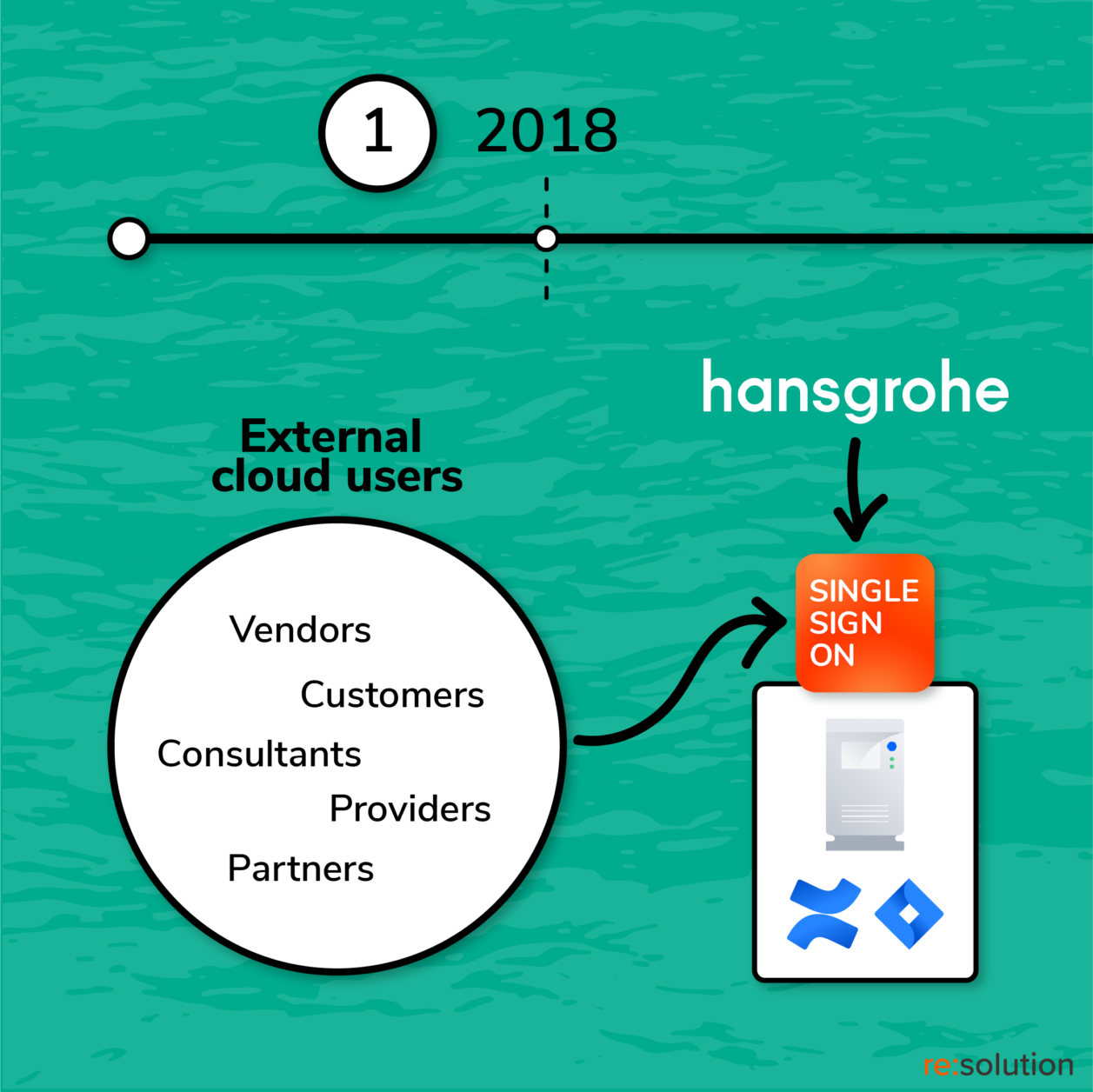
Speedy and frictionless access into Atlassian tools is vital for Hansgrohe’s digital ambitions. Single Sign On is a basic requirement to bring both employees and external users into Jira and Confluence. But it wasn’t supported natively.
Microsoft Azure AD (Entra) Connector for Confluence
A third-party connector was needed. Back in 2018, the first attempt was to implement SAML Single Sign-On with Microsoft’s free Azure AD (Entra) connector for Jira and Confluence. But the deployment failed, with the plugin having little documentation and functionality besides the basic authentication of existing users.
Looking for the best SAML SSO plugin for Confluence
The Atlassian team at Hansgrohe then decided to implement resolution’s SAML SSO, a commercial plugin that was fully maintained and supported. The experience was entirely different:
What we found during our evaluation of the resolution SAML SSO plugin was a very high technical feasibility in the glimpse of an eye
Benjamin Wolber, Product Owner at Hansgrohe Group
Throughout the entire implementation, Wolber only raised one ticket with the resolution support team after having encountered issues authenticating with the Confluence mobile app – and it resulted in a ticket for Atlassian support.
Reasons for migrating Confluence and Jira to Data Center
Server End of Life
After Atlassian’s CEO Scott Farquhar announced the End of Life for Server instances in October 2020, IT leadership at Hansgrohe analyzed the alternative migrations to Cloud and Data Center from three sides: functionality, infrastructure/security requirements, and pricing and licensing.
The final decision was to migrate to Data Center.
Besides the push received from Atlassian, Data Center offered three functional advantages that would contribute to having less apps in the basket: Native SSO, Advanced Roadmaps, and Clustering.
Native SSO
The most obvious replacement was resolution’s SAML SSO plugin for Confluence and Jira with the native SSO functionality included in all Data Center applications.
Unfortunately, the implementation of the Data Center native single sign-on was rolled back because of critical limitations in how external users are handled.
The challenge: provisioning external Confluence users
The Data Center native SSO offers the basic functionality and may be working fine for companies that are not that complex. But it didn’t work for us: we needed more options for mapping user attributes
Benjamin Wolber, Product Owner at Hansgrohe Group
Wolber and the rest of the Atlassian team at Hansgrohe experienced first-hand the limitations of Atlassian’s Single Sign-On. The solution works for simple use cases. It lacks, however, in configuration options, and is prone to failure whenever the customer’s identity infrastructure has specific or unusual requirements.
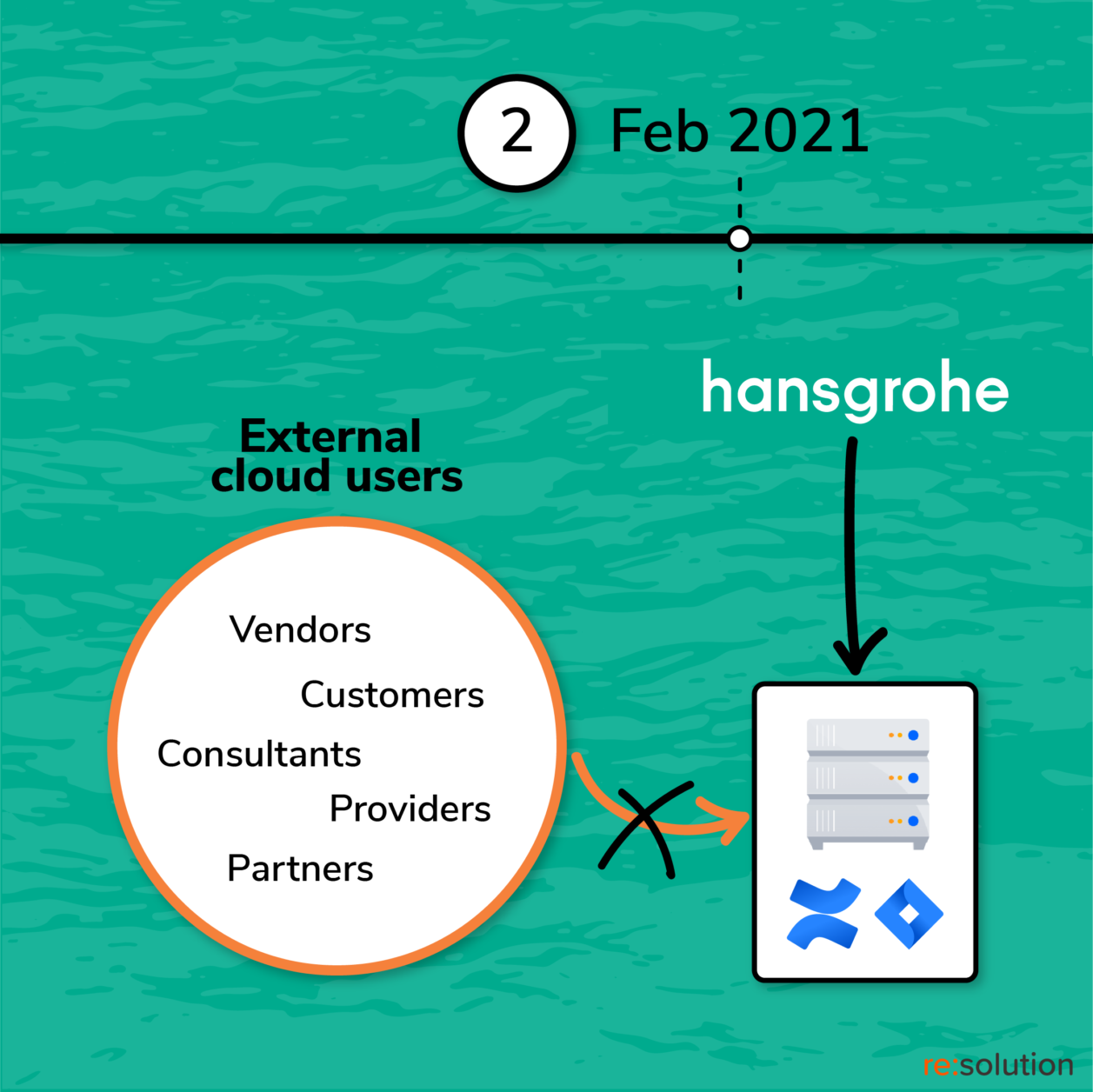
For Hansgrohe, Data Center SSO’s inability to use the email attribute in order to lookup users resulted in the failure to authenticate many external users.
Partners can’t log in with cryptic UPNs
Data Center SSO can only reflect one attribute for user mapping.
As great and powerful as it may be, Microsoft Azure AD, now called Entra, has very special characteristics that need to be dealt with. Among other things, user accounts are identified with a field called UserPrincipalName (UPN).
Microsoft recommends populating its UPN field with the user’s email address.
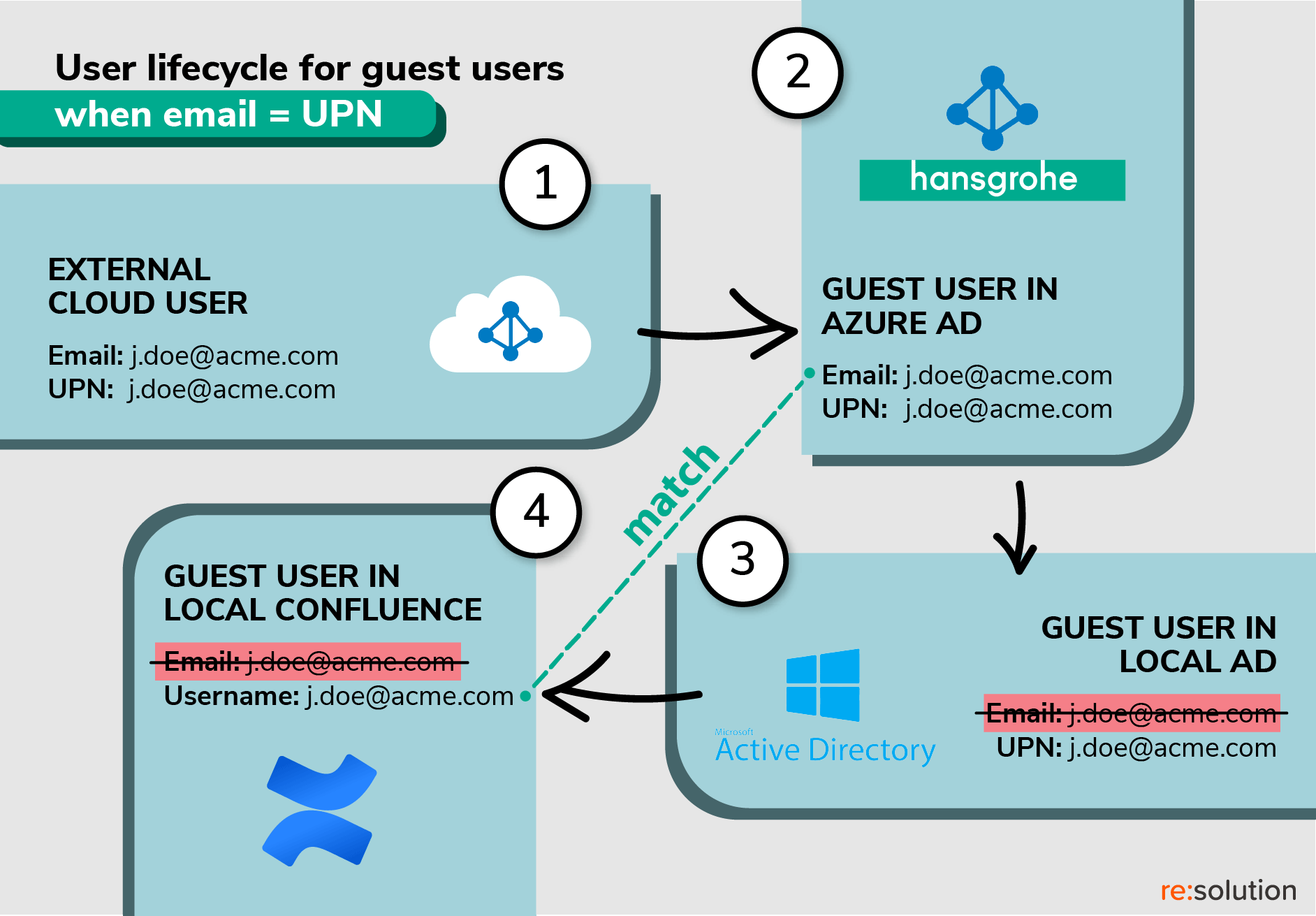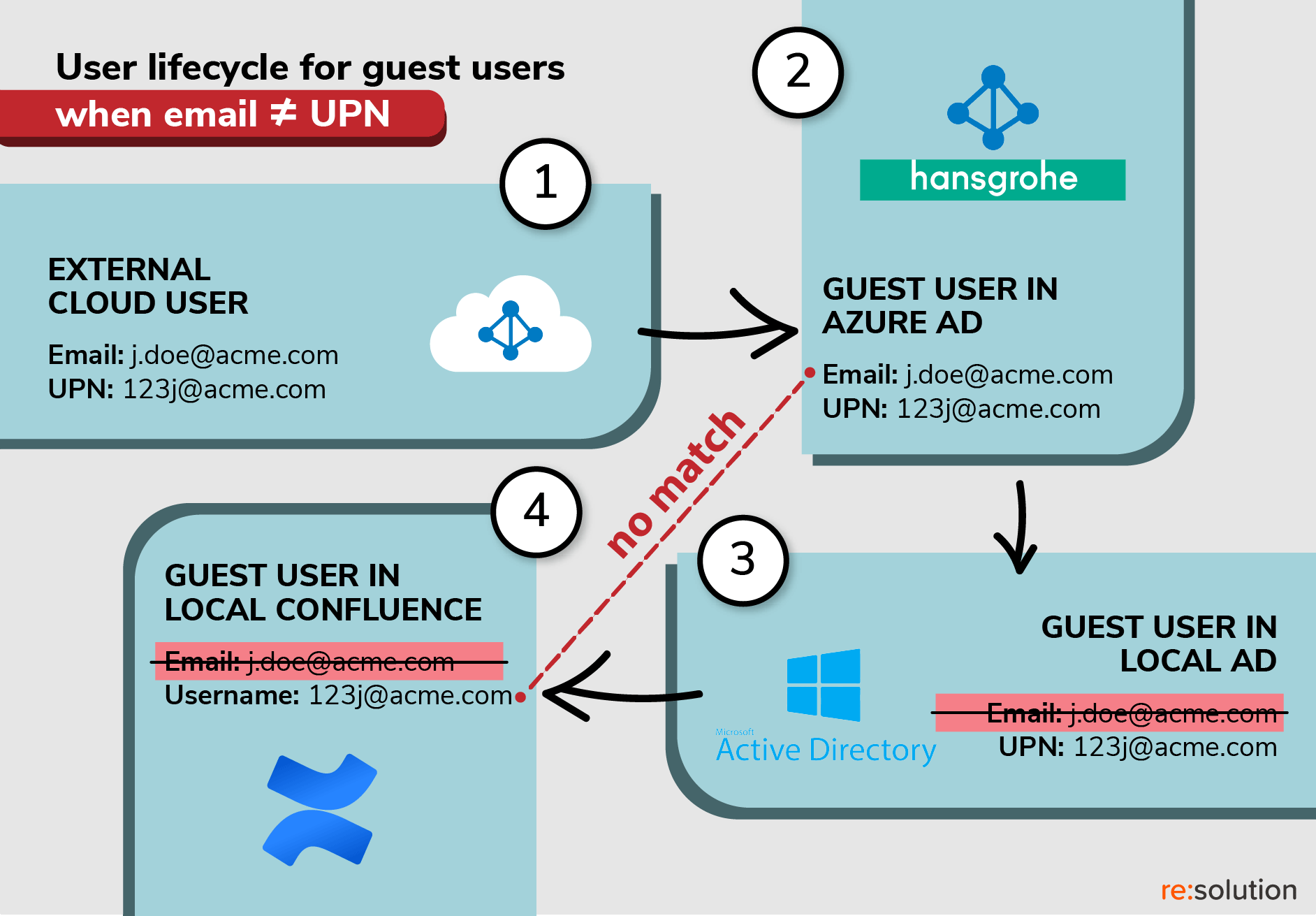
Not all Hansgrohe partners follow this practice when they configure their Active Directories. Instead, some of them prefer to use different values for the UPN and for the email address.
As a result, a user named John Doe could have an email address johndoe@acme.com and a UPN 123j@acme.com.
This is what happens when John is invited to Hansgrohe’s Confluence:
- First, John has to accept the invitation so that his profile can be transmitted.
- Second, the UPN becomes John’s standard username in Hansgrohe’s Azure AD (Entra).
- Third, John’s account is sent to Hansgrohe’s local Active Directory. However, only the UPN is passed. The email value stays behind.
- Fourth, John’s account is created in Confluence locally using the UPN as the Atlassian username.
How Data Center SSO fails to handle external users
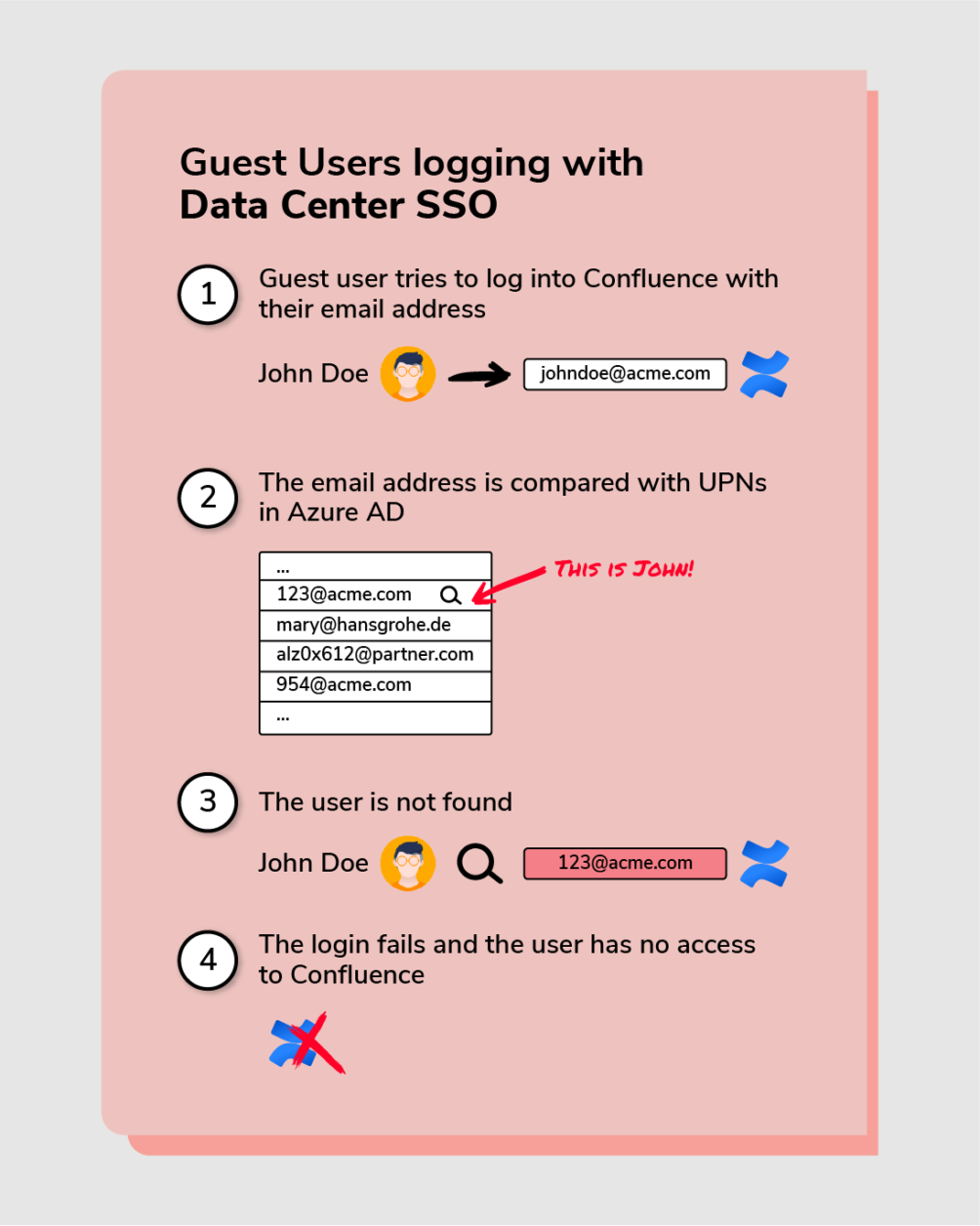
However, when John tries to access Confluence, he will go through this process:
- He will type his UPN in the login form
- The Atlassian Data Center SSO will try to find John in Azure AD (Entra). He will forward the Authentication request to the AzureAD of the Partners Company.
- The authentication in the AzureAD works fine, as both UPN and mail-address are known
- However, when the authentication token is passed back to Confluence, the external user can only be matched by its email – which is not known.
- Therefore, the SSO flow will not be able to match John’s UPN with John’s email
The solution: adjustment of the user mapping attribute within Confluence
Back to resolution’s SAML SSO plugin for Confluence and Jira
As soon as Hansgrohe reactivated resolution’s SAML SSO plugin for Jira and Confluence with a new Data Center license, external users were able to log in again. How could that happen?
How resolution’s SAML SSO succeeds in handling external users
It’s actually quite simple. Resolution’s SAML SSO allowed Hansgrohe to change the authentication attribute from Username to Email. This setup applies for all both internal and external accounts.
This is what their attribute mapping looks like.
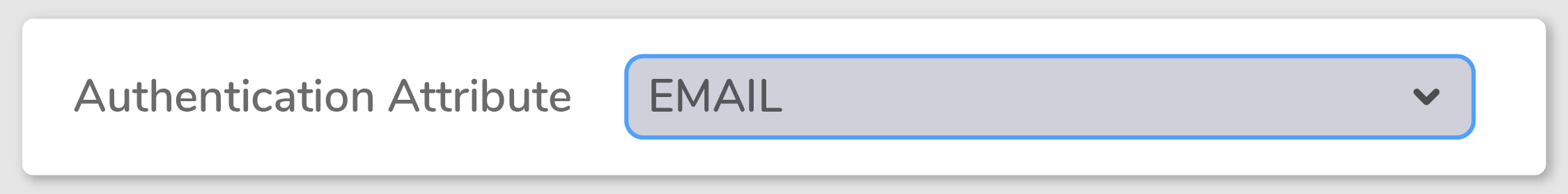
This small change allows to map users across directories efficiently, as emails are only compared with emails and UPNs can be ignored.
The issue had already been solved in the initial setup from 2018. Handling two attributes to authenticate external users is not that extraordinary
Conclusion
Single Sign On is a mission-critical requirement for Hansgrohe: secure and timely access to the Atlassian stack for every user is not optional.
Resolution’s suite of SAML SSO apps ensure full control over the configuration details to deploy accurate and sophisticated implementations. Flexible attribute mapping is one of the most differential factors, ensuring that user data is perfectly integrated from the Identity Provider into the Atlassian applications.
About Hansgrohe
Hansgrohe SE is a German sanitary fittings manufacturer founded by Hans Grohe in 1901, in Schiltach, Germany. As one of the world’s largest suppliers of shower heads and faucets it focuses on innovation, design, quality and responsible manufacturing.
About Trivadis
Founded in 1994, Trivadis is a leading technology service provider and an Atlassian Platinum Solution Partner since 2007. Trivadis covers the entire spectrum, from the development and operation of data platforms and solutions, the refinement of data, to consulting and training. In 2021 it became part of the Accenture group.




