Ever heard the saying, “just in time”? In the world of IT and user access, this isn’t just a catchy phrase—it’s a powerful strategy.
Think of it like this: you give a new employee a hotel key card, but instead of activating it beforehand, the card only becomes active the very first time they tap it on their room door. That’s the essence of just in time (JIT) provisioning. It’s a method that automatically creates a user’s account in an application the moment they try to log in for the first time, not a second sooner.
What Is Just In Time Provisioning, Really?

In the old days—and for some, still today—IT teams would spend hours manually creating accounts for every new hire in every single app they might need. This wasn’t just slow; it was a recipe for mistakes and created massive security holes with dormant, unused accounts just sitting there.
Just in time provisioning completely flips that script. Forget creating accounts “just in case.” With JIT, they’re created “just in time.”
Here’s how it works in practice: a new team member clicks to log into an app, usually through a Single Sign-On (SSO) portal. The system quickly checks if they have an account. If the answer is no, JIT instantly spins one up on the fly, pulling the necessary details from the company’s identity provider (like Azure AD or Okta). For IT teams, this on-demand process is a breath of fresh air.
The Shift From Manual To Automated
Moving to JIT is more than just a workflow tweak; it’s a fundamental shift toward better efficiency and tighter security. It completely removes the headache of manual setups and guarantees that people get access to the tools they need to do their jobs from day one. No more waiting around for an IT ticket to clear.
At its core, JIT provisioning embodies the principle of least privilege. By creating accounts only when they’re actually needed, you shrink your organization’s attack surface by getting rid of all those “ghost accounts” that often linger long after someone has left the company or changed roles.
This automation is what’s fueling some serious market growth. The global user provisioning market was valued at $4.3 billion in 2021 and is on track to hit $15 billion by 2031, a surge driven by the need for faster, more secure onboarding.
JIT vs. Traditional Provisioning
To really see the difference, it helps to put the two methods side-by-side. Traditional provisioning is reactive and incredibly labor-intensive. JIT is proactive and almost entirely automated.
We’ve put together a quick comparison table to highlight the main differences. And if you want to go even deeper into the full spectrum of user account management, you can master user provisioning and deprovisioning with our detailed guide.
JIT Provisioning vs Traditional Provisioning At a Glance
This table gives you a quick rundown of how Just In Time provisioning stacks up against the old-school, manual approach.
| Feature | Just In Time (JIT) Provisioning | Traditional Provisioning |
|---|---|---|
| Account Creation | Automated on first login | Manual, pre-created by IT |
| User Experience | Instant, seamless access | Delayed access, requires IT ticket |
| Security | Reduces dormant accounts | Creates dormant account risks |
| IT Workload | Minimal, setup-focused | High, requires constant manual work |
As you can see, the benefits go far beyond just saving time. JIT creates a smoother, more secure experience for everyone involved, from the end-user to the IT admin.
How JIT Provisioning Works Under the Hood
To really get what just-in-time provisioning is all about, we need to look past the high-level concept and get our hands dirty with the mechanics. It’s not magic; it’s more like a beautifully coordinated digital handshake that happens in the blink of an eye.
Let’s imagine a new hire in marketing, Alex, who needs access to Jira on their first day. The old way involved waiting for an IT ticket to get processed. With JIT, Alex just heads over to the company’s single sign-on (SSO) portal and clicks the Jira icon. That single click sets a secure, automated process in motion.
The SSO portal, which acts as the identity provider (IdP)—think Okta or Azure AD—takes Alex’s verified identity information (name, email, department) and bundles it into a secure digital envelope. This is usually done with a protocol like Security Assertion Markup Language (SAML), the industry standard for these kinds of identity handshakes.
The Digital Handshake
The IdP then sends this SAML assertion over to Jira, which is the service provider in this scenario. Jira receives the package, opens it, and checks the trusted information inside. It then asks a simple but critical question: “Do I already have an account for alex@company.com?”
Since it’s Alex’s very first time logging in, the answer is no. This is the moment where the “just-in-time” part really shines.
Based on the trusted data from the IdP, Jira instantly creates a new user account for Alex. It doesn’t just create a blank slate; it populates the profile with the name, email, and other attributes passed in the SAML assertion, making the account ready for immediate use.
This whole process guarantees that access is granted precisely when it’s first needed. This completely sidesteps the security risk that comes with pre-provisioned, dormant accounts just sitting there. Of course, this is often paired with other security layers, and many organizations learn more about secure Multi-Factor Authentication (MFA) methods to make access controls even tougher.
From Request to Delivery
We can break the entire workflow down into a simple three-act play: a request is triggered, resources are allocated, and access is delivered instantly.
This infographic gives a great visual of the core process, showing how a user’s request seamlessly kicks off the automated allocation and delivery.
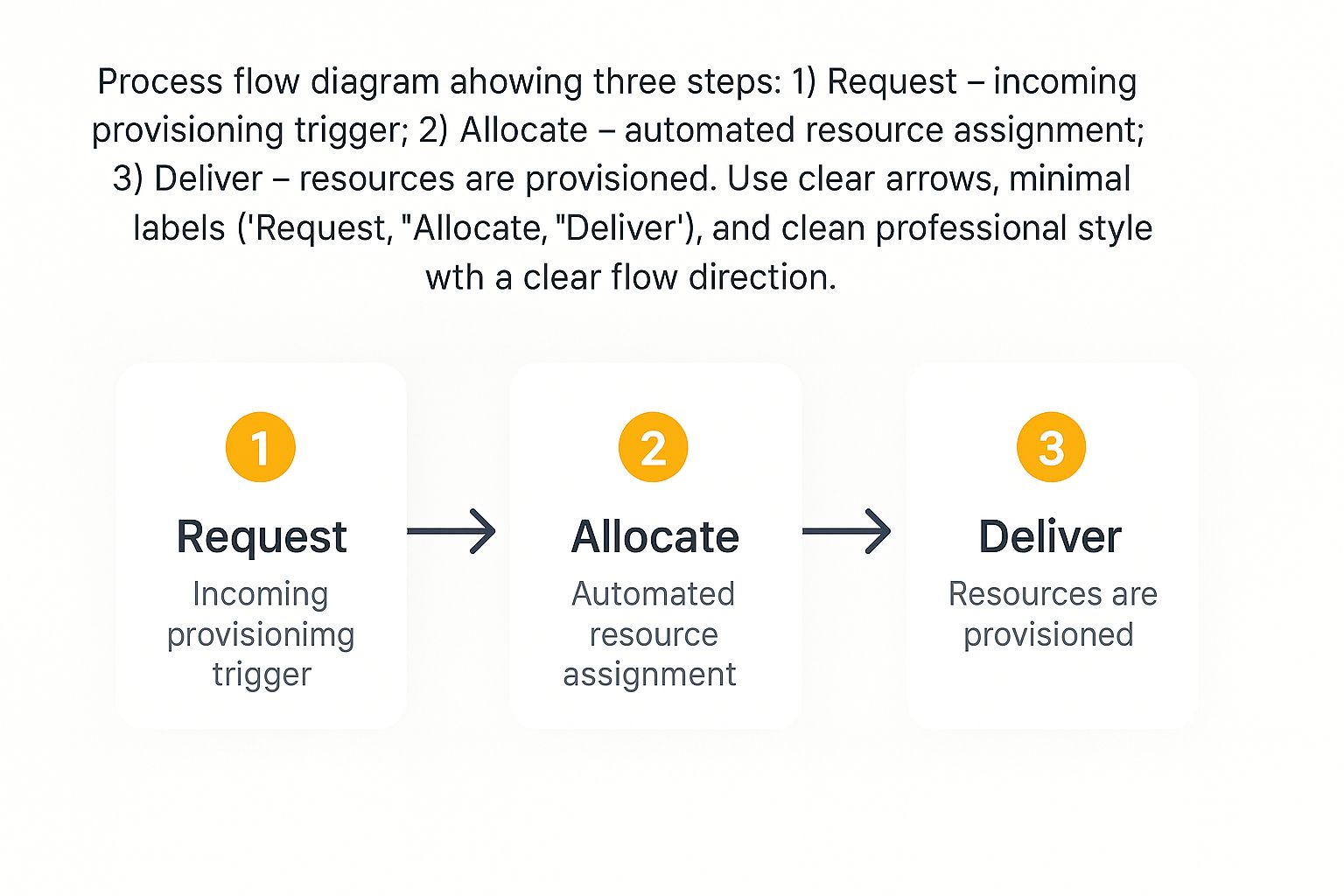
You can see how efficient the JIT model is—each step just flows into the next without anyone having to lift a finger.
The final, crucial step is getting the permissions right. The SAML assertion often carries group membership information (like “Marketing Team”). Using this data, the system can automatically:
- Assign the right user role in Jira, so Alex has the correct permissions from the get-go.
- Grant access to specific Jira projects or Confluence spaces that the marketing team uses.
For Atlassian admins, this is a massive win. The principles of JIT can be pushed even further, and you can see how by checking out our guide to Jira Cloud automation. In just a few seconds, Alex goes from having no account at all to being a fully provisioned, productive member of the team—all without a single manual touch from IT.
The Business Case for Adopting JIT

Let’s be honest, just-in-time provisioning is about much more than just making life easier for your IT team. It’s a strategic decision that tightens your security, makes your operations run smoother, and has a real impact on your bottom line. It all boils down to a fundamental shift in mindset: moving from “just in case” access to “just when needed.”
This change alone can transform your security posture. Think about it. Traditional provisioning methods almost always leave behind a trail of “ghost” accounts from old projects or former employees. These dormant accounts are a goldmine for attackers, creating risks you don’t even know you have. JIT basically erases this threat by making sure accounts only exist when there’s an active user tied to them.
Enhancing Operational and Financial Health
Beyond the security wins, the day-to-day operational gains are huge. When you automate account creation, you’re freeing up your IT folks from the mind-numbing task of manually setting up every new user. Instead of being buried under a mountain of support tickets, they can finally work on projects that actually move the business forward.
It’s no surprise that the market is exploding.
The global user provisioning market, which includes JIT solutions, was valued at $10.2 billion in 2024 and is expected to hit $35.22 billion by 2031. This isn’t just hype; it shows a massive industry-wide move toward automation to cut down on identity-related risks.
And yes, this automation leads to real cost savings. By creating accounts only when someone logs in for the first time, you guarantee you’re only paying for software licenses that people are actually using. No more over-provisioning or wasting money on shelfware, which is a lifesaver for large organizations or teams that scale up and down.
While JIT is perfect for individual users, if you’re tackling large-scale changes, you might find some useful strategies in our guide on bulk user administration in Atlassian.
Improving the Employee Experience
Finally, let’s talk about the user experience, because it matters. When a new hire can log in and get instant access to Jira and Confluence on day one, it sets a completely different tone. No more frustrating delays or waiting around for permissions to be granted. They can just get to work.
This is especially critical for businesses with a dynamic workforce, like:
- Seasonal Staff: A retailer can get hundreds of temporary holiday workers up and running instantly, without creating security headaches that linger long after they’re gone.
- Freelancers and Contractors: A freelance developer can log in and immediately get the project-specific access they need, which is then automatically revoked when their work is done.
The power of this kind of automation goes way beyond just user accounts. If you’re curious about how these ideas can be applied elsewhere, you should check out these various business process automation examples. At the end of the day, JIT isn’t just a feature—it’s a much smarter way to manage access and run your business.
Choosing the Right Provisioning Method
Figuring out the best way to manage user access can feel like navigating a minefield of acronyms. You’ve got terms like just-in-time provisioning and SCIM floating around, and it’s easy to get them mixed up. The first thing to know is that they aren’t competitors. In fact, they’re powerful collaborators that solve different parts of the same puzzle.
Let’s try an analogy. Think of it like getting access to a new office building.
Just-in-time (JIT) provisioning is the person at the front desk who prints your ID badge the very first time you show up. It’s a one-time event triggered by your first attempt to log in. JIT is all about creating that account on demand, making sure no one gets access until the exact moment they need it.
SCIM, or the System for Cross-domain Identity Management, is the building’s automated management system. After you have your badge, SCIM is what keeps your access rights updated. It’s a protocol—a constant, automated conversation—that handles the ongoing sync of your user data.
JIT and SCIM: Better Together
So, what happens when you move from the Sales department to Marketing? That’s where SCIM steps in. It automatically updates your profile, changes your group memberships, and adjusts your permissions across all connected apps. It ensures your identity and access rights stay consistent everywhere, without anyone lifting a finger.
JIT and SCIM are a perfect pair. JIT creates the account on first login, and SCIM takes over from there, managing all future updates, changes, and eventual deprovisioning. Together, they create a seamless, automated user lifecycle.
This tag-team approach is a world away from the old-school, manual methods that many organizations are still stuck with. Those traditional approaches are slow, clunky, and introduce security risks that modern businesses simply can’t afford.
Let’s break down how these different strategies really compare.
Comparison of User Provisioning Methods
To make the right call for your organization, you need a clear-eyed view of how each method performs when it comes to speed, security, and scalability. While not every company needs a top-tier automated setup, understanding the trade-offs is crucial for building an identity framework that’s both efficient and secure.
Here’s a quick rundown of how JIT, SCIM, and manual processes stack up.
| Criteria | JIT Provisioning | SCIM Provisioning | Manual Provisioning |
|---|---|---|---|
| Speed & Onboarding | Instant. Account created on first login, providing immediate access. | Fast. Automates updates and deprovisioning in near real-time. | Slow. Relies entirely on IT ticket queues and manual data entry, causing major delays. |
| Security | High. Eliminates dormant accounts by creating them only when needed. | Very High. Continuously syncs user status, quickly revoking access for leavers. | Low. Prone to human error, forgotten accounts, and “privilege creep.” |
| Scalability | Excellent. Scales effortlessly with user growth without increasing IT workload. | Excellent. Designed for managing large, dynamic user bases across many apps. | Poor. Becomes unmanageable and error-prone as the organization grows. |
| Maintenance Effort | Low. It’s a “set it and forget it” solution after the initial configuration with your IdP. | Low. Requires some initial setup but runs automatically afterward. | Very High. Demands constant, repetitive manual effort from the IT team. |
Ultimately, the goal is to get away from high-effort, low-security manual work. A bulk upload might feel like a quick fix, but it’s a static snapshot that can’t handle the dynamic, real-time changes of a modern workforce.
For most organizations, a strategy that combines just-in-time provisioning with SCIM offers the best of all worlds: speed, security, and scalability without the administrative headache.
Activating JIT in Your Atlassian Environment
So, you’re sold on the idea of just in time provisioning and want to get it running in your Atlassian tools like Jira and Confluence. The good news is that it’s a pretty straightforward process that starts paying you back in saved time almost immediately. The whole idea is to let your single sign-on (SSO) provider do the heavy lifting. Instead of you or your team manually creating accounts, you simply configure your system to do it automatically the first time a user successfully logs in.
The magic starts inside your identity provider (IdP), whether that’s Azure AD, Okta, or another service. You’ll find settings there to enable JIT for your connected Atlassian application. In plain English, you’re telling your IdP, “Hey, when a new user from our company logs into Jira for the first time, send their details over so an account can be created for them on the fly.”
Essential Configuration Steps
Before you flip the switch, there are a few things you need to have in place to make sure everything goes smoothly. First and foremost, you must have Atlassian Access and a properly configured SAML single sign-on integration. Think of this integration as the secure handshake that lets your IdP and Atlassian Cloud trust each other.
Once your SSO is solid, the main steps are:
- Enabling JIT: This is usually a simple checkbox in your identity provider’s settings for the Atlassian app.
- Attribute Mapping: This is critical. You have to tell your IdP which of its user details (like first name, last name, and email) should go into the corresponding fields in Atlassian. Get this right, and user profiles will be perfectly populated.
- Setting Default Groups: A game-changing step is to define default groups. This automatically assigns new users to the right product access groups—like
jira-usersorconfluence-users—from their very first login. No more manual group assignments.
The screenshot above, pulled from Atlassian’s own documentation, shows exactly where you’d handle these settings in your admin panel. You can see the options to assign users to specific product roles and groups automatically—that’s the key to automating access. For those looking to go even deeper, combining Okta API with SAML for Atlassian provides an advanced look at how these workflows can be customized.
JIT for Dynamic Workforces
This automated approach is a lifesaver for companies dealing with rapid growth or high user turnover. We’ve seen it work wonders in sectors like logistics and retail, where JIT is used to onboard thousands of drivers or seasonal staff, cutting setup time from days down to minutes. When your workforce can swell by over 50% during peak seasons, this kind of immediate, secure access isn’t a luxury; it’s a necessity.
For admins managing a complex Atlassian ecosystem, understanding advanced analytics on user roles within platforms like Confluence can offer even more insight. By setting up just in time provisioning correctly, you can build a self-managing system that’s secure, efficient, and perfectly scaled to whatever your organization throws at it.
Common Questions About JIT Provisioning
As folks start digging into just-in-time provisioning, a few questions pop up almost every single time. The core idea of creating an account right when it’s needed is simple enough, but things can get a little fuzzy when you think about how it fits with other identity tools or what it means for security.
Let’s walk through the three most common sticking points and clear them up. Once we’re done, you’ll have the confidence to talk about and implement JIT like a pro.
What Is the Real Difference Between JIT and SCIM?
This is easily the biggest point of confusion. It’s common to see just-in-time provisioning and SCIM (System for Cross-domain Identity Management) as competitors, but they’re not. They’re collaborators, each solving a different piece of the user lifecycle puzzle.
Here’s a simple way to think about it:
- JIT is the “when.” It’s a one-time event that triggers at the moment of a user’s very first login. Its only job is to create a brand-new user account, right on demand. JIT is the doorman letting you into the building for the first time.
- SCIM is the “how” and “what happens next.” It’s a protocol—a continuous, automated chat between your identity provider and your apps. Once JIT has opened the door, SCIM takes over the heavy lifting. It handles all future updates like name changes, new roles, or group shuffles. Crucially, it also handles deprovisioning when a user leaves.
You can absolutely use JIT without SCIM, but your user data will quickly get stale. You could also use SCIM without JIT, but then you lose that awesome on-demand creation. Use them together, and you get a complete, automated system for managing the entire user lifecycle.
Does JIT Handle Deprovisioning?
Nope. This is a critical distinction to make. Just-in-time provisioning is built for a single, focused task: creation. It springs into action when a user first signs in, but it has no way to do anything when that user leaves the company or just doesn’t need access anymore. It’s a one-way street.
This is precisely why a tool like SCIM or another automated deprovisioning process is non-negotiable.
Think about it: when an employee is terminated in your main directory (like Azure AD), you need a process that instantly revokes their access to downstream apps like Jira and Confluence. Without that automated offboarding, you’re stuck with active, orphaned accounts—the exact security hole JIT helps you plug on the front end.
Relying on JIT for the entire lifecycle is like putting a state-of-the-art lock on your door but never changing the code after someone moves out. For a great look at how large companies tackle these exact processes, checking out how they’re provisioning Confluence users at scale can offer some really practical insights.
Is JIT Secure Enough for Sensitive Applications?
Yes, but with an important condition: it has to be implemented correctly as part of a wider security strategy. The security of JIT doesn’t actually come from the protocol itself. Instead, it piggybacks on the security of the identity provider (IdP) it’s connected to. JIT is designed to simply trust the identity information it receives through a secure assertion, like SAML.
So, the security of your JIT setup is only as strong as your SSO and IdP security. To make it bulletproof for your most critical apps, you have to lock down the source with measures like:
- Multi-Factor Authentication (MFA): Demanding a second form of proof before your IdP gives the green light.
- Strong Password Policies: Enforcing passwords that aren’t easy to guess and are updated regularly.
- Contextual Access Policies: Using rules that check for risk based on where a user is, what device they’re on, or what network they’re using before letting them in.
When you ensure your IdP is rock-solid, you can trust that just-in-time provisioning will only create accounts for legitimate, fully authenticated users. That makes it a powerfully secure and efficient method for even your most sensitive systems.
Are you paying for Atlassian licenses that nobody is even using? With resolution’s User Deactivator, you can automatically identify and disable inactive users in Jira, Confluence, and Bitbucket, ensuring you only pay for the seats you need. Stop wasting money on unused licenses and keep your user directory clean and secure. Learn how User Deactivator can optimize your license costs today.
