Think of your company’s data and systems like a high-security building. Permission-based access control (PBAC) is the smart keycard system that ensures people can only get into the specific rooms and floors they need to do their jobs. No more handing out a master key to everyone.
What Is Permission-Based Access Control?

At its core, permission-based access control is a security approach that limits system access to only authorized users. It’s less like a simple lock and more like a diligent security detail checking credentials at every single door. Instead of giving out broad, sweeping access, it assigns very specific permissions for specific tasks, data, and resources.
This model is built on a fundamental security idea called the principle of least privilege (PoLP). It’s a simple rule: a user should only have the absolute minimum level of access—or permissions—they need to perform their duties. For example, a marketing coordinator needs to create and edit blog posts, but they certainly don’t need to peek at the company’s financial records or have the power to change the website’s source code.
The Foundation of Modern Security
By strictly managing who can do what, permission-based access control acts as your first line of defense in protecting sensitive information. It’s not just about stopping outside attackers; it’s also about minimizing the potential damage from inside threats, whether they’re accidental or intentional. If an employee’s account gets compromised, the damage is contained to only what that specific user could access.
The central idea is powerful in its simplicity: start with zero access, then grant permissions only when absolutely necessary. This “deny by default” mindset is a game-changer, fundamentally strengthening your security by shrinking the potential attack surface.
The growing importance of this approach is clear in market trends. The global access control market was valued at around $10.76 billion in 2024 and is set for major growth. This isn’t surprising, given the rise in security threats and new regulations that demand tighter control over data.
Why It’s Critical for Your Business
Putting a solid permission-based access control system in place is essential for a few key reasons. It directly helps your business by:
- Preventing Data Breaches: By limiting access points, you dramatically cut down the risk of unauthorized data exposure.
- Simplifying Compliance: It creates a clear, auditable trail, which makes meeting standards like GDPR, HIPAA, and SOC 2 much easier.
- Maintaining Operational Integrity: It stops critical systems and data from being accidentally or deliberately changed by people who shouldn’t have access.
Ultimately, a well-defined access strategy is a must for any modern organization. For platforms like Jira that handle critical customer and project data, a robust system isn’t just nice to have—it’s non-negotiable. You can learn more about setting up effective Jira access management in our detailed guide. It’s all about making sure the right people see the right information, protecting both your data and your team’s efficiency.
Exploring Key Access Control Models
Once you’ve grasped the “why” of permission-based access control, the next logical step is digging into the “how.” Not all security systems are built the same. Think about securing a physical building: you could use a simple master key, give everyone individual keys for specific doors, or install high-tech keycards that only work at certain times. Digital access works in a similar way, managed through different models with their own logic and strengths.
The most common models you’ll encounter are Role-Based Access Control (RBAC), Attribute-Based Access Control (ABAC), and Discretionary Access Control (DAC). Getting a handle on these approaches is key to picking the right framework to protect your company’s sensitive data while keeping your teams productive.
Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) is probably the most common and intuitive model out there. It works by assigning permissions to roles instead of to individual users. Picture a typical company with roles like “Marketing Manager,” “Sales Representative,” and “Software Engineer.”
Instead of manually giving every new marketing manager access to the company blog, social media accounts, and analytics dashboard, you just create a “Marketing Manager” role. This role comes pre-loaded with all the necessary permissions. When a new person takes that job, you simply assign them the role, and they instantly have all the access they need. It’s clean and simple.
- How it Works: Permissions are bundled into job functions or roles.
- Analogy: It’s like being issued a “Marketing Team” keycard that opens all the necessary marketing department doors but not the engineering labs.
- Best For: Organizations with clearly defined job titles and stable hierarchies where user responsibilities don’t change frequently.
This model’s popularity is booming. In 2024, the RBAC market size was estimated at around $10.59 billion and is projected to hit $11.78 billion in 2025, all thanks to a global push for better, more manageable security.
The diagram below breaks down the core pieces that make these systems tick, from making policy decisions to enforcing them on the ground.
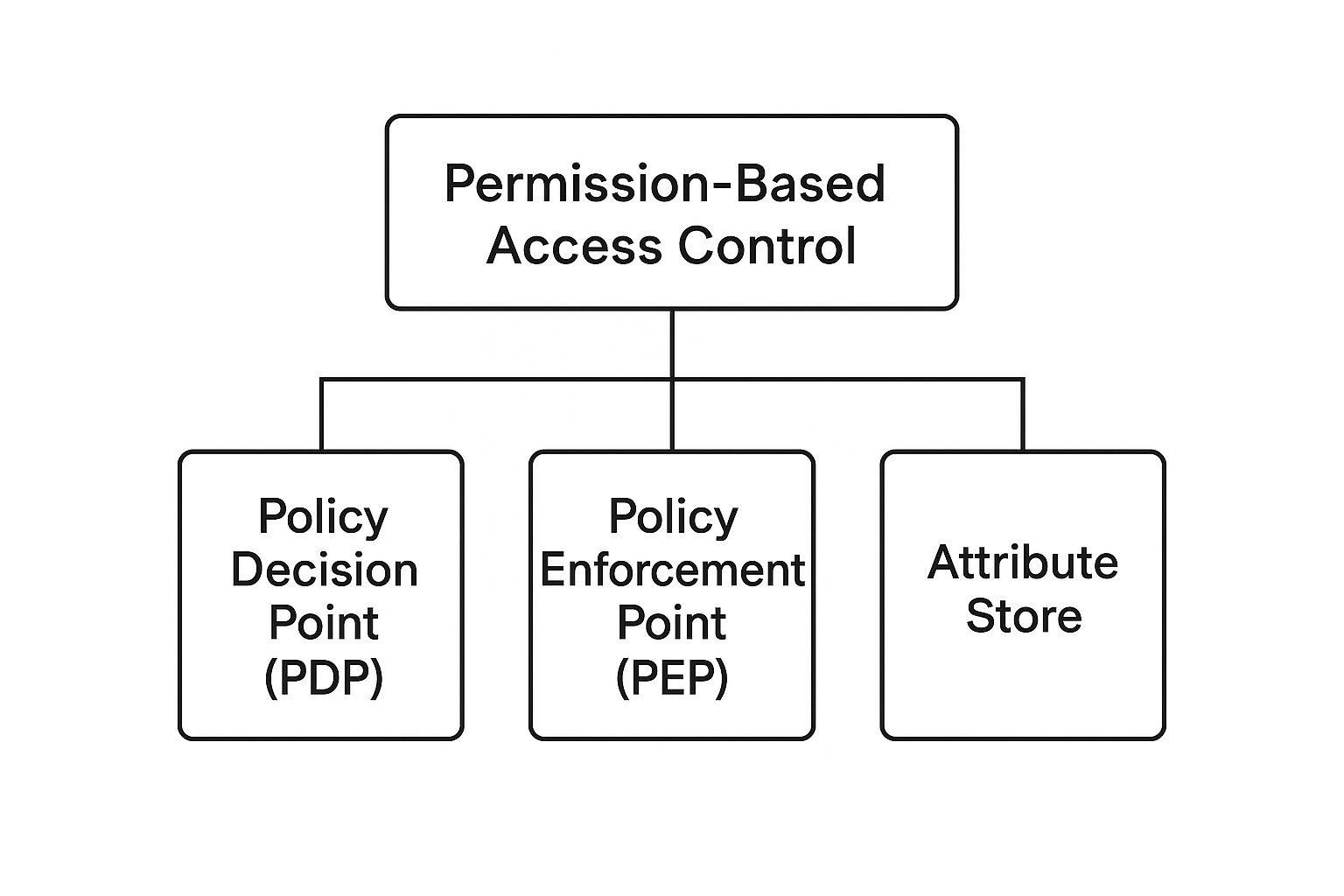
This shows how a central decision point, an enforcement point, and an attribute store all work in concert to manage who gets access to what.
Attribute-Based Access Control (ABAC)
If RBAC is static, then Attribute-Based Access Control (ABAC) is its dynamic, context-aware cousin. It grants or denies access based on a mix of attributes, which are just labels or tags. These attributes can describe the user, the resource they want to access, and the environment itself.
ABAC answers more complex questions than just “What is your role?” It asks, “Who are you, what are you trying to access, where are you, what time is it, and what device are you using?”
For instance, a policy could be set up so that a developer can only access the production database if they are:
- Part of the “Senior Engineering” team (user attribute).
- Accessing from a company-issued laptop (device attribute).
- Working during standard business hours (environment attribute).
If even one of those conditions isn’t met, access is denied. This incredibly granular control makes ABAC a powerhouse for complex, zero-trust security environments. There are many ways to verify these attributes, and some organizations are even exploring things like voice-based caller authentication to add another layer of verification.
Discretionary Access Control (DAC)
Last but not least, we have Discretionary Access Control (DAC). In this model, the owner of a resource gets to decide who can access it. If you create a document or a project board, you have the “discretion” to grant access to your colleagues. It’s the most flexible and user-driven model of the three.
Think about how you share a Google Doc. As the owner, you can invite specific people and assign them permissions like “Viewer,” “Commenter,” or “Editor.” That’s a perfect, real-world example of DAC in action.
While DAC offers fantastic flexibility for collaboration, it can become a real headache to manage at a large scale because there’s no centralized control. It puts a lot of trust in individual users to manage security correctly, which can be a risky bet.
Comparing Access Control Models
To make it easier to see the differences at a glance, here’s a quick comparison of the three models we’ve covered. Each has its place, and the best choice really depends on your organization’s specific needs for security, flexibility, and scale.
| Model | Basis of Control | Granularity | Scalability | Best For |
|---|---|---|---|---|
| Role-Based (RBAC) | User’s job function or role | Coarse | High | Structured organizations with defined roles |
| Attribute-Based (ABAC) | User, environment, and resource attributes | Very fine | High, but complex | Dynamic environments needing context-aware rules |
| Discretionary (DAC) | Resource owner’s discretion | Fine, but user-managed | Low | Small teams and collaborative, flexible projects |
Ultimately, understanding these models helps you move from a one-size-fits-all security mindset to a more tailored approach that truly fits your operational reality.
Why Effective Access Control Is Non-Negotiable
It’s one thing to know the different models of access control, but it’s another to truly grasp their impact on your business. Implementing a solid permission-based access control strategy is so much more than ticking a technical box—it’s a cornerstone for resilience and growth. The positive effects ripple out across your security, compliance, and even day-to-day operations.
Let’s move past the theory. The real-world results are what make robust access control an absolute must for any modern company. Here’s a breakdown of the most critical advantages you’ll see.
Drastically Improving Security
The most immediate benefit is a huge upgrade to your security posture. When you stick to the principle of least privilege, you naturally shrink your digital attack surface. Each person only has access to the data and systems they absolutely need for their job.
What does this mean in practice? It means a compromised account has a very limited blast radius. Instead of an attacker getting a master key to your entire digital kingdom, they get a key that only opens one, low-value room. This containment is everything. It can turn a potential company-wide disaster into a manageable, isolated incident, giving your security team the crucial time they need to respond.
A well-implemented permission based access control system acts like a series of internal fire doors. Even if one area is breached, the fire is contained and can’t spread through the rest of the building, protecting your most valuable assets.
Achieving Seamless Regulatory Compliance
Meeting standards like GDPR, HIPAA, or SOC 2 is a major headache for many businesses. A solid access control framework is the backbone of any compliance effort. It gives you a clear, automated, and auditable trail of who can access what, when, and why.
When the auditors arrive, you can instantly show that you have strong controls protecting sensitive data. This structured approach takes the pain out of the audit process, saving countless hours and lowering the risk of expensive non-compliance penalties. It turns compliance from a frantic, manual scramble into a predictable, system-driven process.
Boosting Operational Efficiency
Let’s be honest: manually managing user permissions is a tedious and error-prone job for IT admins. Onboarding a new hire or changing someone’s role can unleash a flood of access requests. A permission-based access control system, particularly a role-based one (RBAC), automates a huge chunk of this work.
This automation frees up your technical teams to work on more strategic projects instead of getting stuck in the weeds of repetitive tasks. The market certainly sees the value here; the global access control market is projected to grow from $12.8 billion in 2024 to over $13.72 billion in 2025, with strong growth expected to continue.
Simplifying System Administration
Centralizing control just makes everything simpler. Instead of wrestling with a tangled web of individual permissions spread across dozens of different apps, you get a single, unified view. This clarity makes it much easier to update policies, run security reviews, and keep things consistent across the board.
This simplified approach also cuts down on human error, like forgetting to revoke someone’s access when they leave the company. A clear, central dashboard also leads to better decision-making by providing accurate data on who is accessing what. This insight is a key part of improving data-driven decision making throughout your organization.
Implementing Your Access Control Strategy
Moving from theory to practice is where any security plan really shows its teeth. A successful permission-based access control rollout isn’t just a matter of flipping a switch on some new software. It’s a deliberate process of auditing, defining, and continuously refining who gets the keys to what in your organization.
Here’s a roadmap to help you turn your access control model into a secure, functional reality.
The first move, always, is to take stock. You have to conduct a full audit of every existing permission across your apps, servers, and databases. Who has access to what right now, and why? This initial deep dive often uncovers some real surprises—unnecessary access rights that have piled up over the years.
This audit gives you a clear map of where you stand. From that baseline, you can start the real work: defining user roles based on what people actually do, not just their job titles.
Defining Roles And Enforcing Least Privilege
With your audit done, it’s time to define roles logically. Let’s imagine a company, “Innovate Inc.,” as they get this sorted. Their marketing team, for example, had members with sweeping access to customer data in their CRM, far more than they needed for running campaigns.
To sort this out, Innovate Inc. created specific roles like “Content Creator,” “Campaign Manager,” and “Marketing Analyst.” Each role was given only the permissions needed for that specific job. A Content Creator could write and publish blog posts but couldn’t export the entire customer list—that was a job for the Campaign Manager.
This gets to the heart of a core security principle:
Default to zero access, then grant what’s necessary. This approach, the principle of least privilege, is the bedrock of a strong permission-based access control system. It makes sure no user or system has more access than is absolutely essential to do their job.
You see these principles pop up in all kinds of IT management. Take network access, for instance. It’s the same logic you’d use when securely setting up guest WiFi. You create a separate, isolated network with strictly limited permissions for visitors, keeping them completely walled off from your internal company network.
Building A Process For Access And Reviews
Once you have your roles defined, the next piece of the puzzle is creating a formal, easy-to-follow process for access requests. When someone changes jobs or a new person joins the team, there should be a clear workflow for requesting, approving, and setting up the right permissions.
This process has to be:
- Transparent: Everyone should know how to ask for access and who signs off on it.
- Efficient: The workflow needs to be quick. If it’s slow, people will be tempted to find workarounds, defeating the whole purpose.
- Auditable: Every request, approval, and change has to be logged. This creates a clear paper trail for security reviews and audits.
This brings us to the final, and maybe most critical, step: keeping it all up to date. A permission-based access control system is not a “set it and forget it” tool.
Regular reviews are non-negotiable. You should plan for quarterly or semi-annual permission audits to make sure access rights still line up with current roles and responsibilities. These check-ins are vital for a few key reasons:
- Removing Orphaned Accounts: Finding and shutting down accounts for people who no longer work there.
- Correcting Permission Creep: Reversing the slow, gradual build-up of unneeded permissions as people move between roles.
- Ensuring Compliance: Showing auditors that you have a tight, disciplined grip on who can access your data.
By following this implementation roadmap—auditing what you have, defining tight roles, enforcing least privilege, and scheduling regular reviews—you build a resilient and effective security framework. It protects your data while still letting your team get their work done.
Connecting Permissions Between HubSpot And Jira

Theory is one thing, but the real test of a permission based access control strategy is how it holds up in the real world. A classic challenge for just about any growing company is bridging the gap between their sales and development teams—which usually means connecting HubSpot and Jira.
This integration is a fantastic way to get teams talking and work flowing, but it also opens up a new can of worms when it comes to security. How do you give your sales team visibility into customer-reported bugs without letting them wander through sensitive engineering discussions or the entire technical backlog? This is exactly where a smart access control setup becomes critical.
It’s all about creating a smooth channel for information to flow while making absolutely sure the right people see the right things, and only at the right time.
Mapping Roles Across Platforms
At its heart, a secure HubSpot-Jira integration is all about mapping user roles from one system to the other. You’re not just connecting two apps; you’re connecting two different teams with completely different jobs and clearance levels. The whole point is to apply the principle of least privilege across both platforms, so everyone has just enough access to do their job, and no more.
For example, a sales rep in HubSpot should absolutely be able to create a Jira ticket straight from a customer’s contact record when they report a bug. That’s essential for quick customer service. But does that same rep need to see the entire engineering project, read internal developer comments, or mess with sprint timelines? Of course not.
To pull this off, you have to configure the integration to respect role-based permissions:
- Sales Role (in HubSpot): Can create Jira issues from HubSpot contacts, companies, or deals. They can see the status of tickets they created, but that’s where their Jira access ends.
- Support Role (in HubSpot): Similar to sales, they can create and view tickets. Maybe they get slightly more permission, like adding public comments to keep the customer in the loop.
- Developer Role (in Jira): Gets full edit access to the Jira issue, including all the technical fields and internal chatter. They can view the linked HubSpot contact details but can’t edit them.
- Project Manager Role (in Jira): Can see linked HubSpot data and manage the Jira project, but has no power to change the original HubSpot deal or contact info.
This kind of careful mapping is what lets the integration empower your teams without accidentally swinging the doors wide open to security risks.
Solving Common Integration Hurdles
Let’s be honest: connecting two powerhouse systems like HubSpot and Jira is rarely a simple plug-and-play affair. You’re bound to hit a few common bumps in the road that a solid permission based access control plan can help you navigate.
One you’ll see often is permission conflict. This is when a user’s permissions in HubSpot crash into their lack of permissions in Jira. Say a sales manager tries to assign a new ticket to a specific developer but doesn’t have the “Assign Issues” permission in that Jira project. The action will simply fail, causing confusion and delays.
Another headache is data synchronization errors. These can pop up if the integration tries to sync a field that one user can see but the other can’t. This messes up your data and undermines the whole “single source of truth” you were trying to build in the first place.
Overcoming these problems means being incredibly meticulous during setup. The HubSpot for Jira integration app, for instance, gives you a starting point to link accounts and define exactly what information gets passed between them.

This is where you begin to build that permissions-aware bridge, customizing which HubSpot objects even show up in Jira to begin with.
A successful integration hinges on treating it not as a data pipe, but as a guarded bridge. Every piece of information that crosses must be checked against the permissions of the user and the role on both sides.
A Step-By-Step Guide To Secure Integration
Getting to this secure and efficient workflow isn’t magic; it just takes a structured approach. Here’s a quick guide to get you started on the right foot:
- Audit Existing Permissions: Before you connect anything, take a hard look at the current permission setups in both HubSpot and Jira. Know who can do what in each system on its own.
- Define Integration Goals: Write down exactly what you want this connection to do. Be specific, like, “Enable support agents to create bug reports in Jira directly from a HubSpot ticket.”
- Configure Role Mapping: Use an integration tool to map roles between the systems. It’s often a good idea to create a specific “HubSpot Integration User” in Jira with very limited permissions to act as the go-between.
- Set Up Field-Level Security: Decide which HubSpot fields will be visible in Jira. You’ll want to hide sensitive information like deal values or private contact notes from your technical teams.
- Test Extensively: This is non-negotiable. Create test users for your different roles (a dummy sales rep, a test developer, etc.) and run through every single workflow you designed. Find and fix permission conflicts now, not after you go live.
- Monitor and Review: An integration isn’t a “set it and forget it” project. You need to review it regularly. Check the logs and audit the permissions at least quarterly to make sure they still make sense for your business and security policies.
By following these steps, you can build a powerful, seamless workflow that genuinely improves how your sales, support, and development teams work together. For a closer look at how this pays off, you can learn more about how a HubSpot-Jira integration benefits support teams and ultimately boosts customer satisfaction. It’s the difference between an integration that’s a productivity multiplier and one that’s a security liability.
Where Digital Access Control Is Headed
The world of access control is always changing. New tech pops up, and security threats get smarter. While the core ideas of permission-based access control are as solid as ever, how we apply them is definitely evolving. Looking at the horizon, a few key trends are getting ready to shake up how we all manage and secure digital access.
The biggest game-changer is without a doubt Artificial Intelligence (AI) and Machine Learning (ML). These aren’t just buzzwords; they’re the brains behind a new breed of adaptive access control systems. Instead of old-school, static roles that you set and forget, these smart systems watch user behavior as it happens. If someone suddenly tries to grab files at 3 AM or from a new country, the system can flag it or even pull their access right then and there. It stops a potential disaster before it even starts.
Zero Trust and Decentralized Identity
This real-time, adaptive thinking slots perfectly into the Zero Trust Architecture (ZTA) security model. The central idea of Zero Trust is simple but powerful: “never trust, always verify.” It works on the assumption that a threat could be anywhere—inside or outside your network—so it demands strict verification for every single request to access anything. Permission-based access control isn’t just a part of this; it’s the absolute foundation that makes a Zero Trust framework possible by providing the fine-grained controls needed to enforce those tough verification policies.
In a Zero Trust world, access isn’t a permanent key to the city. It’s a continuous, dynamic process where permissions are constantly checked against what’s happening right now—user behavior, context, and potential risks.
Beyond AI, other technologies are also stepping onto the stage. Biometric authentication—think fingerprints, facial recognition, or even how you type—is becoming a go-to for adding a tough layer of identity verification. This makes it a whole lot harder for the wrong person to get in, even if they’ve swiped a password.
We’re also seeing some fresh thinking about identity itself, powered by technologies like blockchain. Here are a few trends you’ll want to keep an eye on:
- Decentralized Identity: Blockchain could let users actually own and control their digital identities. Instead of a central company holding all the keys, you’d share only the credentials you need to, when you need to.
- IoT Security: More and more devices, from sensors to smart appliances, are hooking into company networks. Each one is a potential backdoor that needs to be secured, making sophisticated permission controls for them a top priority.
- Context-Aware Access: Systems will get much smarter about using a whole cocktail of signals—like your location, the time of day, and the health of your device—to make better, more secure access decisions on the fly.
All these signs point in one clear direction. Access control is ditching rigid, static rules for a model that’s more intelligent, dynamic, and aware of the world around it. For any organization that wants to stay ahead of the security curve, getting on board with these trends is going to be crucial for protecting the stuff that matters.
Got Questions About Access Control? We’ve Got Answers.
As you start dialing in your security, it’s only natural for questions to pop up. To help you out, we’ve put together some straightforward answers to the questions we hear most often about permission-based access control. Think of this as a quick-reference guide to clear up any lingering confusion and help you make smarter implementation choices.
Getting these details right is the key to building a security framework that’s tough on threats but easy for your team to live with.
What’s the Real Difference Between RBAC and ABAC?
The core difference between Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) really boils down to static versus dynamic rules.
Imagine RBAC as giving out keys based on a job title—it’s pretty fixed. For example, everyone with the “Accountant” role gets access to the company’s financial software. Simple and effective.
ABAC, on the other hand, is a lot smarter and more flexible. It looks at a whole bunch of contextual clues—like the user’s location, the time of day, or the device they’re using—to make access decisions on the fly. It doesn’t just ask, “What’s your role?” but more like, “Are you trying to open this highly sensitive file from a trusted company network during normal business hours?” This allows for security policies that are far more precise and can react to situations in real time.
How Often Should We Be Reviewing User Permissions?
To keep your security in top shape, you should plan on doing a full review of user permissions every quarter. If that’s too much, at least aim for twice a year. This regular check-up helps you fight “permission creep,” which is what happens when people gradually collect access rights they no longer need.
A change in an employee’s role is your cue for an immediate review. This means promotions, moves to another department, or when someone leaves the company. One of the easiest security mistakes to avoid is failing to remove access right away.
These audits aren’t just a good idea; they’re often a must-have for meeting compliance standards and stopping unauthorized data access before it happens.
Is Access Control Really Necessary for a Small Business?
Yes, absolutely. It’s a dangerous myth that small businesses can skip this. Even the smallest company deals with sensitive information, whether it’s customer lists, employee files, or your own financial data. A data breach can be just as devastating for a small shop as it is for a giant corporation.
Putting a basic permission-based access control system in place from the start is much easier and cheaper than trying to bolt on security after you’ve already grown. Kicking things off with a simple role-based model protects your most important assets from day one. More importantly, it builds a security-first mindset into your company’s DNA, creating a culture that scales right along with your business. It’s one of the best early investments you can make in your company’s future and reputation.
Bridge the gap between your sales, support, and development teams with resolution Reichert Network Solutions GmbH. Seamlessly integrate HubSpot and Jira to provide your teams with the customer context they need, right where they work. Eliminate data silos, improve collaboration, and resolve customer issues faster by connecting your most critical platforms. Learn more and get started with HubSpot for Jira today.
