In today’s complex business landscape, simply having a risk management plan isn’t enough. The key to building resilience and seizing opportunities lies in choosing and implementing a framework that aligns with your specific goals, industry, and organizational culture. But with so many options, from the universal principles of ISO 31000 to the cyber-focused precision of NIST, how do you know which is right for you?
This guide moves beyond surface-level descriptions to provide a deep strategic analysis of seven powerful risk management framework examples. We will dissect their core components, uncover their unique strategic applications, and deliver actionable takeaways you can implement immediately. Whether you’re a Project Manager, IT professional, or Operations lead, you’ll find practical insights here.
Prepare to transform your approach from a reactive, compliance-driven task into a proactive, strategic advantage. Instead of just listing theories, we will break down how these frameworks function in the real world. You will learn how to select and adapt a structure that not only protects your operations but also helps you achieve compliance and drive significant business value. Let’s explore the frameworks that will fortify your organization.
1. ISO 31000 Risk Management Framework
The ISO 31000 standard, developed by the International Organization for Standardization, is one of the most universally recognized risk management framework examples. It’s not a certifiable standard but rather a set of principles and guidelines designed to be adaptable to any organization, regardless of size, sector, or context. Its core philosophy is to integrate risk management seamlessly into an organization’s governance, strategy, and daily operations.
ISO 31000 promotes a systematic and structured approach, emphasizing that risk management should create and protect value. It moves beyond simply avoiding negative outcomes and focuses on optimizing opportunities. The framework is built on a foundation of leadership commitment and a deep understanding of the organization’s internal and external context.
Strategic Analysis & Application
ISO 31000’s strength lies in its flexibility. Unlike rigid, prescriptive models, it provides a high-level architecture that organizations can customize. For instance, a multinational corporation like Shell uses its principles to manage complex geopolitical and environmental risks, while a healthcare provider applies it to enhance patient safety protocols.
The framework’s process involves three key phases: risk identification, risk analysis, and risk evaluation. This cycle is supported by continuous communication, consultation, monitoring, and review, ensuring that risk management is a dynamic, living part of the organization.
The following summary box highlights the essential components of the ISO 31000 framework.

This visual breakdown underscores that the framework’s power comes from its guiding principles and its iterative, three-phase risk management process.
Actionable Takeaways
To effectively implement ISO 31000, organizations should focus on several tactical steps:
- Secure Leadership Buy-In: Management must champion the initiative, allocating resources and communicating its strategic importance.
- Customize, Don’t Copy: Tailor the guidelines to your specific operational realities, industry regulations, and organizational culture. A one-size-fits-all approach will fail.
- Integrate and Automate: Weave risk management activities into existing processes like strategic planning, project management, and operational workflows. This is a critical step in change management, and a robust change management process template from Resolution can provide a structured approach.
- Define Roles Clearly: Establish a clear risk governance structure, assigning ownership for specific risks and management tasks to ensure accountability.
2. NIST Cybersecurity Framework
Developed by the U.S. National Institute of Standards and Technology (NIST), the Cybersecurity Framework (CSF) provides a high-level, strategic view of an organization’s management of cybersecurity risk. It is one of the most respected risk management framework examples in the digital space, offering a common language and systematic methodology. The CSF is designed to be voluntary and flexible, helping organizations of all sizes and sectors improve their ability to prevent, detect, and respond to cyberattacks.
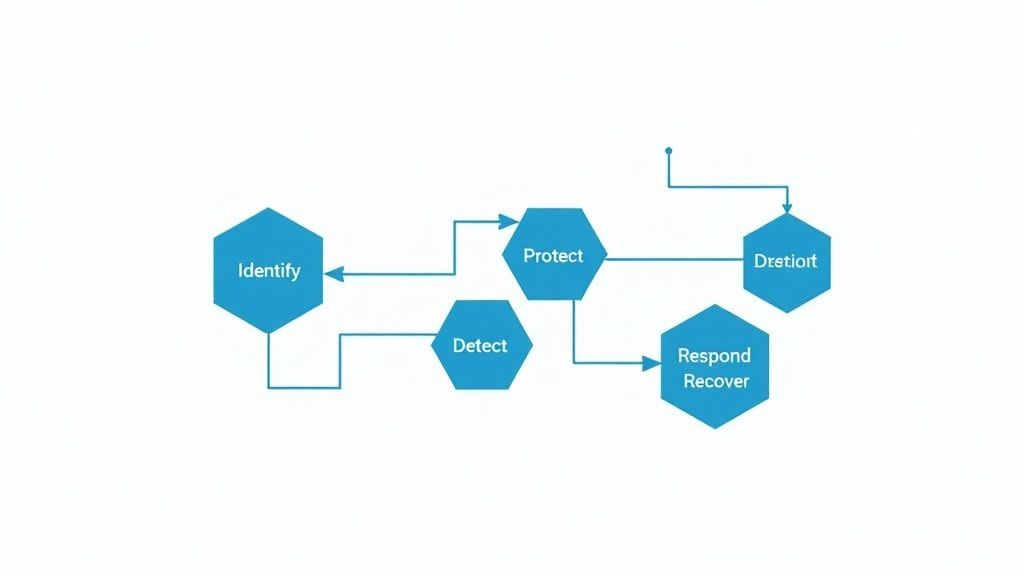
The framework is structured around five core functions: Identify, Protect, Detect, Respond, and Recover. These functions provide a complete lifecycle for managing cybersecurity risk, from understanding your digital assets and vulnerabilities to restoring capabilities after an incident. This comprehensive approach allows organizations to build resilience and improve their security posture over time.
Strategic Analysis & Application
The NIST CSF’s power lies in its structured yet adaptable nature. It enables organizations to assess their current cybersecurity capabilities against a recognized benchmark, define a target state for their security posture, and create a prioritized action plan to close the gaps. For example, financial institutions like JPMorgan Chase use the CSF to strengthen defenses against sophisticated financial threats, while healthcare organizations apply it to protect sensitive patient data in compliance with regulations like HIPAA.
The “Respond” function is a critical component, focusing on the actions taken immediately after a cybersecurity incident is detected. Having well-defined processes here is essential for minimizing damage. For a structured approach to this phase, organizations can leverage robust incident management procedures from Resolution to ensure a coordinated and effective reaction. This systematic approach allows organizations to move from a reactive to a proactive security stance.
Actionable Takeaways
To effectively implement the NIST Cybersecurity Framework, organizations should focus on several tactical steps:
- Create Current and Target Profiles: Start by assessing your current security activities against the CSF’s five functions to create a “Current Profile.” Then, define your desired risk management goals to build a “Target Profile.”
- Prioritize and Bridge Gaps: Analyze the differences between your current and target profiles to identify gaps. Prioritize these gaps based on your risk tolerance, business needs, and available resources to create a clear implementation roadmap.
- Leverage Existing Controls: The CSF is not meant to replace your current security systems. Instead, map your existing controls and investments to the framework’s functions to identify strengths and uncover areas needing improvement.
- Establish Key Metrics: Define and track metrics to measure the effectiveness of your implementation and demonstrate progress. This could include metrics like mean time to detect (MTTD) or mean time to respond (MTTR).
3. COSO Enterprise Risk Management Framework
The COSO ERM Framework, developed by the Committee of Sponsoring Organizations of the Treadway Commission, is a widely adopted risk management framework example specifically designed to help organizations integrate risk management with strategy and performance. Its core purpose is to assist management in making better decisions by understanding how risk can affect the pursuit of strategic objectives.
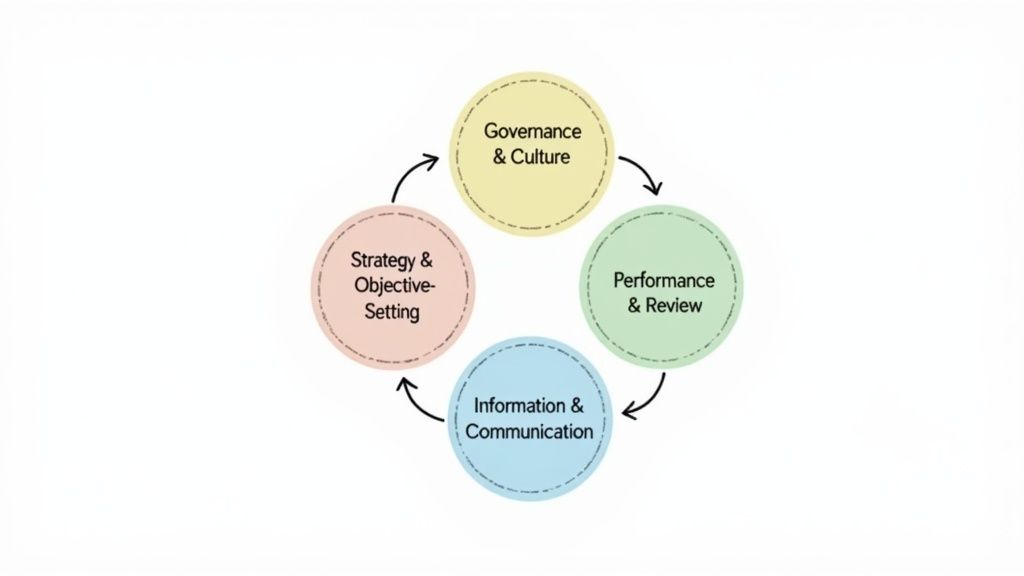
Unlike frameworks that treat risk in isolation, COSO ERM embeds risk considerations directly into the strategic planning process. It is built around five interrelated components: Governance & Culture; Strategy & Objective-Setting; Performance; Review & Revision; and Information, Communication, & Reporting. This structure provides a comprehensive lens for viewing and managing risks across the entire enterprise, from high-level strategic threats to granular operational issues.
Strategic Analysis & Application
COSO’s strength is its emphasis on connecting risk with value creation and preservation. The framework is not just about avoiding losses; it’s about making risk-aware decisions that drive performance and achieve strategic goals. For example, Fortune 500 companies like The Coca-Cola Company leverage COSO principles to manage a vast array of risks, including brand reputation, supply chain disruptions, and shifting consumer preferences, aligning risk management with long-term growth strategies.
The framework’s structure encourages organizations to define their risk appetite and tolerance in the context of their strategic objectives. This ensures that risk-taking is intentional and aligned with the board’s expectations. For a deep dive into applying these principles, particularly in daily operations, you can explore best practices for managing operational risk with Resolution. This alignment is critical for organizations in highly regulated industries, such as banking and insurance, where managing risk is fundamental to survival and success.
Actionable Takeaways
To implement the COSO ERM framework effectively, organizations should prioritize the following actions:
- Secure Executive Sponsorship: Gaining strong support from the board and executive leadership is non-negotiable. Their commitment ensures the initiative receives adequate resources and is seen as a strategic priority.
- Align Risk Appetite with Strategy: Clearly define and articulate the organization’s risk appetite. This critical step ensures that strategic objectives are set with a realistic understanding of the level of risk the organization is willing to accept.
- Implement in Phases: Avoid a “big bang” implementation. Roll out the framework in manageable phases, starting with a pilot in a specific business unit or focusing on a critical risk area to build momentum and learn lessons.
- Invest in Training: Provide comprehensive training and communication to embed a risk-aware culture. All employees must understand their role in managing risk and how it connects to the organization’s overall strategy.
4. FAIR (Factor Analysis of Information Risk) Framework
The FAIR framework, which stands for Factor Analysis of Information Risk, provides a specialized and quantitative model for understanding, measuring, and analyzing information risk. Unlike qualitative frameworks that categorize risk as high, medium, or low, FAIR is a powerful quantitative risk management framework example that helps organizations express risk in financial terms. It provides a taxonomy and methodology for decomposing risk into measurable factors.
This approach allows leaders to answer critical questions like, “How much risk do we have?” and “Which security investment provides the greatest return?” By translating abstract cyber threats into probable financial loss exposure, FAIR empowers organizations to make data-driven, business-aligned decisions. It shifts the conversation from technical jargon to the language of business value and monetary impact.
Strategic Analysis & Application
FAIR’s primary strength is its rigorous, analytical model that quantifies risk. It breaks down risk into two main components: Loss Event Frequency (how often a loss is likely to happen) and Loss Magnitude (how much financial impact a loss would cause). These are further broken down into smaller, measurable factors, creating a clear and defensible analysis.
Financial services firms use FAIR to quantify their exposure to cyber threats and justify security budgets to regulators. Technology companies apply it to estimate the potential costs of data breaches, while insurance carriers use it to develop and price cyber insurance products. The framework provides a common language for CISOs, CFOs, and board members to discuss and manage information risk strategically.
Actionable Takeaways
To leverage the FAIR framework effectively, organizations should adopt a structured and data-centric approach:
- Start with Key Scenarios: Begin by applying FAIR to a few high-priority risk scenarios, such as a major data breach or a critical system outage. This builds expertise and demonstrates value quickly.
- Invest in Data Quality: The accuracy of a FAIR analysis depends on the quality of the input data. Invest in processes to collect reliable data on threat event frequency, vulnerability levels, and potential loss impacts.
- Train Your Teams: FAIR requires a shift in mindset from qualitative to quantitative analysis. Provide comprehensive training on the methodology to security, risk, and business teams to ensure consistent application.
- Use Automation Tools: Performing complex FAIR calculations manually can be time-consuming. Utilize specialized software, like that promoted by the FAIR Institute, to automate the analysis and scale your program.
5. OCTAVE (Operationally Critical Threat, Asset, and Vulnerability Evaluation)
Developed by the Software Engineering Institute at Carnegie Mellon University, the OCTAVE framework is a risk-based strategic assessment method. As one of the more focused risk management framework examples, it empowers organizations to conduct self-directed evaluations. Instead of prioritizing technology, OCTAVE centers on organizational risk, business needs, and the protection of critical assets.
The core philosophy of OCTAVE is that the people who best understand an organization’s mission, assets, and operational risks are its own internal staff. The framework guides a small, interdisciplinary team of internal personnel through a process of identifying critical assets, the threats to those assets, and the vulnerabilities that expose them. This internal focus ensures the risk assessment is grounded in actual business context.
Strategic Analysis & Application
OCTAVE’s strength lies in its asset-centric and practice-based approach. It is particularly effective for organizations that need to understand security risks in the context of their specific business objectives. For instance, a financial institution can use OCTAVE to identify which information assets are most critical to customer trust and regulatory compliance, and then map threats directly to those assets. Similarly, a manufacturing company can apply it to secure proprietary designs and supply chain data.
The framework is typically implemented in three phases: building asset-based threat profiles, identifying infrastructure vulnerabilities, and developing a security strategy and plans. This structured process ensures that security efforts are not just technical exercises but are directly aligned with protecting what matters most to the organization’s success.
This overview explains how the OCTAVE method connects business drivers directly to security risk mitigation activities.
Actionable Takeaways
To effectively implement the OCTAVE framework, organizations should concentrate on several key actions:
- Assemble a Multidisciplinary Team: Create an internal assessment team with members from business units, IT, and management. This cross-functional perspective is crucial for identifying critical assets and realistic threats.
- Focus on Critical Assets First: The process begins by identifying assets most vital to the organization’s mission. This ensures that security resources are directed where they will have the greatest impact.
- Engage Senior Leadership: Secure buy-in and active participation from senior leaders. Their involvement is essential for validating asset criticality and championing the resulting security initiatives.
- Document and Iterate: Meticulously document all processes, findings, and risk mitigation plans. This documentation creates a repeatable process and a valuable knowledge base for future assessments.
6. Basel III Risk Management Framework
The Basel III framework is a globally recognized set of reform measures developed by the Basel Committee on Banking Supervision (BCBS) to strengthen the regulation, supervision, and risk management of banks. It was established in response to the deficiencies in financial regulation revealed by the 2007-2008 financial crisis. Its primary goal is to improve the banking sector’s ability to absorb shocks arising from financial and economic stress, thus reducing the risk of spillover from the financial sector to the real economy.
Basel III builds upon its predecessors (Basel I and II) by introducing more stringent capital requirements, new liquidity standards, and a leverage ratio. The framework mandates that banks hold more and higher-quality capital, ensuring they can withstand periods of stress without taxpayer support. It represents a critical example of a sector-specific, highly prescriptive risk management framework.
Strategic Analysis & Application
The strength of Basel III lies in its detailed, mandatory nature, which creates a level playing field for internationally active banks. Major institutions like JPMorgan Chase and Deutsche Bank have overhauled their capital and liquidity management systems to comply. The framework forces a rigorous, data-driven approach to identifying, measuring, and mitigating credit, market, and operational risks.
Unlike flexible guidelines, Basel III’s application is non-negotiable for regulated financial institutions. Its implementation requires significant investment in risk infrastructure, data analytics, and reporting capabilities. For example, the introduction of the Liquidity Coverage Ratio (LCR) and Net Stable Funding Ratio (NSFR) compelled banks to fundamentally restructure their balance sheets to maintain adequate high-quality liquid assets and stable funding sources.
Actionable Takeaways
To effectively navigate the complexities of Basel III, financial institutions must adopt a strategic and proactive stance:
- Establish Strong Governance: Create a robust governance and oversight process with clear accountability for capital and liquidity management. This ensures compliance is embedded at the board level.
- Invest in Systems and Data: Upgrade risk management systems and data infrastructure to support complex calculations, stress testing, and regulatory reporting requirements.
- Integrate Capital Planning: Embed Basel III requirements directly into strategic capital planning and forecasting processes to manage capital adequacy proactively.
- Maintain Service Continuity: Ensure that critical banking operations and IT systems are resilient. A focus on IT service continuity management is vital to meet operational risk requirements and maintain customer trust during any disruption.
- Engage with Regulators: Foster an open and continuous dialogue with national regulators to clarify expectations and navigate the phased implementation of the framework.
7. COBIT Risk Management Framework
COBIT (Control Objectives for Information and Related Technologies), developed by ISACA, is a leading framework for the governance and management of enterprise IT. It stands out as one of the most comprehensive risk management framework examples by specifically bridging the gap between technical IT issues and overarching business objectives. Its primary purpose is to help organizations generate maximum value from their IT investments by maintaining a balance between realizing benefits, optimizing risk, and using resources effectively.
The framework provides a set of principles, practices, and analytical tools designed to align IT strategy with business goals. COBIT’s risk management component is not an isolated function; it is deeply embedded within its governance model, ensuring that IT-related risks are identified, analyzed, and managed in the context of enterprise-wide risk appetite and tolerance. This holistic approach helps organizations meet regulatory requirements and improve accountability over their information systems.
Strategic Analysis & Application
COBIT’s strength is its structured, process-oriented approach to IT governance. Financial services companies, for example, leverage COBIT to align their IT controls with strict regulatory mandates like Sarbanes-Oxley (SOX), ensuring data integrity and security. Similarly, healthcare organizations apply its principles to safeguard sensitive patient information in compliance with HIPAA, while government agencies use it to enhance transparency and accountability in their IT operations.
The framework’s core is a series of governance and management objectives organized into domains. The risk management process within COBIT involves evaluating risk scenarios, aligning IT risk with enterprise risk, and ensuring that IT-related decisions reflect the organization’s risk tolerance. It creates a clear cascade from stakeholder needs down to specific IT process goals and controls.
Actionable Takeaways
To implement COBIT’s risk management principles effectively, organizations should adopt a structured approach:
- Start with Governance: Establish a clear IT governance structure before diving into specific controls. Engage stakeholders from across the business to define risk appetite and priorities.
- Focus on High-Priority Risks: Use COBIT’s goals cascade to identify the most critical IT processes and risks that impact business objectives. Prioritize these areas for initial implementation.
- Leverage Existing Controls: Don’t reinvent the wheel. Map your existing IT controls and processes to the COBIT framework to identify gaps and areas for improvement, a key part of many effective process improvement techniques.
- Establish Clear Metrics: Define and use clear metrics (Key Goal Indicators and Key Performance Indicators) to monitor the effectiveness of IT risk management activities and report progress to leadership.
Top 7 Risk Management Frameworks Compared
| Framework | Implementation Complexity 🔄 | Resource Requirements 🔄 | Expected Outcomes 📊 | Ideal Use Cases 💡 | Key Advantages ⭐ |
|---|---|---|---|---|---|
| ISO 31000 Risk Management Framework | Moderate to High: Needs customization and leadership commitment | Significant: Organizational training and integration | Improved risk governance and continuous improvement | All types of organizations seeking a flexible risk framework | Internationally recognized, flexible, continuous improvement |
| NIST Cybersecurity Framework | Moderate: Structured but scalable | Moderate: Ongoing maintenance and updates | Enhanced cybersecurity risk management and communication | Organizations managing cybersecurity risks of all sizes | Widely adopted, cost-effective, facilitates cross-team communication |
| COSO Enterprise Risk Management | High: Comprehensive, phased implementation | High: Requires strong leadership and resource investment | Integrated risk management aligned with strategy and culture | Large enterprises needing holistic enterprise risk management | Comprehensive approach, strong governance focus, strategic alignment |
| FAIR (Factor Analysis of Information Risk) | High: Specialized quantitative methodology | High: Data-intensive with expert analysis | Quantitative financial risk metrics for informed decisions | Organizations quantifying cybersecurity risks financially | Quantitative, reduces bias, supports cost-benefit analysis |
| OCTAVE | Moderate to High: Multi-phase internal assessment | Moderate: Requires internal expertise and time | Improved organizational security posture and risk awareness | Organizations emphasizing self-assessment of operational risks | Self-led, focuses on critical assets, cost-effective |
| Basel III Risk Management Framework | High: Complex regulatory compliance | High: Extensive regulatory reporting and system upgrades | Strengthened bank capital and liquidity management | Banks and financial institutions under regulatory mandates | Internationally standardized, enhances financial stability |
| COBIT Risk Management Framework | High: Detailed IT governance and risk management | High: Expertise and ongoing updates needed | Improved IT governance aligned with business objectives | Enterprises focusing on IT governance and regulatory compliance | Comprehensive, integrates IT risk with business goals, widely recognized |
From Framework to Function: Putting Your Risk Strategy into Action
Navigating the landscape of risk management can feel like a monumental task. As we’ve explored, the world of formal risk mitigation is rich with powerful, structured approaches. From the universal principles of ISO 31000 to the cyber-focused precision of the NIST Cybersecurity Framework and the enterprise-wide scope of COSO, each model offers a unique lens through which to view and control uncertainty.
The key takeaway is not that one framework reigns supreme, but that the best framework is the one that aligns with your organization’s specific context, industry, and maturity level. For a tech-driven team, a quantitative model like FAIR might provide the data-centric clarity needed for cybersecurity investments. In contrast, a highly regulated financial institution will naturally gravitate towards the stringent requirements outlined in the Basel III framework. The power lies in understanding these differences and selecting a blueprint that fits.
Synthesizing the Frameworks: Core Principles for Success
Despite their diverse applications, these risk management framework examples share a common DNA. They all champion a proactive, systematic, and integrated approach to handling risk. Instead of reacting to crises, they empower organizations to anticipate, assess, and act decisively.
Here are the universal threads connecting these powerful models:
- Context is King: Every effective framework, from COBIT to OCTAVE, begins with understanding your organization’s unique environment, objectives, and risk appetite. Without this foundational context, any risk management effort is merely a shot in the dark.
- Integration is Non-Negotiable: Risk management cannot be a siloed activity confined to a single department. As COSO and ISO 31000 emphasize, risk must be woven into the fabric of decision-making at all levels, from the C-suite to frontline project teams.
- Continuous Improvement is the Goal: Risk landscapes are dynamic. A successful risk program is not a one-time project but a continuous cycle of identification, analysis, response, and monitoring. This iterative process ensures your strategy remains relevant and effective against emerging threats.
From Blueprint to Reality: Making Risk Management Actionable
Choosing a framework is the first step; bringing it to life is the true challenge. A framework on paper is just theory. Its value is only realized when it is translated into concrete processes and embedded into daily workflows. This is where high-level strategy meets operational reality. For sectors with complex financial instruments and regulatory pressures, applying these frameworks requires specialized knowledge. For practical insights into applying risk management in the financial sector, resources like industry-specific blogs can offer valuable perspectives, such as the Fundpilot Blog.
Ultimately, the most successful risk management strategies are those that are not only comprehensive but also seamlessly integrated into the tools your teams use every day. The goal is to make sound risk practices an automatic, ingrained part of your organizational culture, ensuring resilience and paving the way for sustainable growth.
Ready to turn risk management theory into operational reality? Mitigate the project disruptions caused by unplanned absences by automating handovers directly within Jira. Explore how the Out of Office Assistant from resolution Reichert Network Solutions GmbH can help you embed risk resilience directly into your team’s daily workflows. Learn more and start your free trial today.